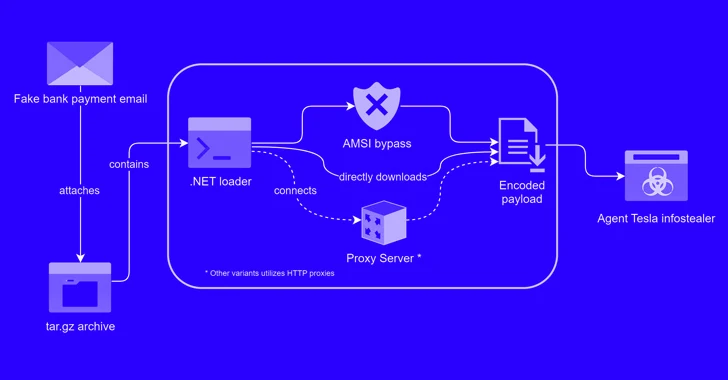
A new phishing marketing campaign has been noticed leveraging a novel loader malware to deliver an details stealer and keylogger termed Agent Tesla.
Trustwave SpiderLabs explained it identified a phishing email bearing this attack chain on March 8, 2024. The information masquerades as a bank payment notification, urging the consumer to open up an archive file attachment.
The archive (“Lender Handlowy w Warszawie – dowód wpłaty_pdf.tar.gz”) conceals a destructive loader that activates the procedure to deploy Agent Tesla on the compromised host.
“This loader then used obfuscation to evade detection and leveraged polymorphic habits with elaborate decryption procedures,” security researcher Bernard Bautista mentioned in a Tuesday examination.
“The loader also exhibited the capacity to bypass antivirus defenses and retrieved its payload utilizing certain URLs and user brokers leveraging proxies to further obfuscate site visitors.”
The tactic of embedding malware in seemingly benign data files is a tactic that has been regularly employed by risk actors to trick unsuspecting victims into triggering the infection sequence.

The loader utilized in the attack is published in .NET, with Trustwave getting two distinct variants that every make use of a various decryption schedule to access its configuration and ultimately retrieve the XOR-encoded Agent Tesla payload from a remote server.
In an exertion to evade detection, the loader is also intended to bypass the Windows Antimalware Scan Interface (AMSI), which offers the skill for security computer software to scan information, memory, and other info for threats.
It achieves this by “patching the AmsiScanBuffer perform to evade malware scanning of in-memory information,” Bautista stated.
The last period will involve decoding and executing Agent Tesla in memory, permitting the danger actors to stealthily exfiltrate sensitive information by way of SMTP making use of a compromised email account associated with a legitimate security program provider in Turkey (“merve@temikan[.]com[.]tr”).
The approach, Trustwave claimed, not only does not raise any purple flags, but also affords a layer of anonymity that helps make it tougher to trace the attack back to the adversary, not to mention preserve the hard work of obtaining to established up devoted exfiltration channels.
“[The loader] employs strategies like patching to bypass Antimalware Scan Interface (AMSI) detection and dynamically load payloads, ensuring stealthy execution and reducing traces on disk,” Bautista said. “This loader marks a notable evolution in the deployment ways of Agent Tesla.”
The disclosure will come as BlueVoyant uncovered an additional phishing exercise executed by a cybercrime team termed TA544 that leverages PDFs dressed up as authorized invoices to propagate WikiLoader (aka WailingCrab) and create connections with command-and-management (C2) server that almost completely encompasses hacked WordPress internet sites.
It’s value noting that TA544 also weaponized a Windows security bypass flaw tracked as CVE-2023-36025 in November 2023 to distribute Remcos RAT via a different loader relatives dubbed IDAT Loader, allowing it to seize regulate of contaminated systems.
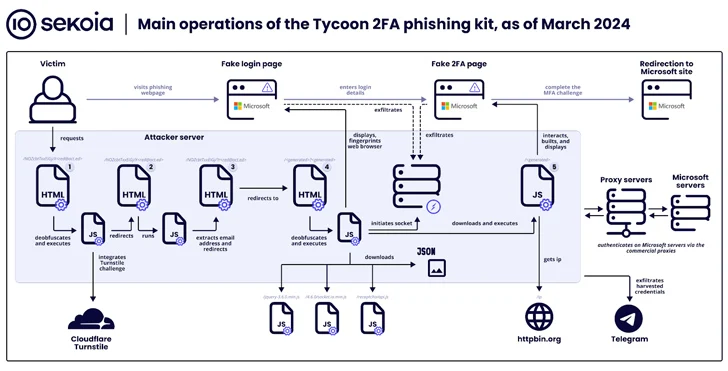
The findings also comply with a surge in the use of a phishing package called Tycoon, which Sekoia reported has “grow to be a single of the most popular [adversary-in-the-middle] phishing kits in excess of the previous couple months, with much more than 1,100 domain names detected involving late October 2023 and late February 2024.”

Tycoon, publicly documented by Trustwave past month, permits cyber criminals to goal consumers of Microsoft 365 with phony login web pages to seize their credentials, session cookies, and two-variable authentication (2FA) codes. It’s identified to be active because at minimum August 2023, with the service offered through non-public Telegram channels.
The phishing package is noteworthy for incorporating comprehensive website traffic filtering solutions to thwart bot exercise and analysis attempts, demanding web page website visitors to full a Cloudflare Turnstile challenge before redirecting end users to a credential harvesting page.
Tycoon also shares operational and structure-level similarities with the Dadsec OTT phishing package, increasing the risk that the developers experienced obtain to and tweaked the resource code of the latter to go well with their desires. This is supported by the simple fact that Dadsec OTT had its supply code leaked in Oct 2023.
“The developer enhanced stealth capabilities in the most modern model of the phishing kit,” Sekoia explained. “The recent updates could reduce the detection charge by security products and solutions of the Tycoon 2FA phishing pages and the infrastructure. Additionally, its ease of use and its somewhat very low price tag make it very well-known among the menace actors.”
Located this posting attention-grabbing? Comply with us on Twitter and LinkedIn to go through extra unique information we put up.
Some parts of this article are sourced from:
thehackernews.com

 Two Chinese APT Groups Ramp Up Cyber Espionage Against ASEAN Countries
Two Chinese APT Groups Ramp Up Cyber Espionage Against ASEAN Countries