When you roll out a security item, you think it will satisfy its function. However, even so, this often turns out not to be the situation. A new report, developed by Osterman Research and commissioned by Silverfort, reveals that MFA (Multi-Component Authentication) and PAM (Privileged Entry Management) remedies are practically never ever deployed comprehensively enough to provide resilience to id threats. As effectively, provider accounts – which are normally past the scope of defense of these controls – are alarmingly exposed to destructive compromise. These results and numerous extra can be located in “The Condition of the Identification Attack Floor: Insights Into Critical Safety Gaps,” the initial report that analyzes organizational resilience to identity threats.
What is the “Identity Attack Area”?
The identity attack surface area is any organizational useful resource that can be accessed by means of username and password. The main way that attackers concentrate on this attack surface area is by way of the use of compromised consumer qualifications. In this way, the id attack surface area differs substantially from other attack surfaces. When focusing on endpoints, for instance, attackers have to produce progressive malware and zero-day exploits. But in the planet of id the default attack tool is reputable usernames and passwords. And with an believed 24B username-password mixtures available on the Dark Web, this indicates the only function attackers need to have to do is attain the preliminary access.
But I Have MFA and PAM in Spot to Avert Attacks
Do you, though? In accordance to the report, which summarizes results from 600 identity security experts surveyed all-around the entire world, the vast vast majority of corporations have MFA and PAM solutions in place yet continue being uncovered to assaults. Here is why:
Less than 7% of organizations have MFA safety for the greater part of their critical resources
One particular of the issues the survey asked was: What proportion of the adhering to means and accessibility methods are you at the moment in a position to safeguard with MFA?
- Desktop logins (e.g. Windows, Mac)
- VPN and other remote relationship approaches
- RDP
- Command-line remote access (e.g. PowerShell, PsExec)
- SSH
- Homegrown and legacy applications
- IT infrastructure (e.g. management consoles)
- VDI
- Virtualization platforms and hypervisors (e.g. VMware, Citrix)
- Shared network drives
- OT programs
This graph summarizes the success:

These figures indicate a critical hole, due to the fact a source with out MFA is a source that an adversary can seamlessly obtain using compromised credentials. Translating this to a real-everyday living scenario, a menace actor using command-line software that’s not secured with MFA – this sort of as PsExec or Distant PowerShell – will encounter no hurdles when transferring throughout a network in buy to plant a ransomware payload on a number of machines.
Only 10.2% of corporations have a fully onboarded PAM remedy
PAM solutions are notorious for lengthy, complicated deployments, but how terrible is it seriously? The report reveals the solution: It can be bad. In this article is an aggregation of respondents’ responses to the problem “Where are you in your PAM implementation journey?”

As you can see, most businesses are stuck someplace along their PAM journey, which signifies at least some of their privileged buyers are uncovered to assaults. And preserve in brain that admin consumers are an attackers’ speediest path to your crown jewels. Failing to defend all of them is a risk no business can afford to overlook.
78% of corporations can not protect against malicious entry with compromised assistance accounts
Support accounts are a effectively-acknowledged blind location. Because these non-human accounts are typically really privileged yet can not be secured by MFA – as effectively as the fact that they are commonly undocumented and thus unmonitored – they are a key target for adversaries.
Right here are the responses to the question, “How self-confident are you in your capacity to reduce attackers from utilizing company accounts for malicious entry in your setting?”
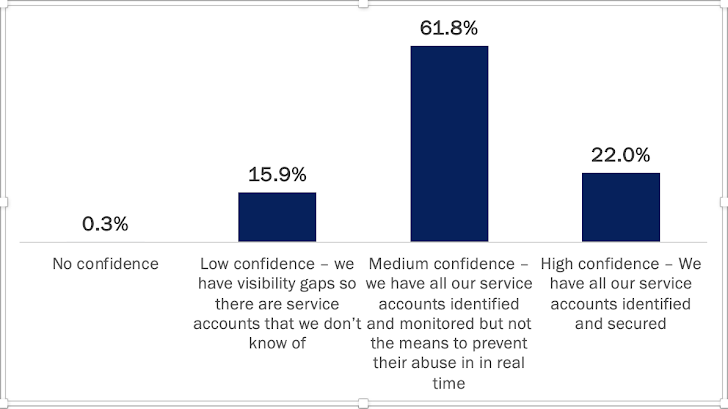
Notice that the time period “medium” here is a little bit misleading, considering that the absence of actual-time avoidance in essence voids the security price of currently being in a position to detect an account’s compromise.
How Perfectly Are You Protecting Your Environment’s Identity Attack Surface? Use the Maturity Design
The report goes further than pointing out weaknesses and gaps — it gives a practical scoring model that, centered on aggregated results throughout all the identity safety features, can expose your level of resilience to id threats.
The report discovered that incredibly couple businesses – as reduced as 6.6% – have a disciplined and carried out identification defense strategy in put. But use this model to answer the exact same issues and see how your organization stacks up, and also what steps you want to consider.
All set to see how resilient you are to identity threats? Entry the report right here.
Located this report fascinating? Observe us on Twitter and LinkedIn to read additional unique written content we publish.
Some parts of this article are sourced from:
thehackernews.com

 Hook: New Android Banking Trojan That Expands on ERMAC’s Legacy
Hook: New Android Banking Trojan That Expands on ERMAC’s Legacy