If you’ve listened to software distributors in the identity place recently, you will have noticed that “unified” has immediately develop into the buzzword that all people is adopting to describe their portfolio. And this is great! Unified identity has some remarkable positive aspects!
On the other hand (there is normally a however, right?) not just about every “unified” “id” “security” “platform” is created equivalent. Some sellers phone the mix of workforce IDaaS and consumer IDaaS a unified identity remedy, though others offer you a glorified 2FA assistance – unified only in the head of their marketers.
Your landscape matters!
So ignore for a second what the sellers assert, and think back again to your group and your identity security landscape. Think about this new definition: “unified” is what has the means to consolidate your id challenges with a comprehensive identification solution.
Here’s an case in point: you are liable for the identification infrastructure of a big medical center. Frontline employees, administrative workers, audit/compliance demands and a big variety of external customers. You are making use of Lively Directory, and your LOB software would not do identification. For this healthcare facility, unified id suggests powerful obtain management for clients and frontline personnel, powerful joiner-leaver-mover handling, Advertisement hardening and organization-quality reporting. Something less fails the unified assure and indicates their internal identification landscape stays fractured.
Another illustration: a smaller software program dev studio. They want extra powerful controls on Privileged Access Management (PAM) to secure the progress pipeline and make certain they will not develop into the original attack vector in a source chain attack. But they also have to have Identity Governance and Administration (IGA) for equipment entities and their homeowners, functioning on the many automated tasks they are working. A alternative which covers PAM and IGA independently from each and every other is not unified.
What is the benefit of unified identity anyhow?
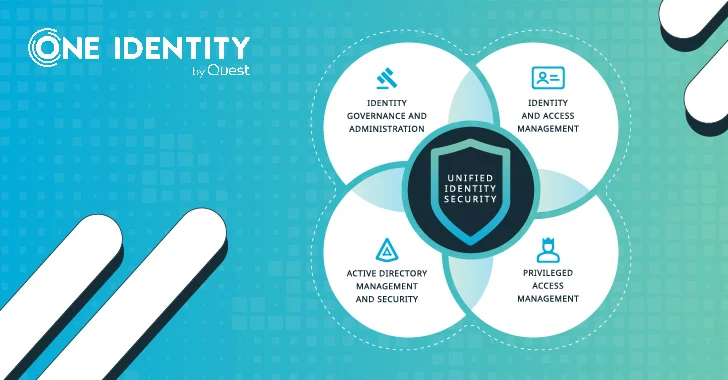
So why has “unified identification ” become these types of a hot buzzword? Effectively, there are some truly good arguments for it. Historically, the identification space was really fractured, with numerous gurus not even taking into consideration it a singular sector until finally pretty recently. Identity Governance and Administration (IGA), Accessibility Management (AM), and Privileged Accessibility Administration (PAM) ended up the key sub-marketplaces, with a huge array of adjacent areas this kind of as Advertisement bridging and endpoint privilege management.
The essential driver for unified identification is this extreme fragmentation: a large corporation has on average 45 unique security applications. Add to this the id sprawl, a development where businesses preserve acquiring more and additional id silos in-house – a A single Identification survey shows 50 percent the organizations are utilizing additional than 25 unique units to handle obtain rights. This is simply just not sustainable, and introducing a new device every single time a new danger approaches is absolutely unworkable. So corporations are seeking to consolidate vendors, cut down complexity and trim down the amount of suppliers they get the job done with. The positive aspects of a Unified Identification Platform are a far better cybersecurity posture and larger resilience in the face of security threats, although increasing simplicity and enabling agility.
An additional motive is top rated line value: bundles, volume special discounts and ELAs are a very simple way to minimize costs. Vendor consolidation also provides some a lot less evident personal savings too: a solitary tech stack allows the abilities gap, easing the strain on choosing and schooling, which in switch signifies major personal savings on headcount and may lessen the prerequisite for very skilled senior staff, developing far more price from security with much less sources or place another way, doing work smarter not more durable.
Integration is a essential aspect of the identification landscape – and a person of the major head aches. Security instruments need to have to do the job with each other effortlessly, but that’s hardly ever a given. The industry is not keen on common standards, which can make interoperability pretty tricky to attain. With some effort (which means customization, aid several hours and overhead) id solutions can perform alongside one another pairwise, but generating a full ecosystem of identification applications that do the job flawless alongside one another is a scarce accomplishment. It really is straightforward to see the value a unified identity system delivers below. The applications are pre-tested, pre-validated to do the job jointly, generally devoid of any customization demanded, and the platform elements are supported as just one by the vendor.
This provides us to the last profit: faster time to worth, an expression deserving of any MBA graduate. Id and access management (IAM) tasks are renowned for having a lengthy time to implement, as specialists meticulously formalize organization procedures and carry out them in code or configuration. In massive companies, this is an incredibly intricate activity, as the IAM set up wants to mirror each and every component (and quirk) the enterprise has created up – sometimes more than many years. Implementations become so intricate that they just are unsuccessful – the value and time overruns exceeding the tolerance of organization leaders. In a nutshell: time to price issues in IAM. And a unified identity remedy removes the complexity of the multi-seller method, reducing at the very least one particular issue.
After these gains, let us communicate a draw back: vendor lock-in. Unified identification seems excellent but betting the house on a one vendor is a substantial question. And what if you now have some alternatives in location that you’re happy with? It can be essential to don’t forget that not all unified id distributors are the exact same Some distributors supply modular identification platforms which make it possible for you to continue to keep what you want and unify what you want. This method enables buyers to start out the unification at any position (for illustration with PAM) without having the will need to embrace and put into practice all areas in one huge leap. When buying suppliers, search for this versatile approach.
Observed this article attention-grabbing? Abide by us on Twitter and LinkedIn to browse much more unique material we post.
Some parts of this article are sourced from:
thehackernews.com

 HijackLoader Evolves: Researchers Decode the Latest Evasion Methods
HijackLoader Evolves: Researchers Decode the Latest Evasion Methods