The Android banking trojan identified as Vultur has resurfaced with a suite of new options and improved anti-assessment and detection evasion tactics, enabling its operators to remotely interact with a cell system and harvest sensitive info.
“Vultur has also commenced masquerading a lot more of its malicious exercise by encrypting its C2 conversation, using various encrypted payloads that are decrypted on the fly, and utilizing the guise of legitimate programs to carry out its destructive steps,” NCC Team researcher Joshua Kamp mentioned in a report released previous week.
Vultur was initially disclosed in early 2021, with the malware able of leveraging Android’s accessibility services APIs to execute its malicious steps.
The malware has been observed to be dispersed by way of trojanized dropper apps on the Google Enjoy Retail store, masquerading as authenticator and productiveness apps to trick unwitting users into putting in them. These dropper applications are provided as component of a dropper-as-a-company (DaaS) operation named Brunhilda.
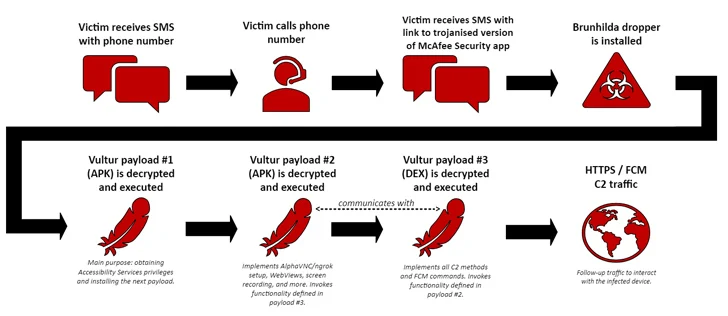
Other attack chains, as noticed by NCC Team, require the droppers being distribute making use of a mixture of SMS messages and phone phone calls – a procedure called phone-oriented attack supply (TOAD) – to eventually provide an current model of the malware.

“The very first SMS concept guides the sufferer to a phone simply call,” Kamp claimed. When the sufferer calls the quantity, the fraudster supplies the target with a next SMS that includes the connection to the dropper: a modified edition of the [legitimate] McAfee Security app.”
The original SMS message aims to induce a untrue sense of urgency by instructing the recipients to call a amount to authorize a non-existent transaction that will involve a substantial sum of dollars.
Upon installation, the malicious dropper executes 3 connected payloads (two APKs and one DEX file) that sign up the bot with the C2 server, receive accessibility solutions permissions for remote access by using AlphaVNC and ngrok, and operate instructions fetched from the C2 server.
Just one of the notable additions to Vultur is the capacity to remotely interact with the infected product, like carrying out clicks, scrolls, and swipes, via Android’s accessibility services, as well as download, upload, delete, set up, and find files.
In addition, the malware is outfitted to prevent the victims from interacting with a predefined listing of apps, exhibit tailor made notifications in the position bar, and even disable Keyguard to bypass lock display security measures.
“Vultur’s the latest developments have shown a shift in concentrate towards maximizing distant manage more than infected products,” Kamp stated.
“With the functionality to issue instructions for scrolling, swipe gestures, clicks, volume control, blocking applications from jogging, and even incorporating file supervisor functionality, it is apparent that the main goal is to achieve complete command more than compromised gadgets.”
The progress arrives as Staff Cymru revealed the Octo (aka Coper) Android banking trojan’s changeover to a malware-as-a-provider procedure, presenting its companies to other danger actors for conducting information and facts theft.
“The malware offers a selection of superior capabilities, such as keylogging, interception of SMS messages and press notifications, and regulate above the device’s display screen,” the company mentioned.

“It employs many injects to steal sensitive details, these as passwords and login qualifications, by exhibiting faux screens or overlays. In addition, it makes use of VNC (Virtual Network Computing) for distant entry to products, maximizing its surveillance capabilities.”
Octo strategies are believed to have compromised 45,000 units, mostly spanning Portugal, Spain, Turkey, and the U.S. Some of the other victims are found in France, the Netherlands, Canada, India, and Japan.
The findings also observe the emergence of a new campaign focusing on Android consumers in India that distributes destructive APK deals posing as online booking, billing, and courier products and services via a malware-as-a-support (MaaS) providing.
The malware “targets theft of banking data, SMS messages, and other private facts from victims’ gadgets,” Broadcom-owned Symantec stated in a bulletin.
Observed this report fascinating? Comply with us on Twitter and LinkedIn to study more exclusive content material we put up.
Some parts of this article are sourced from:
thehackernews.com


 New Webinar: Avoiding Application Security Blind Spots with OPSWAT and F5Mar 28, 2024Application Security / Webinar Considering the ever-changing state of cybersecurity, it's never too late to ask yourself, "am I doing what's necessary to keep my organization's web applications secure?" The continuous evolution of technology introduces new and increasingly sophisticated threats daily, posing challenges to organizations all over the world and across the broader spectrum of industries striving to maintain reliable defenses. 2024 promises to be no exception. Threat actors continue to adapt their tactics, techniques, and procedures to exploit vulnerabilities in innovative ways, injecting malicious content into files that bypass traditional antivirus solutions and advanced, AI and ML-powered solutions alike. Therefore, organizations must assess and continually reinforce their security measures. One critical aspect that organizations often grapple with is identifying and addressing security blind spots. These are areas within the infrastructure where vulnerabilities exist but may
New Webinar: Avoiding Application Security Blind Spots with OPSWAT and F5Mar 28, 2024Application Security / Webinar Considering the ever-changing state of cybersecurity, it's never too late to ask yourself, "am I doing what's necessary to keep my organization's web applications secure?" The continuous evolution of technology introduces new and increasingly sophisticated threats daily, posing challenges to organizations all over the world and across the broader spectrum of industries striving to maintain reliable defenses. 2024 promises to be no exception. Threat actors continue to adapt their tactics, techniques, and procedures to exploit vulnerabilities in innovative ways, injecting malicious content into files that bypass traditional antivirus solutions and advanced, AI and ML-powered solutions alike. Therefore, organizations must assess and continually reinforce their security measures. One critical aspect that organizations often grapple with is identifying and addressing security blind spots. These are areas within the infrastructure where vulnerabilities exist but may