Two China-linked superior persistent menace (APT) groups have been noticed focusing on entities and member countries affiliated with the Association of Southeast Asian Nations (ASEAN) as part of a cyber espionage campaign over the earlier 3 months.
This consists of the menace actor acknowledged as Mustang Panda, which has been lately connected to cyber attacks versus Myanmar as properly as other Asian international locations with a variant of the PlugX (aka Korplug) backdoor dubbed DOPLUGS.
Mustang Panda, also named Camaro Dragon, Earth Preta, and Stately Taurus, is believed to have targeted entities in Myanmar, the Philippines, Japan and Singapore, targeting them with phishing e-mail made to provide two malware deals.
“Risk actors developed malware for these packages on March 4-5, 2024, coinciding with the ASEAN-Australia Exclusive Summit (March 4-6, 2024),” Palo Alto Networks Device 42 claimed in a report shared with The Hacker News.
Just one of the malware package is a ZIP file that contains in it an executable (“Chatting_Factors_for_China.exe”), that when released, masses a DLL file (“KeyScramblerIE.dll”) and in the end deploys a regarded Mustang Panda malware known as PUBLOAD, a downloader beforehand utilized to fall PlugX.
It truly is worthy of pointing out right here that the binary is a renamed copy of a legit program termed KeyScrambler.exe which is vulnerable to DLL facet-loading.
The second package, on the other hand, is a screensaver executable (“Take note PSO.scr”) that’s applied to retrieve following-stage malicious code from a distant IP handle, like a benign application signed by a video clip recreation organization renamed as WindowsUpdate.exe and a rogue DLL that is introduced using the identical approach as prior to.

“This malware then attempts to build a connection to www[.]openservername[.]com at 146.70.149[.]36 for command-and-regulate (C2),” the researchers said.
Unit 42 mentioned it also detected network visitors between an ASEAN-affiliated entity and the C2 infrastructure of a next Chinese APT group, suggesting a breach of the victim’s ecosystem. This unnamed menace action cluster has been attributed to very similar assaults concentrating on Cambodia.
“These styles of strategies continue to reveal how businesses are targeted for cyber espionage functions, the place nation-condition affiliated menace teams accumulate intelligence of geopolitical interests in just the location,” the researchers mentioned.
Earth Krahang Emerges in Wild
The conclusions arrive a 7 days immediately after Trend Micro drop mild on a new Chinese threat actor recognised as Earth Krahang that has targeted 116 entities spanning 35 countries by leveraging spear-phishing and flaws in general public-experiencing Openfire and Oracle servers to deliver bespoke malware this sort of as PlugX, ShadowPad, ReShell, and DinodasRAT (aka XDealer).
The earliest attacks date again to early 2022, with the adversary leveraging a combination of techniques to scan for sensitive facts.
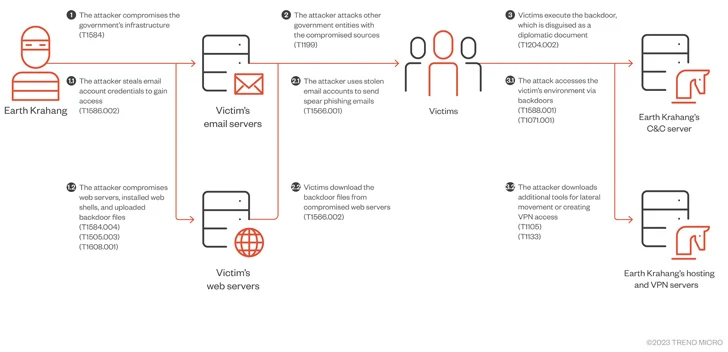
Earth Krahang, which has a robust target in Southeast Asia, also displays some amount of overlap with yet another China-nexus risk actor tracked as Earth Lusca (aka RedHotel). Equally the intrusion sets are most likely managed by the exact menace actor and connected to a Chinese federal government contractor referred to as I-Shortly.
“1 of the risk actor’s favored strategies consists of utilizing its malicious obtain to authorities infrastructure to attack other govt entities, abusing the infrastructure to host malicious payloads, proxy attack website traffic, and deliver spear-phishing e-mail to authorities-similar targets using compromised govt email accounts,” the firm explained.
“Earth Krahang also works by using other tactics, such as developing VPN servers on compromised general public-experiencing servers to set up access into the non-public network of victims and doing brute-pressure assaults to acquire email credentials. These credentials are then made use of to exfiltrate victim emails.”
The I-Soon Leaks and the Shadowy Hack-for-employ the service of Scene
Previous thirty day period, a set of leaked files from I-Quickly (aka Anxun) on GitHub uncovered how the enterprise sells a wide array of stealers and distant access trojans like ShadowPad and Winnti (aka TreadStone) to multiple Chinese federal government entities. This also encompasses an integrated functions system that is made to carry out offensive cyber strategies and an undocumented Linux implant codenamed Hector.
“The integrated operations platform encompasses both equally interior and external applications and networks,” Bishop Fox claimed. “The internal software is mainly for mission and resource administration. The exterior application is built to carry out cyber functions.”
The obscure hack-for-seek the services of entity has also been implicated in the 2019 POISON CARP marketing campaign aimed at Tibetan groups and the 2022 hack of Comm100, in addition to attacks concentrating on overseas governments and domestic ethnic minorities to acquire valuable information and facts, some of which are carried out independently on their have in hopes of landing a govt consumer.
“The information leak has supplied uncommon perception into how the Chinese governing administration outsources components of its cyber functions to private third-celebration businesses, and how these organizations get the job done with just one one more to satisfy these demands,” ReliaQuest noted.

Cybersecurity business Recorded Long run, in its own investigation, explained the leak unravels the “operational and organizational ties” involving the corporation and a few different Chinese condition-sponsored cyber teams this kind of as RedAlpha (aka Deepcliff), RedHotel, and POISON CARP.
“It supplies supporting proof with regards to the very long-suspected existence of ‘digital quartermasters’ that supply abilities to multiple Chinese point out-sponsored groups.”
It also said the overlaps counsel the presence of many sub-teams targeted on certain missions in just the exact same firm. I-Soon’s victimology footprint spreads to at the very least 22 international locations, with govt, telecommunications, and education representing the most specific sectors.
Also, the publicized paperwork ensure that Tianfu Cup – China’s individual take on the Pwn2Possess hacking contest – functions as a “vulnerability feeder program” for the governing administration, letting it to stockpile zero-day exploits and devise exploit code.
“When the Tianfu Cup submissions are not already complete exploit chains, the Ministry of General public Security disseminates the evidence of concept vulnerabilities to non-public companies to even further exploit these evidence-of-strategy abilities,” Margin Investigation stated.
“China’s vulnerability disclosure necessity is one particular component of the puzzle of how China stockpiles and weaponizes vulnerabilities, environment in stone the surreptitious collection supplied by Tianfu Cup in previous several years.”
The supply of the leak is currently not identified, despite the fact that two staff of I-Before long instructed The Linked Push that an investigation is ongoing in collaboration with regulation enforcement. The firm’s web site has due to the fact absent offline.
“The leak presents some of the most concrete specifics viewed publicly to date, revealing the maturing character of China’s cyber espionage ecosystem,” SentinelOne’s Dakota Cary and Aleksandar Milenkoski mentioned. “It shows explicitly how governing administration concentrating on necessities push a aggressive market of unbiased contractor hackers-for-use.”
Discovered this short article appealing? Abide by us on Twitter and LinkedIn to study a lot more exceptional information we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Malicious NuGet Package Linked to Industrial Espionage Targets Developers
Malicious NuGet Package Linked to Industrial Espionage Targets Developers