The menace actors powering the Vidar malware have built adjustments to their backend infrastructure, indicating attempts to retool and conceal their on the net path in response to community disclosures about their modus operandi.
“Vidar danger actors go on to rotate their backend IP infrastructure, favoring vendors in Moldova and Russia,” cybersecurity company Crew Cymru said in a new assessment shared with The Hacker News.
Vidar is a commercial information and facts stealer that’s acknowledged to be active considering that late 2018. It is really also a fork of a further stealer malware named Arkei and is provided for sale amongst $130 and $750 depending on the membership tier.
Typically shipped through phishing campaigns and web-sites advertising and marketing cracked software program, the malware will come with a vast vary of abilities to harvest sensitive info from infected hosts. Vidar has also been observed to be distributed via rogue Google Adverts and a malware loader dubbed Bumblebee.

Workforce Cymru, in a report posted earlier January, mentioned that “Vidar operators have break up their infrastructure into two components a single committed to their frequent shoppers and the other for the management crew, and also probably high quality / important end users.”
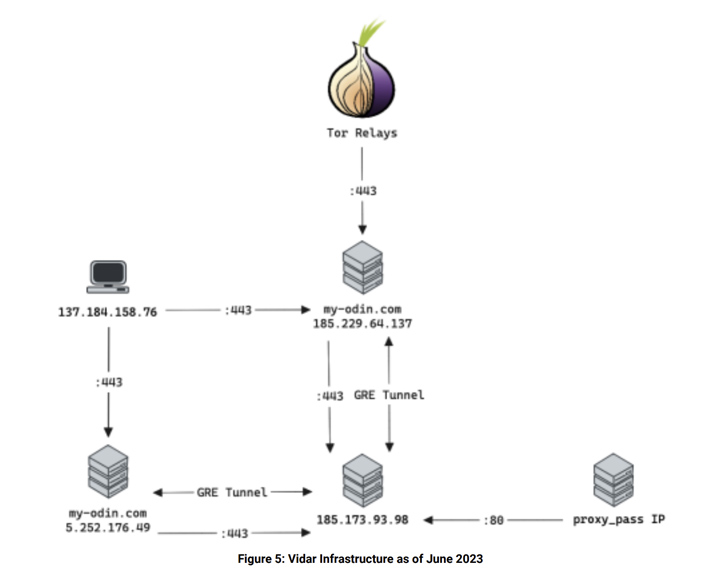
A critical domain utilised by the Vidar actors is my-odin[.]com, which serves as the one-stop desired destination to handle the panel, authenticate affiliate marketers, and share data files.
When earlier it was possible to download information from the site without the need of any authentication, executing the exact action now redirects the user to a login website page. One more adjust consists of updates to the IP address hosting the area by itself.
This involves moving from 186.2.166[.]15 to 5.252.179[.]201 to 5.252.176[.]49 by the end of March 2023, with the risk actors accessing the latter utilizing VPN servers all over the very same time.
Approaching WEBINAR🔐 Mastering API Security: Understanding Your True Attack Area
Explore the untapped vulnerabilities in your API ecosystem and consider proactive measures to ironclad security. Join our insightful webinar!
Sign up for the Session.wn-button,.wn-label,.wn-label:immediately afterdisplay screen:inline-block.look at_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px reliable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-leading-still left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-suitable-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-size:13pxmargin:20px 0font-body weight:600letter-spacing:.6pxcolor:#596cec.wn-label:right afterwidth:50pxheight:6pxcontent:”border-major:2px reliable #d9deffmargin: 8px.wn-titlefont-sizing:21pxpadding:10px 0font-weight:900text-align:leftline-height:33px.wn-descriptiontext-align:leftfont-sizing:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-shade:#4469f5font-size:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-weight:500letter-spacing:.2px
“By making use of VPN infrastructure, which in at minimum component was also used by a lot of other benign people, it is obvious that the Vidar risk actors could be getting actions to anonymize their administration actions by hiding in normal Internet sounds,” Staff Cymru pointed out.
The cybersecurity enterprise said it also detected outbound connections from 5.252.176[.]49 to a authentic web-site called blonk[.]co as perfectly as a host positioned in Russia (185.173.93[.]98:443).
The Vidar infrastructure has been found to acquire but yet another facelift productive May perhaps 3, 2023, with the introduction of a new IP deal with 185.229.64[.]137 hosting the my-odin[.]com domain together with the use of TOR relays by the operators to access their accounts and malware repositories.
The conclusions “presents even further perception into the ‘behind-the-scenes’ operation of Vidar, demonstrating the evolution of its administration infrastructure as effectively as proof of ways taken by the menace actors to probably address their tracks,” the company stated.
Discovered this article exciting? Observe us on Twitter and LinkedIn to go through a lot more special written content we submit.
Some parts of this article are sourced from:
thehackernews.com


 Warning: GravityRAT Android Trojan Steals WhatsApp Backups and Deletes Files
Warning: GravityRAT Android Trojan Steals WhatsApp Backups and Deletes Files