Energetic flaws in the PowerShell Gallery could be weaponized by threat actors to pull off source chain assaults versus the registry’s buyers.
“These flaws make typosquatting attacks inevitable in this registry, even though also building it extremely complicated for consumers to determine the correct operator of a offer,” Aqua security researchers Mor Weinberger, Yakir Kadkoda, and Ilay Goldman reported in a report shared with The Hacker News.
Maintained by Microsoft, PowerShell Gallery is a central repository for sharing and buying PowerShell code, together with PowerShell modules, scripts, and Wanted State Configuration (DSC) methods. The registry boasts 11,829 exceptional deals and 244,615 deals in overall.
The issues identified by the cloud security company have to do with the service’s lax coverage bordering package deal names, missing protections in opposition to typosquatting assaults, as a result enabling attackers to add destructive PowerShell modules that seem real to unsuspecting end users.

A next flaw pertains to the ability of a bad actor to spoof the metadata of a module — which include Author(s), Copyright, and Description fields — to make it appear additional legit, thus deceiving unwitting users into setting up them.
“The only way for buyers to identify the real author/proprietor is to open the ‘Package Details’ tab,” the scientists stated.
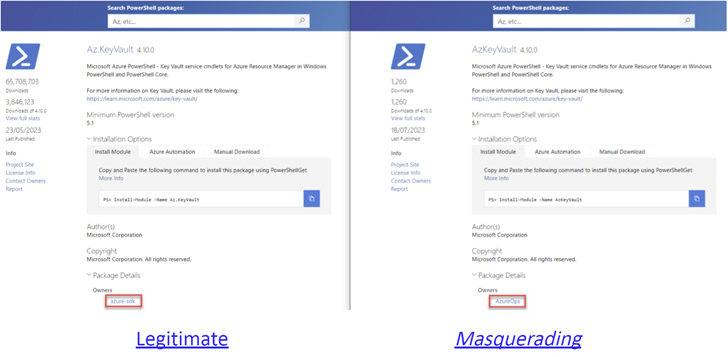
“Having said that, this will only lead them to the profile of the fake writer, as the attacker can freely select any identify when developing a consumer in the PowerShell Gallery. Hence, pinpointing the actual author of a PowerShell module in the PowerShell Gallery poses a complicated job.”
Also discovered is a third flaw that could be abused by attackers to enumerate all package names and variations, including those people that are unlisted and meant to be hidden from public view.
This can be attained by using the PowerShell API “https://www.powershellgallery.com/api/v2/Offers?$skip=variety,” enabling an attacker to obtain unrestricted entry to the comprehensive PowerShell package databases, which includes associated versions.

“This uncontrolled access delivers destructive actors with the potential to lookup for prospective delicate information within unlisted deals. Consequently, any unlisted package deal that is made up of confidential details, gets really susceptible to compromise,” the scientists explained.
Aqua said it described the shortcomings to Microsoft in September 2022, following which the Windows maker is claimed to have set in area reactive fixes as of March 7, 2023. The troubles, however, continue to be reproducible.
“As we more and more count on open up-supply jobs and registries, the security threats affiliated with them develop into more distinguished,” the researchers concluded.
“The duty for securing customers mainly lies with the system. It is really essential that PowerShell Gallery, and very similar platforms, acquire necessary ways to greatly enhance their security actions.”
Identified this report fascinating? Adhere to us on Twitter and LinkedIn to browse additional distinctive content material we put up.
Some parts of this article are sourced from:
thehackernews.com

 Guide: How Google Workspace-based Organizations can leverage Chrome to improve Security
Guide: How Google Workspace-based Organizations can leverage Chrome to improve Security