At a minor overt halfway via 2023, credential theft is continue to a significant thorn in the facet of IT groups. The heart of the challenge is the worth of information to cybercriminals and the evolution of the techniques they use to get maintain of it. The 2023 Verizon Information Breach Investigations Report (DBIR) revealed that 83% of breaches included exterior actors, with almost all attacks being monetarily inspired. Of these breaches by external actors, 49% involved the use of stolen qualifications.
We will investigate why credential theft is even now these types of an interesting (and productive) attack route, and glance at how IT security groups can battle back in the 2nd half of 2023 and over and above.
Buyers are continue to frequently the weak website link
The hallmarks of quite a few profitable cyberattacks are the determination, inventiveness, and endurance danger actors display. Although a person may location some assaults by security and recognition instruction, it only takes a single very well-crafted attack to capture them. From time to time all it requires is for a user to be dashing or stressed. Risk actors craft bogus login webpages, falsified invoices (these types of as in enterprise email compromise attacks), and redirect email exchanges to trick the close-person into supplying up credentials or cash.
Verizon’s DBIR pointed out that 74% of breaches include things like the human element, both by human mistake, privilege misuse, social engineering, or stolen credentials. A single attention-grabbing info position was that 50% of all social engineering assaults in 2022 utilized a strategy known as ‘pretexting’ – an invented state of affairs that methods a user into offering up their qualifications or doing yet another valuable motion to the attacker. This shows that attackers know people are often the weak url, and they’re fully commited to utilizing social engineering to get their arms on qualifications. It’s generally an easier route into an organization than hacking a complex element of an IT process.
Breaching a process by way of stolen qualifications
Massive companies with substantial security budgets are not immune to cyberattacks – even these doing work the cybersecurity marketplace. Norton Lifelock Password Supervisor gives a modern circumstance study into the lengths attackers will go to in order to get maintain of passwords. As mentioned by the state of Maine’s Legal professional Standard, Norton notified just about 6,500 consumers early in 2023 that their details may have been compromised. Through a brute-power attack employing stolen qualifications, attackers ultimately discovered performing passwords and quickly proceeded to log into client accounts, likely accessing stored customer secrets.
Despite Norton IT alerting on a significant quantity of failed logins and using speedy action, Norton Lifelock Password Manager consumers were being continue to compromised. This underlines the risk that stolen qualifications participate in in attacks. No make a difference the power of a company’s security, a password stolen from an additional fewer-safeguarded firm is difficult to protect against from reuse.
As the Verizon report confirmed, approximately 50 percent (49%) of very last year’s breaches stemmed from stolen qualifications. So where by are attackers acquiring these breached credentials? And how can you explain to if your end users have compromised passwords out there too?
Finding stolen secrets in black markets
Like evolved black markets of previous, on the internet black markets peddling stolen qualifications are increasingly popular. Enormous datasets consisting of hundreds of hundreds of stolen qualifications are out there for sale though costing peanuts up coming to the possible payoff a effective ransomware or BEC attack could have. These lists are particularly worthwhile for non-technological attackers who lack the techniques to hack IT methods by themselves.
The modern Genesis Current market takedown confirmed how these marketplaces are evolving. Providing “digital fingerprints” for sale, alternatively of just a compromised username and password, continually up-to-date identities had been out there for a subscription. Far more than just a stolen established of credentials, these fingerprints paired with carefully-positioned VPN accessibility that allowed an attacker considerably increased entry than stolen qualifications on your own can provide.
The shady underground nature of these markets tends to make them hard to find out and eliminate. A person may perhaps be eradicated with one more popping up mere days later. With the median price tag of a business enterprise email compromise attack soaring to $50,000 alone in 2023, the acquiring of stolen credentials is all the much more appealing for menace actors.
Shield your organization versus stolen credentials
With a whole 49% of breaches involving stolen credentials and evolving digital black markets, these kinds of as Genesis, instruments devoted to detecting compromised passwords are critical for overworked IT departments. Specops Password Plan withBreached Password Defense can help end users generate stronger passwords in Active Directory with dynamic, educational consumer opinions and blocks the use of over 3 billion unique compromised passwords.
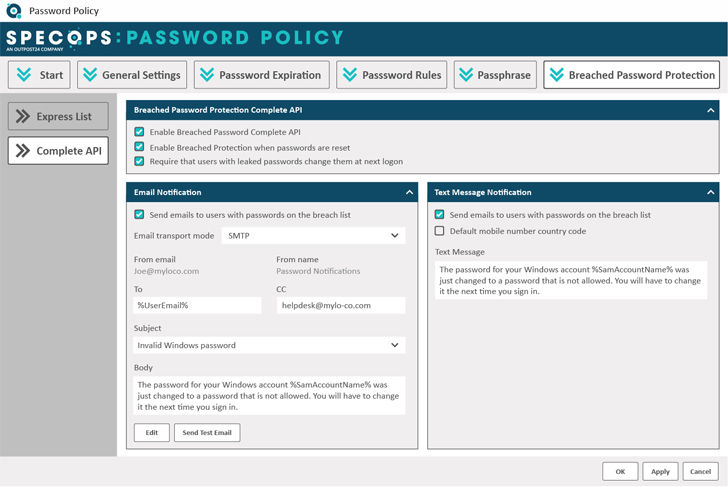
This contains lists observed on dark websites such as Genesis and passwords being utilized in attacks right now on Specops honeypot accounts. IT teams get pleasure from tight Advert integration, and uncomplicated-to-use end-user interfaces for complying with sophisticated password insurance policies and preventing the use of weak and compromised qualifications.
Fascinated in having a initial step towards far better password security? Scan your Energetic Directory with Specops Password Auditor for visibility into how numerous compromised passwords may well currently be in your current surroundings. Get started closing off quick attack routes today to steer clear of major compromises in the potential.
Identified this report interesting? Abide by us on Twitter and LinkedIn to go through additional exceptional information we publish.
Some parts of this article are sourced from:
thehackernews.com


 Experts Uncover Weaknesses in PowerShell Gallery Enabling Supply Chain Attacks
Experts Uncover Weaknesses in PowerShell Gallery Enabling Supply Chain Attacks