The infamous Russian hackers known as Sandworm focused an electrical substation in Ukraine very last year, creating a transient power outage in Oct 2022.
The conclusions come from Google’s Mandiant, which described the hack as a “multi-function cyber attack” leveraging a novel strategy for impacting industrial command devices (ICS).
“The actor 1st used OT-level dwelling-off-the-land (LotL) approaches to likely vacation the victim’s substation circuit breakers, causing an unplanned power outage that coincided with mass missile strikes on critical infrastructure across Ukraine,” the corporation said.

“Sandworm later performed a 2nd disruptive event by deploying a new variant of CaddyWiper in the victim’s IT natural environment.”
The risk intelligence firm did not reveal the place of the qualified electrical power facility, the duration of the blackout, and the range of folks who were impacted by the incident.
The advancement marks Sandworm’s steady efforts to stage disruptive attacks and compromise the electrical power grid in Ukraine considering that at least 2015 using malware this kind of as Industroyer.
The correct initial vector applied for the cyber-bodily attack is presently unclear, and it can be thought that the risk actor’s use of LotL approaches diminished the time and methods expected to pull it off.
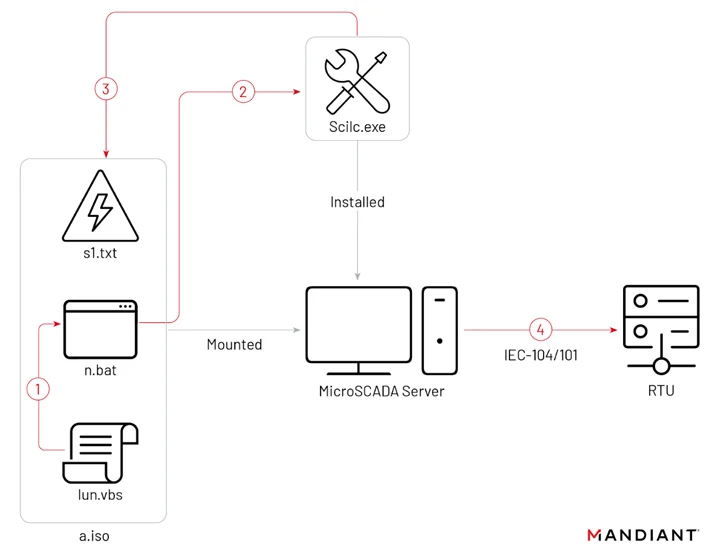
The intrusion is believed to have transpired around June 2022, with the Sandworm actors attaining obtain to the operational technology (OT) setting by means of a hypervisor that hosted a supervisory handle and information acquisition (SCADA) management occasion for the victim’s substation surroundings.
On October 10, 2022, an optical disc (ISO) impression file was employed to start malware capable of switching off substations, resulting in an unscheduled energy outage.

“Two days soon after the OT party, Sandworm deployed a new variant of CaddyWiper in the victim’s IT environment to lead to further more disruption and likely to remove forensic artifacts,” Mandiant claimed.
CaddyWiper refers to a piece of details-wiping malware that to start with came to light in March 2022 in link with the Russo-Ukrainian war.
“This attack represents an rapid danger to Ukrainian critical infrastructure environments leveraging the MicroSCADA supervisory regulate procedure,” the firm reported.
“Offered Sandworm’s international risk action and the all over the world deployment of MicroSCADA goods, asset homeowners globally ought to take motion to mitigate their ways, techniques, and processes towards IT and OT units.”
Identified this article intriguing? Comply with us on Twitter and LinkedIn to go through more exclusive material we submit.
Some parts of this article are sourced from:
thehackernews.com


 The New 80/20 Rule for SecOps: Customize Where it Matters, Automate the Rest
The New 80/20 Rule for SecOps: Customize Where it Matters, Automate the Rest