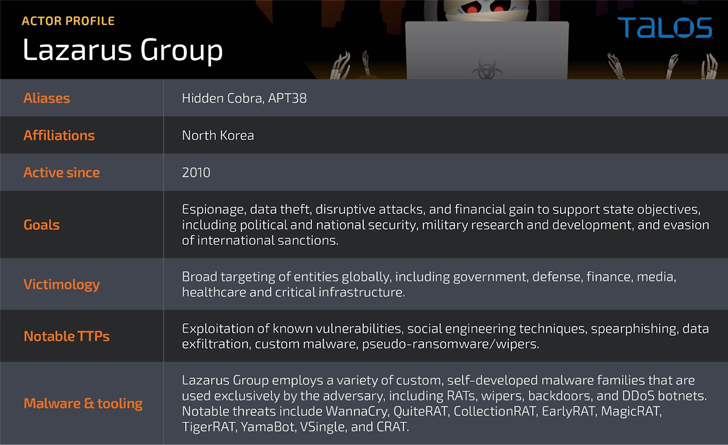
The North Korea-connected danger actor identified as Lazarus Team has been noticed exploiting a now-patched critical security flaw impacting Zoho ManageEngine ServiceDesk Additionally to distribute a distant entry trojan called this sort of as QuiteRAT.
Targets include internet spine infrastructure and health care entities in Europe and the U.S., cybersecurity company Cisco Talos said in a two-portion evaluation printed currently.
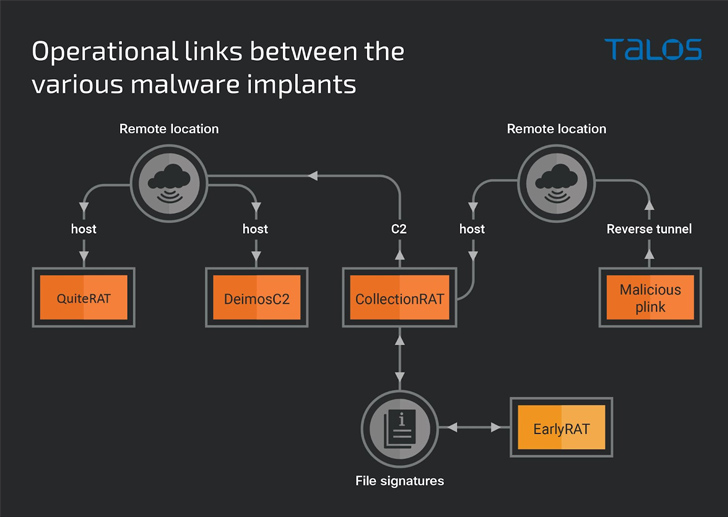
What is actually much more, a nearer evaluation of the adversary’s recycled attack infrastructure in its cyber assaults on enterprises has led to the discovery of a new threat dubbed CollectionRAT.
The truth that the Lazarus Group carries on to count on the exact tradecraft inspite of these parts getting very well-documented over the a long time underscores the danger actor’s confidence in their functions, Talos pointed out.
QuiteRAT is mentioned to be a successor to MagicRAT, itself a follow-up to TigerRAT, although CollectionRAT appears to share overlaps with EarlyRAT (aka Jupiter), an implant composed in PureBasic with abilities to run instructions on the endpoint.

“QuiteRAT has several of the exact same abilities as Lazarus Group’s improved-identified MagicRAT malware, but its file dimensions is considerably lesser,” security scientists Asheer Malhotra, Vitor Ventura, and Jungsoo An explained. “Both of those implants are created on the Qt framework and include things like capabilities these types of as arbitrary command execution.”
The use of the Qt framework is viewed as an intentional energy on the element of the adversary to make assessment a lot a lot more difficult as it “boosts the complexity of the malware’s code.”
The action, detected in early 2023, associated the exploitation of CVE-2022-47966, a mere 5 times immediately after proof-of-concept (Poc) for the flaw emerged on the net, to instantly deploy the QuiteRAT binary from a malicious URL.
“QuiteRAT is obviously an evolution of MagicRAT,” the scientists mentioned. “Though MagicRAT is a even larger, bulkier malware relatives averaging all over 18 MB in dimensions, QuiteRAT is a a great deal substantially scaled-down implementation, averaging close to 4 to 5 MB in dimensions.”
A further very important variance concerning the two is the absence of a created-in persistence system in QuiteRAT, necessitating that a command be issued from the server to assure ongoing procedure on the compromised host.
The results also overlap with one more campaign uncovered by WithSecure before this February in which security flaws in unpatched Zimbra gadgets had been used to breach target units and ultimately install QuiteRAT.

Cisco Talos claimed the adversary is “significantly relying on open up-resource applications and frameworks in the preliminary entry section of their assaults, as opposed to strictly employing them in the put up-compromise phase.”
This incorporates the GoLang-primarily based open-supply DeimosC2 framework to acquire persistent accessibility, with CollectionRAT largely used to acquire metadata, operate arbitrary instructions, manage data files on the infected technique, and deliver supplemental payloads.
It’s not right away very clear how CollectionRAT is propagated, but proof exhibits that a trojanized duplicate of the PuTTY Hyperlink (Plink) utility hosted on the similar infrastructure is being applied to establish a distant tunnel to the method and provide the malware.
“Lazarus Group earlier relied on the use of customized-crafted implants this sort of as MagicRAT, VSingle, Dtrack, and YamaBot as a indicates of developing persistent original entry on a properly compromised program,” the scientists said.
“These implants are then instrumented to deploy a range of open up-supply or twin-use equipment to execute a multitude of destructive fingers-on-keyboard actions in the compromised organization network.”
The development is a signal that the Lazarus Group is frequently shifting methods and expanding its destructive arsenal, at the same time weaponizing newly disclosed vulnerabilities in computer software to devastating effect.
Uncovered this posting appealing? Adhere to us on Twitter and LinkedIn to read extra unique material we article.
Some parts of this article are sourced from:
thehackernews.com


 New Telegram Bot “Telekopye” Powering Large-scale Phishing Scams from Russia
New Telegram Bot “Telekopye” Powering Large-scale Phishing Scams from Russia