The U.S. authorities on Wednesday explained the Chinese condition-sponsored hacking team recognized as Volt Storm had been embedded into some critical infrastructure networks in the region for at minimum five decades.
Targets of the risk actor incorporate communications, electrical power, transportation, and water and wastewater programs sectors in the U.S. and Guam.
“Volt Typhoon’s preference of targets and pattern of actions is not consistent with regular cyber espionage or intelligence collecting functions, and the U.S. authoring businesses evaluate with large self-assurance that Volt Hurricane actors are pre-positioning themselves on IT networks to enable lateral motion to OT belongings to disrupt capabilities,” the U.S. government said.
The joint advisory, which was released by the Cybersecurity and Infrastructure Security Company (CISA), Nationwide Security Company (NSA), and the Federal Bureau of Investigation (FBI), was also backed by other nations that are component of the 5 Eyes (FVEY) intelligence alliance comprising Australia, Canada, New Zealand, the U.K.
Volt Storm – which is also named Bronze Silhouette, Insidious Taurus, UNC3236, Vanguard Panda, or Voltzite – a stealthy China-centered cyber espionage team that’s thought to be active because June 2021.

It initially arrived to mild in May 2023 when Microsoft disclosed that the hacking crew managed to establish a persistent foothold into critical infrastructure businesses in the U.S. and Guam for prolonged intervals of time sans receiving detected by principally leveraging living-off-the-land (LotL) techniques.
“This variety of tradecraft, recognised as ‘living off the land,’ enables attackers to operate discreetly, with malicious activity blending in with reputable program and network habits producing it complicated to differentiate – even by organizations with extra mature security postures,” the U.K. National Cyber Security Centre (NCSC) said.
An additional hallmark tactic adopted by Volt Hurricane is the use of multi-hop proxies like KV-botnet to route destructive site visitors by way of a network of compromised routers and firewalls in the U.S. to mask its legitimate origins.
Cybersecurity agency CrowdStrike, in a report revealed in June 2023, named out its reliance on an intensive arsenal of open up-resource tooling from a narrow established of victims to reach its strategic aims.
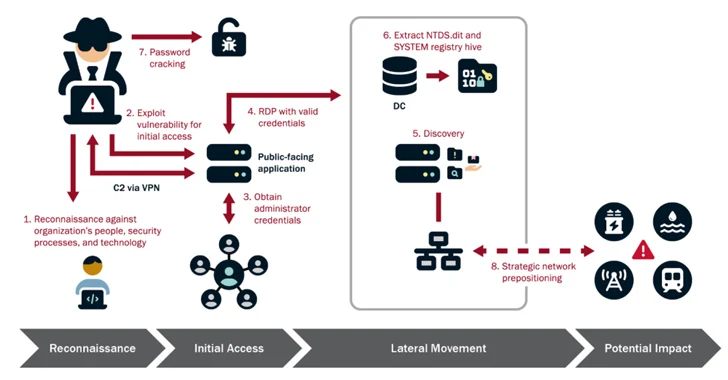
“Volt Typhoon actors carry out intensive pre-exploitation reconnaissance to understand about the concentrate on organization and its environment tailor their strategies, procedures, and treatments (TTPs) to the victim’s ecosystem and devote ongoing assets to preserving persistence and knowledge the concentrate on surroundings more than time, even immediately after preliminary compromise,” the agencies pointed out.
“The team also relies on legitimate accounts and leverages sturdy operational security, which mixed, permits for extensive-phrase undiscovered persistence.”
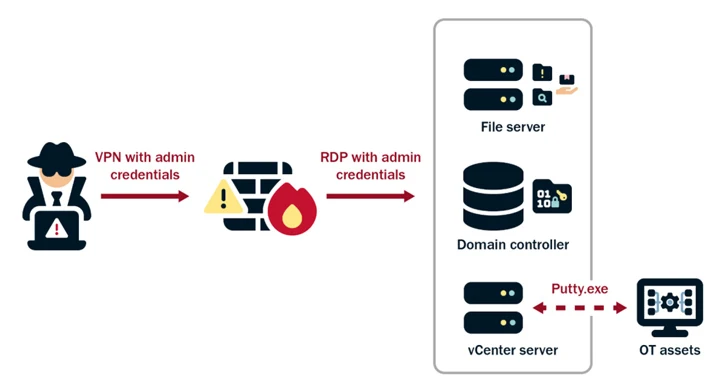
Additionally, the country-point out has been observed trying to get administrator credentials inside of the network by exploiting privilege escalation flaws, subsequently leveraging the elevated obtain to aid lateral motion, reconnaissance, and total domain compromise.
The top aim of the campaign is to retain access to the compromised environments, “methodically” re-concentrating on them over many years to validate and increase their unauthorized accesses. This meticulous approach, for each the businesses, is evidenced in conditions where they have regularly exfiltrated domain credentials to make sure entry to latest and legitimate accounts.
“In addition to leveraging stolen account credentials, the actors use LOTL techniques and keep away from leaving malware artifacts on programs that would induce alerts,” CISA, FBI, and NSA said.

“Their strong concentrate on stealth and operational security lets them to maintain long-term, undiscovered persistence. Additional, Volt Typhoon’s operational security is improved by focused log deletion to conceal their actions inside of the compromised ecosystem.”
The improvement comes as the Citizen Lab unveiled a network of at least 123 websites impersonating community information outlets spanning 30 countries in Europe, Asia, and Latin The united states that’s pushing pro-China written content in a prevalent impact marketing campaign linked to a Beijing public relations company named Shenzhen Haimaiyunxiang Media Co., Ltd.
The Toronto-based digital watchdog, which dubbed the affect procedure PAPERWALL, explained it shares similarities with HaiEnergy, albeit with distinct operators and exceptional TTPs.
“A central attribute of PAPERWALL, noticed across the network of internet sites, is the ephemeral nature of its most intense elements, whereby posts attacking Beijing’s critics are routinely taken out from these sites some time following they are revealed,” the Citizen Lab reported.
In a statement shared with Reuters, a spokesperson for China’s embassy in Washington reported “it is a usual bias and double regular to allege that the pro-China contents and reviews are ‘disinformation,’ and to get in touch with the anti-China ones’ true information.'”
Observed this short article appealing? Abide by us on Twitter and LinkedIn to browse extra exceptional information we article.
Some parts of this article are sourced from:
thehackernews.com

 Unified Identity – look for the meaning behind the hype!
Unified Identity – look for the meaning behind the hype!