The Android banking fraud malware recognised as SharkBot has reared its head at the time once more on the formal Google Participate in Shop, posing as file managers to bypass the application marketplace’s constraints.
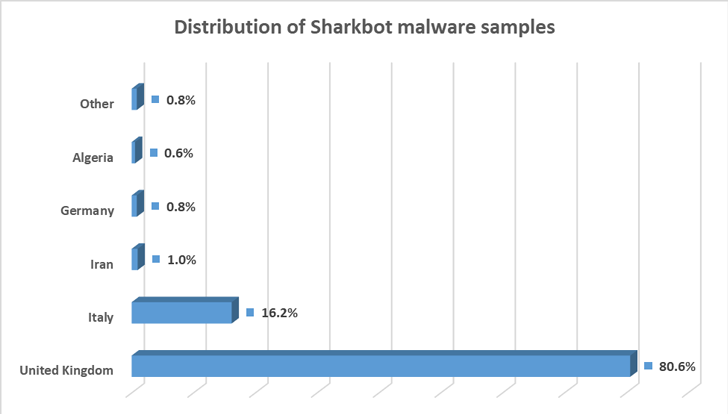
A the vast majority of the consumers who downloaded the rogue applications are positioned in the U.K. and Italy, Romanian cybersecurity organization Bitdefender explained in an investigation revealed this week.
SharkBot, initially found towards the finish of 2021 by Cleafy, is a recurring cell danger distributed both of those on the Google Enjoy Keep and other third-occasion application merchants.
A person of the trojan’s key aims is to initiate dollars transfers from compromised units by way of a system known as “Automatic Transfer Method” (ATS), in which a transaction triggered by way of a banking application is intercepted to swap the payee account with an actor-managed account in the qualifications.
It really is capable of serving a pretend login overlay when customers endeavor to open reputable banking apps, stealing the credentials in the process.
Generally, this kind of applications provide seemingly harmless features, masquerading as antivirus application and cleaners to sneak into Google Play Retail outlet. But they also double up as droppers that, at the time set up on the gadget, can fetch the malware payload.
The dropper applications, now taken down, are down below –
- X-File Supervisor (com.victorsoftice.llc) – 10,000+ downloads
- FileVoyager (com.potsepko9.FileManagerApp) – 5,000+ downloads
- LiteCleaner M (com.ltdevelopergroups.litecleaner.m) – 1,000+ downloads
LiteCleaner M is however offered for down load from a third-social gathering app retail outlet termed Apksos, which also residences a fourth SharkBot artifact by the title “Phone Aid, Cleaner, Booster” (com.sidalistudio.developer.application).
The X-File Manager app, which is only available to users in Italy, attracted in excess of 10,000 downloads prior to it was taken off. With Google steadily clamping down on permission abuse, the danger actor’s alternative of using a file supervisor as a lure is not stunning.
That is since Google’s Developer Program Policy restricts the permission to set up exterior deals (Ask for_Set up_Deals) to a handful of application groups: web browsers, instantaneous messengers that support attachments, file administrators, business unit management, backup and restore, and unit transfer.
Invariably, this permission is abused to obtain and put in malware from a distant server. Some of the targeted lender apps include Lender of Eire, Lender of Scotland, Barclays, BNL, HSBC U.K., Lloyds Financial institution, Metro Lender, and Santander.
“The application [i.e., the dropper] performs anti-emulator checks and targets users from Great Britain and Italy by verifying if the SIM ISO corresponds with IT or GB,” Bitdefender researchers claimed.
Buyers who have put in the aforementioned applications are advisable to delete them and change their financial institution account passwords straight away. People are also suggested to permit Perform Shop Defend, and scrutinize app scores and reviews prior to downloading them.
Discovered this post fascinating? Abide by THN on Facebook, Twitter and LinkedIn to read far more exceptional content we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Black Basta Ransomware Gang Actively Infiltrating U.S. Companies with Qakbot Malware
Black Basta Ransomware Gang Actively Infiltrating U.S. Companies with Qakbot Malware