The U.S. Federal Bureau of Investigation (FBI) is warning that Barracuda Networks Email Security Gateway (ESG) appliances patched versus a lately disclosed critical flaw go on to be at risk of prospective compromise from suspected Chinese hacking teams.
It also deemed the fixes as “ineffective” and that it “continues to notice lively intrusions and considers all impacted Barracuda ESG appliances to be compromised and vulnerable to this exploit.”
Tracked as CVE-2023-2868 (CVSS score: 9.8), the zero-working day bug is said to have been weaponized as early as October 2022, additional than 7 months before the security hole was plugged. Google-owned Mandiant is tracking the China-nexus exercise cluster beneath the name UNC4841.

The distant command injection vulnerability, impacting variations 5.1.3.001 via 9.2..006, makes it possible for for unauthorized execution of process commands with administrator privileges on the ESG product.
In the attacks observed so far, a thriving breach acts as a conduit to deploy numerous malware strains these as SALTWATER, SEASIDE, SEASPY, SANDBAR, SEASPRAY, SKIPJACK, WHIRLPOOL, and SUBMARINE (aka DEPTHCHARGE) that let for the execution of arbitrary commands and defense evasion.
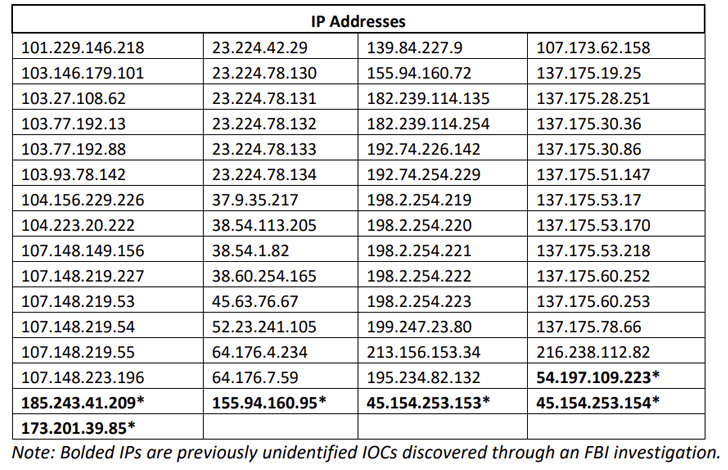
“The cyber actors utilized this vulnerability to insert destructive payloads on to the ESG equipment with a assortment of abilities that enabled persistent entry, email scanning, credential harvesting, and data exfiltration,” the FBI said.
The threat intelligence company has characterised UNC4841 as both aggressive and skilled, demonstrating a flair for sophistication and quickly adapting their tailor made tooling to employ added persistence mechanisms and preserve their foothold into higher precedence targets.
The federal agency is recommending prospects to isolate and swap all affected ESG gadgets with speedy influence, and scan the networks for suspicious outgoing traffic.
Discovered this short article appealing? Comply with us on Twitter and LinkedIn to browse far more exceptional content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Lazarus Group Exploits Critical Zoho ManageEngine Flaw to Deploy Stealthy QuiteRAT Malware
Lazarus Group Exploits Critical Zoho ManageEngine Flaw to Deploy Stealthy QuiteRAT Malware