Several malicious Android applications that turn cell units functioning the working method into residential proxies (RESIPs) for other risk actors have been noticed on the Google Perform Retailer.
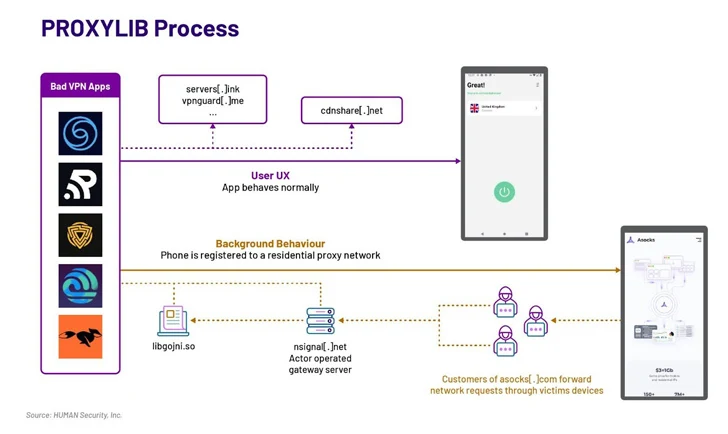
The results appear from HUMAN’s Satori Threat Intelligence staff, which stated the cluster of VPN applications came equipped with a Golang library that reworked the user’s machine into a proxy node devoid of their understanding.
The procedure has been codenamed PROXYLIB by the enterprise. The 29 apps in issue have considering that been eradicated by Google.
Household proxies are a network of proxy servers sourced from authentic IP addresses provided by internet provider suppliers (ISPs), serving to people hide their true IP addresses by routing their internet site visitors by way of an middleman server.
The anonymity positive aspects apart, they are ripe for abuse by danger actors to not only obfuscate their origins, but also to perform a wide variety of assaults.

“When a menace actor utilizes a household proxy, the site visitors from these assaults seems to be coming from distinctive household IP addresses alternatively of an IP of a details heart or other elements of a danger actor’s infrastructure,” security researchers claimed. “Lots of danger actors purchase accessibility to these networks to aid their operations.”
Some of these networks can be created by malware operators tricking unsuspecting people into putting in bogus apps that in essence corral the products into a botnet that is then monetized for income by selling the accessibility to other customers.
The Android VPN apps identified by HUMAN are designed to establish make contact with with a remote server, enroll the infected product to the network, and procedure any ask for from the proxy network.
Yet another notable component of these applications is that a subset of them discovered amongst May possibly and October 2023 integrate a software package enhancement package (SDK) from LumiApps, which consists of the proxyware operation. In both instances, the destructive functionality is pulled off working with a native Golang library.
LumiApps also gives a provider that in essence permits end users to add any APK file of their alternative, including reputable applications, and bundle the SDK to it without the need of getting to build a person account, which can then be re-downloaded and shared with many others.
These modified applications – referred to as mods – are then distributed in and out of the Google Participate in Retail outlet. LumiApps promotes itself and the SDK as an choice app monetization process to rendering ads.
There is proof indicating that the threat actor behind PROXYLIB is marketing obtain to the proxy network established by the infected devices through LumiApps and Asocks, a company that advertises alone as a vendor of residential proxies.
What is actually more, in an energy to bake the SDK into as numerous applications as probable and increase the measurement of the botnet, LumiApps delivers cash rewards to developers based on the quantity of targeted visitors that receives routed by user equipment that have put in their applications. The SDK service is also advertised on social media and black hat boards.

The latest exploration released by Orange Cyberdefense and Sekoia characterised residential proxies as section of a “fragmented yet interconnected ecosystem,” in which proxyware products and services are marketed in numerous ways ranging from voluntary contributions to committed stores and reselling channels.
“[In the case of SDKs], the proxyware is generally embedded in a merchandise or services,” the corporations mentioned. Buyers may not detect that proxyware will be mounted when accepting the phrases of use of the principal application it is embedded with. This lack of transparency leads to buyers sharing their Internet link with out a obvious being familiar with.”
The improvement arrives as the Lumen Black Lotus Labs disclosed that finish-of-everyday living (EoL) small property/small office (SOHO) routers and IoT products are currently being compromised by a botnet regarded as TheMoon to electrical power a felony proxy assistance named Faceless.
Found this report interesting? Stick to us on Twitter and LinkedIn to study a lot more distinctive information we post.
Some parts of this article are sourced from:
thehackernews.com

 Vultur Android Banking Trojan Returns with Upgraded Remote Control Capabilities
Vultur Android Banking Trojan Returns with Upgraded Remote Control Capabilities