Corporations based in the U.S. have been at the obtaining stop of an “aggressive” Qakbot malware marketing campaign that sales opportunities to Black Basta ransomware infections on compromised networks.
“In this most recent campaign, the Black Basta ransomware gang is applying QakBot malware to make an first position of entry and go laterally inside of an organization’s network,” Cybereason scientists Joakim Kandefelt and Danielle Frankel explained in a report shared with The Hacker Information.
Black Basta, which emerged in April 2022, follows the tried out-and-analyzed solution of double extortion to steal sensitive knowledge from qualified providers and use it as leverage to extort cryptocurrency payments by threatening to launch the stolen details.
This is not the to start with time the ransomware crew has been observed employing Qakbot (aka QBot, QuackBot, or Pinkslipbot). Last month, Development Micro disclosed comparable assaults that entailed the use of Qakbot to produce the Brute Ratel C4 framework, which, in turn, was leveraged to drop Cobalt Strike.
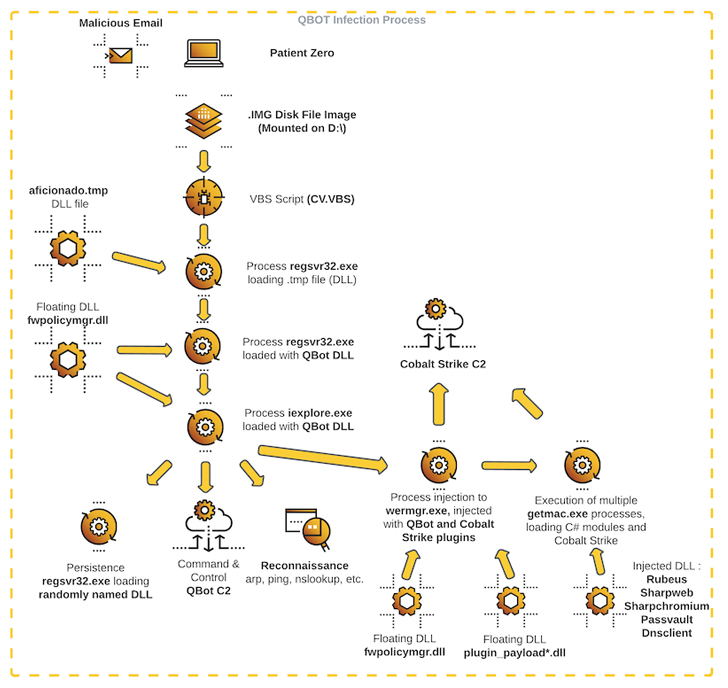
The intrusion exercise noticed by Cybereason cuts out Brute Ratel C4 from the equation, alternatively utilizing Qakbot to specifically distribute Cobalt Strike on quite a few machines in the infected natural environment.
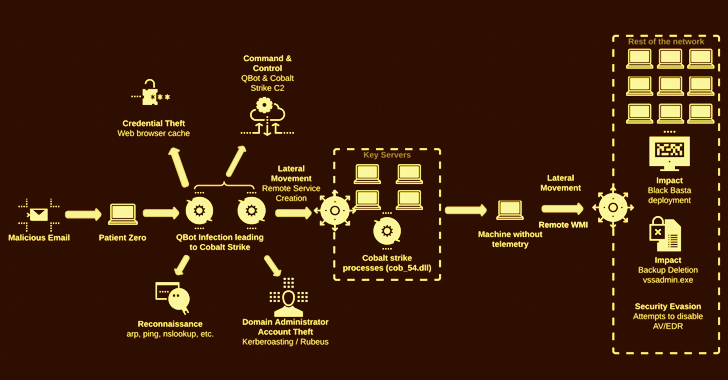
The attack chain commences with a spear-phishing email bearing a malicious disk picture file that, when opened, kickstarts the execution of Qbot, which, for its element, connects to a remote server to retrieve the Cobalt Strike payload.
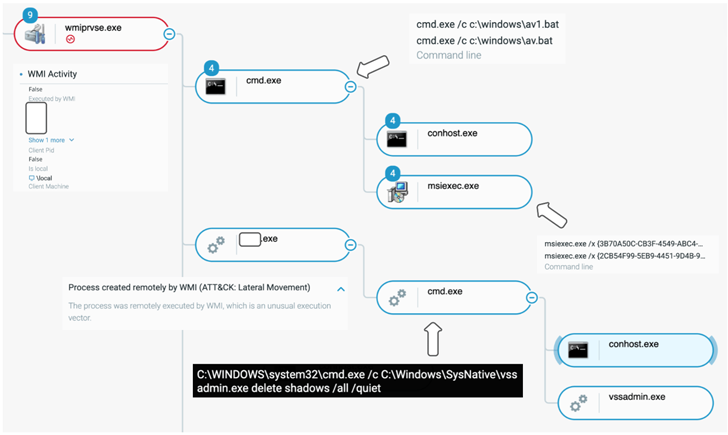
At this stage, credential harvesting and lateral motion functions are carried out to put the purple staff framework on various servers, right before breaching as quite a few endpoints as attainable utilizing the gathered passwords and launching the Black Basta ransomware.
“The risk actor attained domain administrator privileges in a lot less than two hrs and moved to ransomware deployment in fewer than 12 hours,” the researchers observed, incorporating about 10 unique customers ended up impacted by the fresh new established of assaults in the past two weeks.
In two scenarios spotted by the Israeli cybersecurity corporation, the intrusions not only deployed the ransomware but also locked the victims out of their networks by disabling the DNS services in a bid to make a recovery far more challenging.
Black Basta continues to be a very active ransomware actor. In accordance to knowledge collected by Malwarebytes, Black Basta effectively qualified 25 companies in October 2022 alone, placing it guiding LockBit, Karakurt, and BlackCat.
Identified this write-up exciting? Comply with THN on Facebook, Twitter and LinkedIn to study additional distinctive material we put up.
Some parts of this article are sourced from:
thehackernews.com

 Razer's Black Friday deals knock $800 off the Blade 14 gaming laptop
Razer's Black Friday deals knock $800 off the Blade 14 gaming laptop