In 2023, the world-wide common value of a information breach reached $4.45 million. Past the immediate monetary decline, there are long-phrase consequences like diminished buyer belief, weakened model price, and derailed company functions.
In a environment the place the frequency and charge of details breaches are skyrocketing, companies are coming facial area-to-facial area with a severe truth: standard cybersecurity steps may possibly not be reducing it any longer.
Towards this backdrop, enterprises have to discover strategies to fortify their actions to safeguard important knowledge and critical assets. At the heart of this shift lies a important method: continual checking.
Understanding Ongoing Security Monitoring in Cybersecurity
Continual checking is a dynamic tactic that encompasses several tactics to fulfil a multi-layered defense technique. These approaches can contain:
- Risk-Primarily based Vulnerability Management (RBVM):Steady vulnerability assessments throughout your network with remediation prioritization based on the best threats posed.
- External Attack Floor Management (EASM): Ongoing discovery, checking, and evaluation of your exterior publicity, which include domains, websites, hosts, companies, etc.
- Cyber Danger Intelligence:Actionable and centralized danger facts to assist you hold-up with adversaries and deal with electronic risk.
Contrary to level-in-time assessments, which are analogous to having a image of your security posture, continuous checking is like a 24/7 reside stream. It proactively scouts for vulnerabilities, irregularities, misconfigurations, and potential threats, making certain swift detection and response.
Constant Security Checking for Web Applications
Safeguarding enterprise applications really should be a central component of any powerful cybersecurity strategy. Not only are they a tempting focus on for cybercriminals, but they are also significantly hard to protect. In accordance to a recent report, dependent on examination of 3.5 million business belongings, the large vast majority (74%) of internet-exposed web apps containing own identifiable data (PII) are susceptible to a cyberattack.
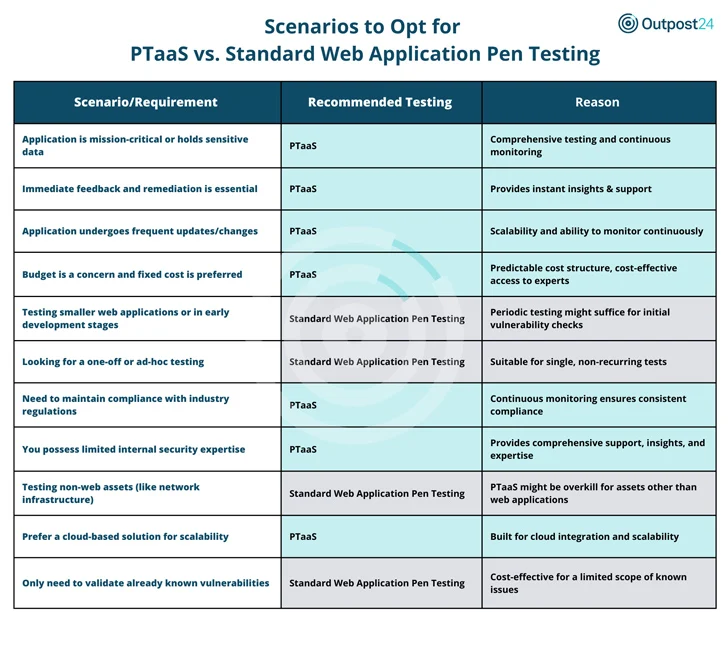
When it will come to safeguarding their web software, corporations typically grapple with a critical choice: a pen testing as a services (PTaaS) remedy or the normal (periodic or advertisement-hoc) pen check. The choice boils down to your organization’s precise desires. Each tools have their merits it can be about aligning the instrument with the endeavor at hand, ensuring you happen to be always in advance in the cybersecurity game.
The Added benefits of PTaaS
- In environments where by apps are very important or take care of delicate data a PTaaS alternative and its steady monitoring is a non-negotiable. It gives ongoing protection from evolving vulnerabilities.
- On the spending plan front, PTaaS delivers a predictable cost model, producing it a price-helpful route to significant-degree security abilities.
- For companies restricted in security manpower, PTaaS fills the gap, supplying sturdy support and direct access to security gurus.
The Added benefits of the Standard Pen Screening
- For newer or lesser web apps, occasional checks may be plenty of, which is where the normal pen examination methods in.
- Have a one-time want, like a certain security verification? typical pen screening is your very best wager. It’s also additional suited for jobs centered on non-web assets, like network infrastructure.
- If you happen to be strictly seeking to validate identified vulnerabilities, conventional pen testing gives a centered, expense-powerful option.
The Broader Landscape of Ongoing Checking
Outpost24 identifies security gaps across your complete attack floor and helps you prioritize vulnerabilities to enhance your cybersecurity posture and decrease publicity.
- Outscan NX (RBVM): Vulnerability management with genuine-globe risk intelligence to focus remediation and minimize small business risk.
- SWAT (PTaaS): Manual screening and automatic scanning with accessibility to security professionals for your agile improvement cycles.
- Sweepatic (EASM): Attack surface discovery and monitoring in real-time with actionable insights.
- Menace Compass (Cyber Menace Intelligence): Targeted and actionable intelligence for speedier menace detection and incident reaction.
The electronic age requires a rethink of our cybersecurity paradigms. The climbing fees and risks involved with facts breaches make it very clear: continuous security monitoring is not just an possibility, it is really a requirement. With the previously mentioned alternatives, Outpost24 features a sturdy toolkit to navigate this new cybersecurity landscape.
Uncovered this article exciting? Adhere to us on Twitter and LinkedIn to browse far more exclusive information we put up.
Some parts of this article are sourced from:
thehackernews.com


 Alert: OracleIV DDoS Botnet Targets Public Docker Engine APIs to Hijack Containers
Alert: OracleIV DDoS Botnet Targets Public Docker Engine APIs to Hijack Containers