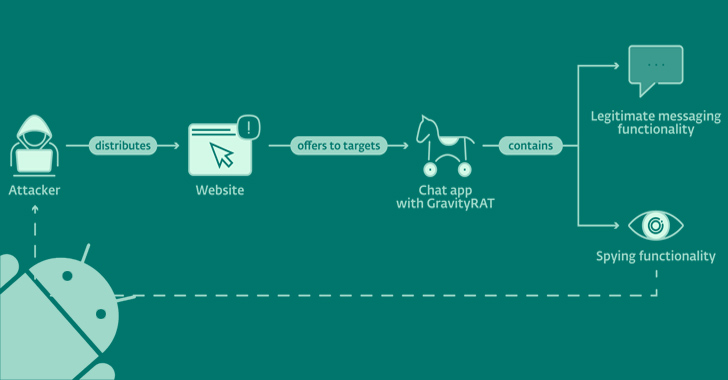
An updated version of an Android remote entry trojan dubbed GravityRAT has been found masquerading as messaging applications BingeChat and Chatico as element of a narrowly focused campaign since June 2022.
“Noteworthy in the freshly found marketing campaign, GravityRAT can exfiltrate WhatsApp backups and receive instructions to delete data files,” ESET researcher Lukáš Štefanko mentioned in a new report revealed currently.
“The malicious applications also deliver authentic chat operation based on the open up-source OMEMO Instant Messenger application.”
GravityRAT is the name given to a cross-platform malware which is capable of focusing on Windows, Android, and macOS gadgets. The Slovak cybersecurity business is tracking the exercise under the identify SpaceCobra.

The menace actor is suspected to be based mostly in Pakistan, with modern assaults involving GravityRAT focusing on armed forces personnel in India and among the the Pakistan Air Force by camouflaging it as cloud storage and enjoyment applications, as disclosed by Meta very last month.
The use of chat apps as a lure to distribute the malware was beforehand highlighted in November 2021 by Cyble, which analyzed a sample named “SoSafe Chat” that was uploaded to the VirusTotal databases from India.
The chat applications, though not available on Google Enjoy, are distributed via rogue sites selling totally free messaging services: bingechat[.]net and chatico[.]co[.]british isles.
“This group utilized fictitious personas — posing as recruiters for equally respectable and fake protection corporations and governments, navy personnel, journalists, and females seeking to make a passionate link — in an attempt to develop have confidence in with the men and women they focused,” Meta stated in its Quarterly Adversarial Threat Report.
The modus operandi implies that potential targets are contacted on Facebook and Instagram with the purpose of tricking them into clicking on the backlinks and downloading the malicious apps.
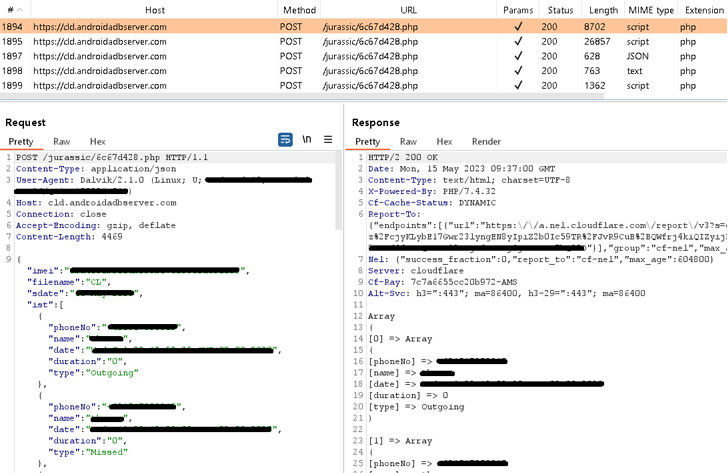
GravityRAT, like most Android backdoors, requests for intrusive permissions underneath the garb of a seemingly reputable application to harvest delicate details this kind of as contacts, SMSes, call logs, information, place information, and audio recordings without the need of the victim’s awareness.
The captured details is finally exfiltrated to a distant server below the risk actor’s regulate. It is really really worth noting that employing the application is conditional on owning an account.
Future WEBINAR🔐 Mastering API Security: Being familiar with Your Genuine Attack Floor
Find the untapped vulnerabilities in your API ecosystem and choose proactive techniques to ironclad security. Sign up for our insightful webinar!
Be a part of the Session.wn-button,.wn-label,.wn-label:right afterdisplay:inline-block.examine_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px good #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top rated-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-ideal-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimensions:13pxmargin:20px 0font-pounds:600letter-spacing:.6pxcolor:#596cec.wn-label:immediately afterwidth:50pxheight:6pxcontent:”border-prime:2px sound #d9deffmargin: 8px.wn-titlefont-measurement:21pxpadding:10px 0font-weight:900textual content-align:leftline-top:33px.wn-descriptiontextual content-align:leftfont-size:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-color:#4469f5font-measurement:15pxcolor:#fff!importantborder:0line-peak:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-fat:500letter-spacing:.2px
What will make the new variation of GravityRAT stand out is its means to steal WhatsApp backup information and obtain instructions from the command-and-handle (C2) server to delete connect with logs, call lists, and files with unique extensions.
“These are incredibly unique instructions that are not commonly noticed in Android malware,” Štefanko pointed out.
The advancement arrives as Android customers in Vietnam have been victimized by a new pressure of banking cum stealer malware known as HelloTeacher that makes use of legitimate messaging applications like Viber or Kik as a address to siphon sensitive information and have out unauthorized fund transfers by abusing the accessibility expert services API.
Also found out by Cyble is a cloud mining fraud that “prompts consumers to download a destructive application to start off mining,” only to choose advantage of its permissions to the accessibility solutions to collect delicate facts from cryptocurrency wallets and banking apps.
The economical trojan, codenamed Roamer, exemplifies the craze of using phishing web-sites and Telegram channels as distribution vectors, thus effectively widening the opportunity target pool.
“People will have to physical exercise warning and chorus from pursuing suspicious cryptocurrency mining channels on platforms like Telegram, as these channels can direct to significant monetary losses and compromise sensitive private info,” Cyble explained.
Uncovered this posting exciting? Adhere to us on Twitter and LinkedIn to read through a lot more exclusive content we article.
Some parts of this article are sourced from:
thehackernews.com

 New Research: 6% of Employees Paste Sensitive Data into GenAI tools as ChatGPT
New Research: 6% of Employees Paste Sensitive Data into GenAI tools as ChatGPT