Ukrainian military services entities are the focus on of a phishing marketing campaign that leverages drone manuals as lures to provide a Go-dependent open up-resource submit-exploitation toolkit known as Merlin.
“Due to the fact drones or Unmanned Aerial Autos (UAVs) have been an integral resource made use of by the Ukrainian armed forces, malware-laced lure files themed as UAVs company manuals have started to area,” Securonix scientists Den Iuzvyk, Tim Peck, and Oleg Kolesnikov claimed in a report shared with The Hacker News.
The cybersecurity organization is monitoring the campaign less than the name STARK#VORTEX.
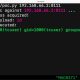
The starting up place of the attack is a Microsoft Compiled HTML Assist (CHM) file that, when opened, operates destructive JavaScript embedded within just one of the HTML web pages to execute PowerShell code developed to get in touch with a remote server to fetch an obfuscated binary.

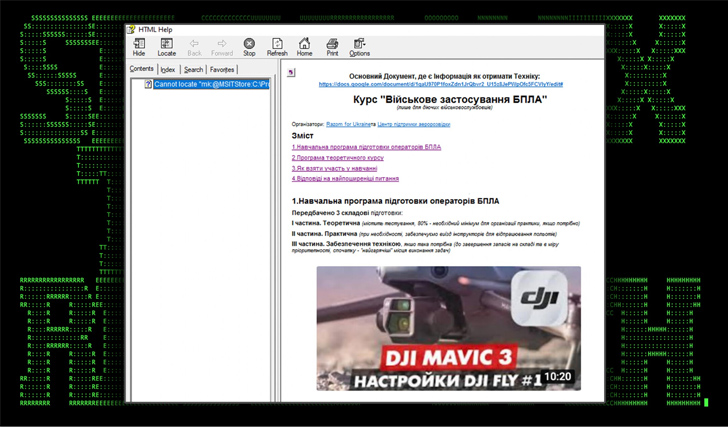
The Windows-based payload is decoded to extract the Merlin Agent, which, in flip, is configured to converse with a command-and-handle (C2) server for put up-exploitation steps, successfully seizing manage about the host.
“Whilst the attack chain is really easy, the attackers leveraged some pretty complicated TTPs and obfuscation procedures in order to evade detection,” the scientists claimed.
This is the first time Ukrainian governing administration corporations have been qualified employing Merlin. In early August 2023, the Laptop Crisis Reaction Workforce of Ukraine (CERT-UA) disclosed a equivalent attack chain that employs CHM files as decoys to infect the computer systems with the open-resource software.
CERT-UA attributed the intrusions to a danger actor it monitors under the identify UAC-0154.
“Information and paperwork applied in the attack chain are really able of bypassing defenses,” the scientists defined.
Upcoming WEBINARFight AI with AI — Battling Cyber Threats with Future-Gen AI Resources
Ready to deal with new AI-driven cybersecurity problems? Be part of our insightful webinar with Zscaler to deal with the rising danger of generative AI in cybersecurity.
Supercharge Your Expertise
“Generally getting a Microsoft help file in excess of the internet would be viewed as strange. On the other hand, the attackers framed the lure documents to show up as something an unsuspecting victim could be expecting to look in a enable-themed document or file.”
The enhancement comes weeks just after the CERT-UA explained it detected an unsuccessful cyber attack against an unnamed critical electrical power infrastructure facility in the state carried out by the Russian state-sponsored crew identified as APT28.
Uncovered this post attention-grabbing? Stick to us on Twitter and LinkedIn to read additional exceptional material we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Watch the Webinar — AI vs. AI: Harnessing AI Defenses Against AI-Powered Risks
Watch the Webinar — AI vs. AI: Harnessing AI Defenses Against AI-Powered Risks