There is a seemingly under no circumstances-ending quest to come across the right security instruments that provide the right abilities for your firm.
SOC groups are inclined to commit about a 3rd of their day on situations that you should not pose any threat to their corporation, and this has accelerated the adoption of automatic alternatives to just take the spot of (or augment) inefficient and cumbersome SIEMs.
With an approximated 80% of these threats remaining prevalent across most companies, modern SOCs are ready to confidently count on automation to include this substantial percentage of risk alerts.
But, although it is legitimate that automation can drastically make improvements to the effectiveness and efficiency of security groups, it will never be equipped to deal with all detection and reaction use instances infallibly.
In the not too long ago unveiled GigaOm Radar for Autonomous Security Functions Heart (SOC), they accurately state that “the SOC will not—and ought to not—be thoroughly autonomous.”
As much more distributors try to challenge the dominant players in the SIEM classification, need is raising for solutions that give automation, which can go over 80%, when also supplying customization abilities to deal with bespoke use conditions – the remaining 20%.
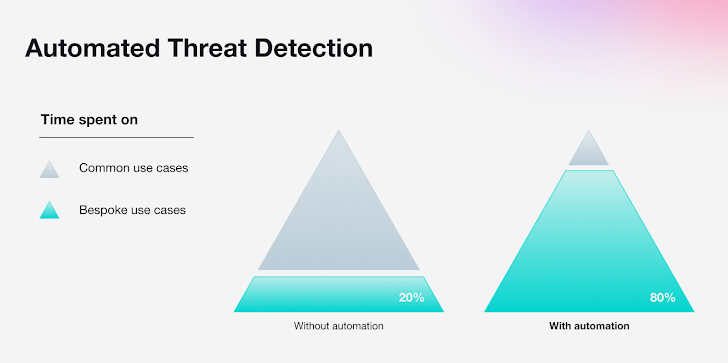 Automation can absolutely free up worthwhile time for security groups, so they can spend the the vast majority of their time on use scenarios unique to their organization.
Automation can absolutely free up worthwhile time for security groups, so they can spend the the vast majority of their time on use scenarios unique to their organization.
THE 80%: AUTOMATION
With the continual surge in world-wide details development, corporations are inevitably viewing an uptick in the quantity of alerts managed by security groups.
This may possibly seem to be challenging for overworked security teams, but state-of-the-art seller choices are utilizing automation throughout many stages of the SOC workflow, helping groups increase their pace and success.
The four key phases the place we are seeing automation are:
- Info Ingestion and Normalization: Automating info ingestion and normalization enables groups to system huge quantities of info from diverse resources efficiently, creating a sturdy basis for subsequent automatic processes.
- Detection: Transferring the duty of building a significant portion of detection guidelines lets security analysts to concentrate on threats distinctive to their firm or industry section.
- Investigation: Automation can relieve the load of handbook and repetitive jobs, expediting investigation and triage procedures.
- Response: Computerized responses to acknowledged and uncovered threats facilitate swift and correct mitigation. This can incorporate connectivity to circumstance administration, SOAR options, ITSM, and so on.
Present day SIEM substitution suppliers, these types of as Hunters, leverage pre-built detection policies, integrate risk intelligence feeds, and routinely enrich and cross-correlate sales opportunities. These automatic procedures ease large quantities of laborous workloads, empowering security groups to conveniently control the significant bulk of alerts.
 Automatic enrichment and cross-correlation build comprehensive stories, generating monitoring lateral movements significantly more economical.
Automatic enrichment and cross-correlation build comprehensive stories, generating monitoring lateral movements significantly more economical.
THE 20%: CUSTOMIZATION
Whilst automating the above phases of the workflow have been significant in boosting efficiencies for several SOCs, there will often continue being the want for a specific degree of customization.
Every single organization has bespoke wants and demands depending on market- or business-unique use cases. This suggests that even if automatic and created-in capabilities can deal with 80% of the general use cases and responsibilities, further capabilities are needed to address the remaining 20%.
“Customization” can mean a large amount of unique items, but the principal prerequisite for security teams is that they have both of those the overall flexibility to deal with one of a kind use circumstances and the ability to scale their capabilities. Let us search at a couple of illustrations of use conditions wherever this can be helpful:
- Ingesting customized information resources: every corporation has several details sources they ingest with distinctive log formats. Quite a few distributors may not have pre-built integrations to ingest from every single single details supply, so if a vendor does offer you that capability, it can be a huge elevate. This is particularly for organizations that are presently making use of (or will soon be transferring to) details lakes to maintain knowledge for several applications.
- Detection-as-code: this has grow to be a substantial buzzword in the security sector, but with good explanation. Detection-as-code gives a variety of positive aspects for detection engineers, like enhanced and economical progress lifecycle, and for substantial companies to a lot more successfully manage multi-tenancy environments. If you usually are not common with the notion, detection-as-code utilizes APIs and deployment pipelines to supply sought after auditing capabilities, generating the enhancement lifecycle for security operations a great deal closer to that of conventional software program improvement. This strategy improves processes to assistance groups build bigger-high quality alerts or reuse code in just your group so you never have to establish every single new detector from scratch. It also helps force detection engineering still left in the enhancement lifecycle, eliminating the need to manually test and deploy detectors.
- Scalable organization context: Regardless of whether it be entities with distinct sensitivity degrees (like crown jewels), info from distinct business units or distinct geographies, or siloed info from unique resources, it will take a large amount of time and energy to piece jointly info in a way which is easy to understand and actionable. Leveraging an SIEM option that offers you the means to manage all this via API delivers expanded efficiencies and scalability that not just about every vendor offers.
Conclusion
Constructing out an productive SOC has usually been, and will keep on to be, a nuanced effort.
There is no a person-sizing-matches-all alternative when it comes to security equipment. It is important to give ways for companies to not just customise for their use situations, but it is vital that they are ready to merge this “customization” with the by now current automatic abilities that vendors offer you.
It has turn into a requirement to appear for suppliers that can give equally a palms-on approach to customizing applications, but to do so in a way to bolster the autonomous parts of their offerings.
SIEM replacement suppliers like Hunters, which have been named leaders in GigaOm’s beforehand mentioned report on autonomous SOC, are known for their uncomplicated-to-use and pre-designed abilities. And, to make certain that they serve the desires of security teams, are continuing to increase impressive customization options that permit corporations to tailor their security technique to their unique requirements.
Covering the 80% is important, but addressing the remaining 20% will established your security crew higher than the rest.
Found this report intriguing? Comply with us on Twitter and LinkedIn to browse additional special written content we submit.
Some parts of this article are sourced from:
thehackernews.com


 Alert: ‘Effluence’ Backdoor Persists Despite Patching Atlassian Confluence Servers
Alert: ‘Effluence’ Backdoor Persists Despite Patching Atlassian Confluence Servers