A critical security vulnerability in the JetBrains TeamCity constant integration and constant deployment (CI/CD) application could be exploited by unauthenticated attackers to realize distant code execution on afflicted methods.
The flaw, tracked as CVE-2023-42793, carries a CVSS score of 9.8 and has been addressed in TeamCity version 2023.05.4 subsequent dependable disclosure on September 6, 2023.
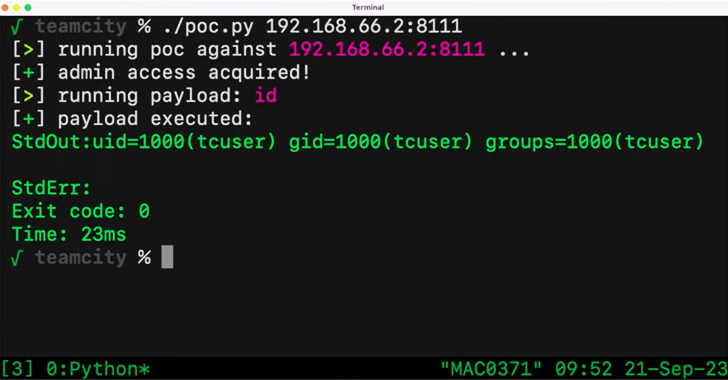
“Attackers could leverage this obtain to steal source code, provider techniques, and private keys, take manage above connected make agents, and poison establish artifacts,” Sonar security researcher Stefan Schiller mentioned in a report last 7 days.

Effective exploitation of the bug could also allow menace actors to obtain the create pipelines and inject arbitrary code, major to an integrity breach and provide chain compromises.
More specifics of the bug have been withheld because of to the actuality that it truly is trivial to exploit, with Sonar noting that it can be probably to be exploited in the wild by threat actors.
JetBrains, in an impartial advisory, has recommended people to enhance as shortly as achievable. It has also released a security patch plugin for TeamCity versions 8. and previously mentioned to especially deal with the flaw.
The disclosure comes as two higher-severity flaws have been disclosed in the Atos Unify OpenScape items that make it possible for a small-privileged attacker to execute arbitrary functioning techniques instructions as root user (CVE-2023-36618) as nicely as an unauthenticated attacker to access and execute several configuration scripts (CVE-2023-36619).
Impending WEBINARFight AI with AI — Battling Cyber Threats with Next-Gen AI Instruments
Ready to deal with new AI-pushed cybersecurity challenges? Be part of our insightful webinar with Zscaler to address the expanding risk of generative AI in cybersecurity.
Supercharge Your Skills
The flaws were being patched by Atos in July 2023.
Above the previous several months, Sonar has also printed information about critical cross-internet site scripting (XSS) vulnerabilities impacting encrypted email options, including Proton Mail, Skiff, and Tutanota, that could have been weaponized to steal emails and impersonate victims.
Identified this short article intriguing? Stick to us on Twitter and LinkedIn to go through much more unique material we post.
Some parts of this article are sourced from:
thehackernews.com

 Ukrainian Military Targeted in Phishing Campaign Leveraging Drone Manuals
Ukrainian Military Targeted in Phishing Campaign Leveraging Drone Manuals