A novel cloud-indigenous cryptojacking procedure has set its eyes on unusual Amazon Web Providers (AWS) choices these as AWS Amplify, AWS Fargate, and Amazon SageMaker to illicitly mine cryptocurrency.
The malicious cyber exercise has been codenamed AMBERSQUID by cloud and container security organization Sysdig.
“The AMBERSQUID operation was in a position to exploit cloud providers with out triggering the AWS need for approval of extra assets, as would be the case if they only spammed EC2 situations,” Sysdig security researcher Alessandro Brucato reported in a report shared with The Hacker News.
“Concentrating on multiple companies also poses more issues, like incident response, considering the fact that it calls for obtaining and killing all miners in every single exploited provider.”

Sysdig reported it identified the marketing campaign adhering to an analysis of 1.7 million visuals on Docker Hub, attributing it with reasonable self-assurance to Indonesian attackers dependent on the use of Indonesian language in scripts and usernames.
Some of these photographs are engineered to execute cryptocurrency miners downloaded from actor-managed GitHub repositories, whilst other people run shell scripts concentrating on AWS.
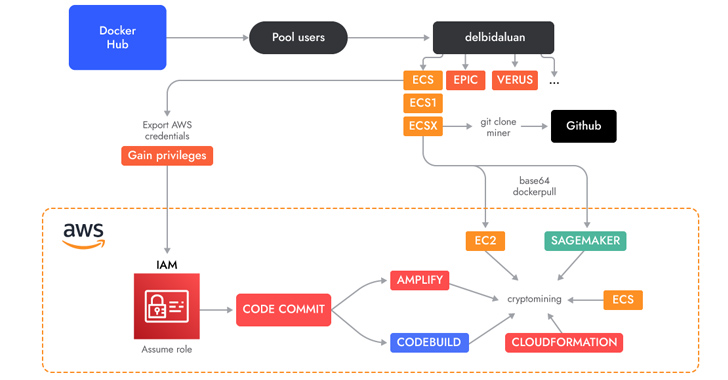
A vital attribute is the abuse of AWS CodeCommit, which is applied to host private Git repositories, to “create a non-public repository which they then utilised in diverse expert services as a supply.”
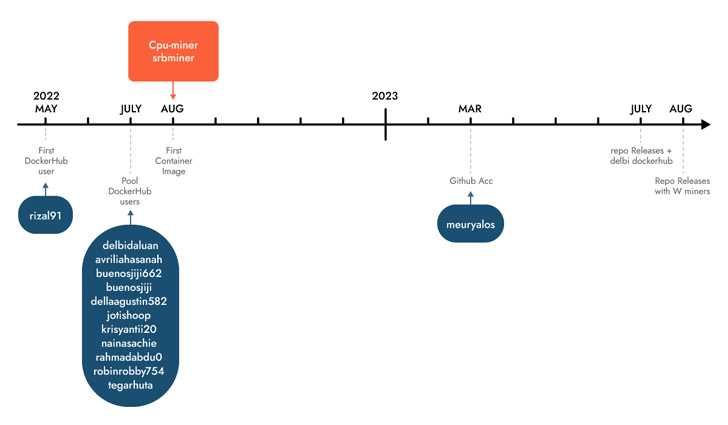
The repository incorporates the resource code of an AWS Amplify app that, in flip, is leveraged by a shell script to generate a Amplify web application and finally launch the cryptocurrency miner.
The menace actors have also been noticed employing shell scripts to accomplish cryptojacking in AWS Fargate and SageMaker situations, incurring substantial compute fees for the victims.
Sysdig believed that AMBERSQUID could final result in losses of far more than $10,000 for every working day if it’s scaled to target all AWS locations. A further examination of the wallet addresses applied reveals that the attackers have gained much more than $18,300 in revenues to date.
Impending WEBINARIdentity is the New Endpoint: Mastering SaaS Security in the Fashionable Age
Dive deep into the potential of SaaS security with Maor Bin, CEO of Adaptive Protect. Find why id is the new endpoint. Protected your location now.
Supercharge Your Expertise
This is not the very first time Indonesian risk actors have been joined to cryptojacking campaigns. In May 2023, Permiso P0 Labs in depth an actor named GUI-vil which was noticed leveraging Amazon Web Companies (AWS) Elastic Compute Cloud (EC2) circumstances to carry out crypto mining operations.
“Whilst most monetarily enthusiastic attackers target compute products and services, these kinds of as EC2, it is important to bear in mind that many other expert services also offer obtain to compute resources (albeit it more indirectly),” Brucato explained.
“It is easy for these solutions to be forgotten from a security perspective considering the fact that there is fewer visibility in comparison to that accessible by runtime risk detection.”
Located this report exciting? Comply with us on Twitter and LinkedIn to browse much more exclusive written content we put up.
Some parts of this article are sourced from:
thehackernews.com

 Think Your MFA and PAM Solutions Protect You? Think Again
Think Your MFA and PAM Solutions Protect You? Think Again