Risk actors have been leveraging bogus web sites marketing common movie conferencing application these kinds of as Google Meet up with, Skype, and Zoom to provide a assortment of malware focusing on both of those Android and Windows end users considering the fact that December 2023.
“The threat actor is distributing Distant Accessibility Trojans (RATs) together with SpyNote RAT for Android platforms, and NjRAT and DCRat for Windows devices,” Zscaler ThreatLabz scientists reported.
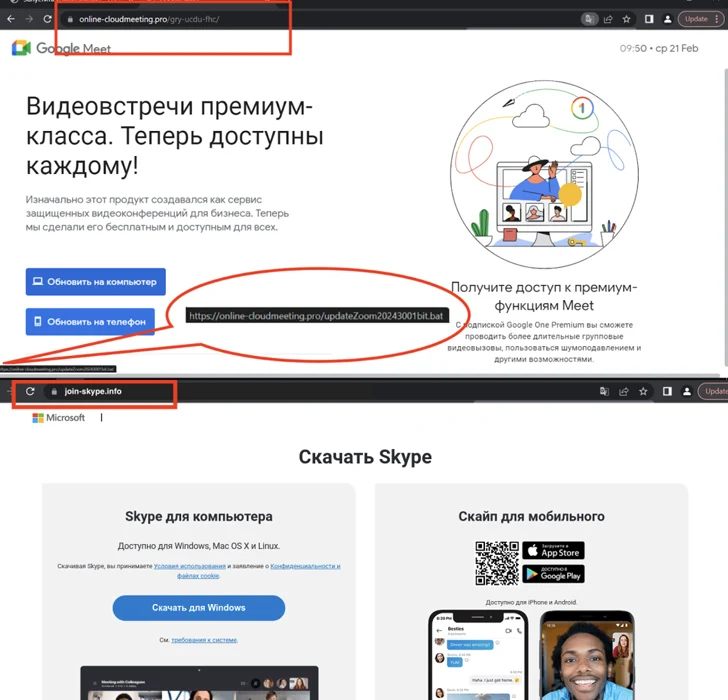
The spoofed sites are in Russian and are hosted on domains that intently resemble their legit counterparts, indicating that the attackers are making use of typosquatting tricks to entice prospective victims into downloading the malware.

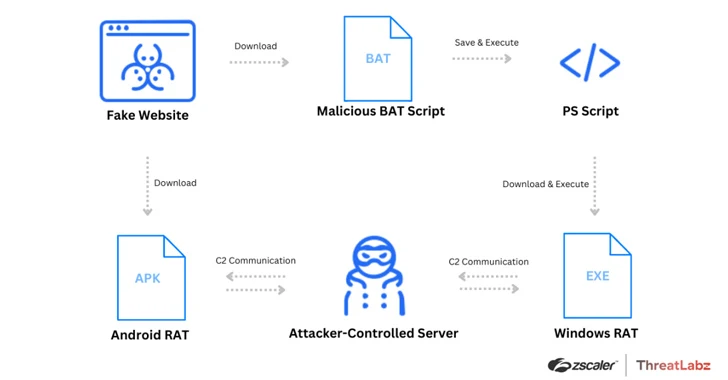
They also appear with solutions to obtain the app for Android, iOS, and Windows platforms. Whilst clicking on the button for Android downloads an APK file, clicking on the Windows app button triggers the download of a batch script.
The destructive batch script is dependable for executing a PowerShell script, which, in convert, downloads and executes the distant accessibility trojan.
At this time, there is no proof that the menace actor is concentrating on iOS consumers, presented that clicking on the button for the iOS application normally takes the consumer to the genuine Apple App Keep listing for Skype.
“A threat actor is utilizing these lures to distribute RATs for Android and Windows, which can steal confidential facts, log keystrokes, and steal documents,” the scientists mentioned.
The improvement will come as the AhnLab Security Intelligence Middle (ASEC) unveiled that a new malware dubbed WogRAT targeting equally Windows and Linux is abusing a no cost on the net notepad system called aNotepad as a covert vector for hosting and retrieving malicious code.
It truly is mentioned to be lively from at the very least late 2022, targeting Asian international locations like China, Hong Kong, Japan, and Singapore, between other people. That explained, it is at this time not identified how the malware is dispersed in the wild.
“When WogRAT is operate for the initially time, it collects simple information of the infected process and sends them to the C&C server,” ASEC mentioned. “The malware then supports commands such as executing commands, sending benefits, downloading documents, and uploading these files.”
It also coincides with superior-quantity phishing campaigns orchestrated by a monetarily determined cybercriminal actor recognised as TA4903 to steal company credentials and probable stick to them with organization email compromise (BEC) assaults. The adversary has been active given that at minimum 2019, with the routines intensifying write-up mid-2023.
“TA4903 routinely conducts campaigns spoofing a variety of U.S. govt entities to steal company credentials,” Proofpoint explained. “The actor also spoofs companies in numerous sectors which includes building, finance, healthcare, foodstuff and beverage, and some others.”

Attack chains contain the use of QR codes (aka quishing) for credential phishing as properly as relying on the EvilProxy adversary-in-the-middle (AiTM) phishing kit to bypass two-component authentication (2FA) protections.
At the time a focus on mailbox is compromised, the menace actor has been noticed browsing for details suitable to payments, invoices, and lender data, with the top purpose of hijacking current email threads and carrying out invoice fraud.
Phishing campaigns have also functioned as a conduit for other malware family members like DarkGate, Agent Tesla, and Remcos RAT, the previous of which leverages steganographic decoys to drop the malware on compromised hosts.
Found this report appealing? Abide by us on Twitter and LinkedIn to go through extra exclusive written content we post.
Some parts of this article are sourced from:
thehackernews.com

 Hackers Exploit Misconfigured YARN, Docker, Confluence, Redis Servers for Crypto Mining
Hackers Exploit Misconfigured YARN, Docker, Confluence, Redis Servers for Crypto Mining