The latest information breaches across CircleCI, LastPass, and Okta underscore a common theme: The enterprise SaaS stacks connected to these sector-foremost applications can be at serious risk for compromise.
CircleCI, for instance, plays an integral, SaaS-to-SaaS role for SaaS app improvement. Likewise, tens of 1000’s of corporations rely on Okta and LastPass security roles for SaaS identity and obtain management. Organization and specialized niche SaaS applications alike have efficiently released multitudes of unmonitored endpoints into organizations of all measurements.
Although expending for SaaS security is trending up, it lags driving categories such as cloud infrastructure defense and network security. In accordance to Statista, the average business employs 100+ SaaS apps, several of which are unsanctioned by IT, producing a glaring gap in SaaS security.
Why People Flock to SaaS Applications — And Typically Bypass IT in the Method
As productivity resources for tasks this sort of as promoting automation, document signature, and profits forecasting have shifted from installed computer software to SaaS, so have the behaviors of finish-customers. Staff members find SaaS solutions to aid them accomplish much more in considerably less time, in particular with the expanding decentralization of the IT operate.
Workforce will often find methods to improve their efficiency with instruments of their selection. This conduct is practically nothing novel or in and of alone destructive, but it poses sizeable security challenges. In the era of installed software, companies added endpoint security to do the job equipment and devices to guarantee their staff members couldn’t download destructive computer software or drop victim to malware-dependent assaults. This technique remains a essential aspect of all round endpoint security, but it would not replicate the evolution of the way folks are now performing: outside the house the purview of corporate networks, and usually on individual units.
Relatively than approaching Security or IT to have an understanding of insurance policies for onboarding new SaaS alternatives — and dealing with the chance of red tape, delays, or denial for their requests — they break out the credit score card or decide for a 30-working day absolutely free trial of the SaaS apps. Staff rarely take into account the security implications of the shadow IT they have introduced into the ecosystem as they authorize connecting their new applications to organization SaaS units these types of as Microsoft 365, Salesforce, Workday, or ServiceNow.
These connections, coupled with the users’ inherited authorization settings, could touch the organization’s most delicate details, with no potential to check or management this attack area risk. And it transpires just about every day.
AppOmni: SaaS Security and SSPM Platform
Protect your business’s valuable knowledge across various applications with AppOmni’s potent SaaS security administration application. Acquire insights and visibility to safeguard versus possible security threats. Our cutting-edge technology guarantees protection against publicly-uncovered SaaS facts, around-privileged external customers, third-bash purposes, and much more. Rest quick recognizing your company’s knowledge is in fantastic palms with AppOmni. Check out it currently.
Request a Demo
How SaaS Applications Inherit Permissions by using OAuth Tokens
In quite a few companies, the SaaS applications (and SaaS-to-SaaS connections) capitalize on OAuth access tokens both at the point of preliminary link and throughout their lifecycle. The procedure ordinarily follows these methods:
- A consumer has been authenticated into an business SaaS application, regardless of whether by using basic authentication or powerful zero belief authentication. They’re now in the SaaS cloud.
- That consumer desires to conserve time toggling concerning their task management tool and paperwork, spreadsheets, and e-mails. Appropriately, they research for methods to streamline their do the job. That lookup qualified prospects to a preferred challenge management SaaS plug-in, possibly with a absolutely free demo, and the person decides to try out it.
- The user starts the installation and clicks on “Certainly” to a prompt authorizing study-produce obtain to knowledge in a major SaaS system like an office environment productiveness suite, and the info affiliated with it. There are no tiers of unique permission rights for the person to decide on.
- An OAuth token is established by the place of work efficiency suite. This token allows the job administration application and workplace efficiency suite to retain API-centered cloud-to-cloud communication without the user having to log in and authenticate consistently.
From this place ahead, the undertaking administration application is frequently related just after the preliminary potent authentication. CASBs and SWGs will not detect this SaaS-to-SaaS connectivity.
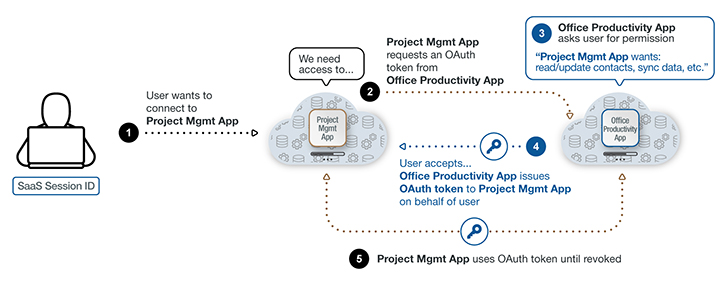 Determine 1: A breakdown of how a SaaS-to-SaaS connection interacts with an OAuth token.
Determine 1: A breakdown of how a SaaS-to-SaaS connection interacts with an OAuth token.
These software tokens are worthwhile simply because they make the venture administration app easily accessible for the user. Sad to say, they are similarly, if not a lot more, useful for attackers in search of an very easily exploitable entry stage into an enterprise SaaS program.
The Arrive at — and Risk — SaaS Apps and SaaS-to-SaaS Connections Existing
If threat actors can efficiently hijack OAuth tokens, they can attain entry into CRMs, code repos, and a lot more. One particular compromised SaaS-to-SaaS connection can offer legitimate, authorized API obtain into a multiplicity of diverse creation SaaS environments and data.
Security and IT groups are overburdened with monitoring and maintaining the configuration options and development of their company SaaS platforms, let by yourself unauthorized SaaS applications. Without any security review, SaaS-to-SaaS connections build most likely susceptible endpoints.
The prevalence of these SaaS-to-SaaS connections is sizeable and often underestimated by IT corporations. According to SaaS security service provider AppOmni:
- The ordinary business business has extra than 42 unique SaaS-to-SaaS apps connected into are living SaaS environments in an company. Just about 50 percent of these apps were being related directly by end-people, not by IT groups.
- Approximately half of these 42 connected applications have not been utilized in the final 6 months. Whether or not energetic or dormant, connected SaaS-to-SaaS applications keep their information entry legal rights.
- Several of these companies have reached a overall of virtually 900 person-to-software connections.
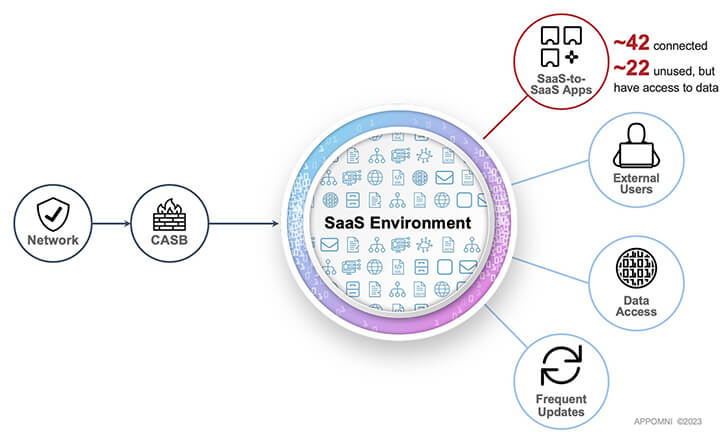 Determine 2: SaaS environments contain many entry details outside classic network and CASB defense.
Determine 2: SaaS environments contain many entry details outside classic network and CASB defense.
As this research demonstrates, the selection of “approved” apps in speak to with potentially sensitive knowledge is infeasible to evaluate and keep an eye on without the proper SaaS security tooling.
Simple Methods for Checking and Securing SaaS Connections
Most Security teams absence the appropriate tooling to attain visibility into SaaS connectivity and the related consumer action. SaaS Security Posture Administration (SSPM) options deal with these concerns by bringing visibility and handle in excess of the SaaS estate.
A Security or IT experienced can, for instance, make the most of SSPM to find out everything operating in Salesforce, alongside with the SaaS apps connected to it. The same is correct for various other SaaS apps applied by the firm.
This added visibility and management in ongoing monitoring of SaaS apps and SaaS-to-SaaS connections lowers attack area risk and permits proactive security manage. If a vulnerability is found out, the Security group can get action, these types of as pinpointing unsanctioned, unsecure, and in excess of-permissioned SaaS apps.
Many thanks to an SSPM solution’s continuous monitoring capabilities, the Security staff is ready to decide a baseline of SaaS exercise to use as a time-in-level frame of reference. Whilst the probable for a SaaS-associated breach can in no way be entirely eliminated, employing SSPM drives down that risk noticeably.
Identified this short article exciting? Follow us on Twitter and LinkedIn to read more exclusive content material we post.
Some parts of this article are sourced from:
thehackernews.com


 Police Escape $1.2m Fine For Secretly Recording Phone Calls
Police Escape $1.2m Fine For Secretly Recording Phone Calls