Publicly-accessible Docker Motor API situations are staying specific by risk actors as section of a campaign made to co-choose the equipment into a dispersed denial-of-services (DDoS) botnet dubbed OracleIV.
“Attackers are exploiting this misconfiguration to supply a malicious Docker container, created from an image named ‘oracleiv_latest’ and containing Python malware compiled as an ELF executable,” Cado researchers Nate Bill and Matt Muir mentioned.
The malicious exercise starts with attackers employing an HTTP Post request to Docker’s API to retrieve a malicious image from Docker Hub, which, in change, runs a command to retrieve a shell script (oracle.sh) from a command-and-manage (C&C) server.
Oracleiv_hottest purports to be a MySQL impression for docker and has been pulled 3,500 periods to date. In a probably not-so-surprising twist, the graphic also features added guidelines to fetch an XMRig miner and its configuration from the similar server.

That reported, the cloud security firm said it did not observe any proof of cryptocurrency mining performed by the counterfeit container. The shell script, on the other hand, is concise and incorporates functions to carry out DDoS attacks such as slowloris, SYN floods, and UDP floods.
Uncovered Docker circumstances have come to be a lucrative attack focus on in the latest yrs, typically used as conduits for cryptojacking strategies.
“Once a legitimate endpoint is identified, it’s trivial to pull a malicious picture and start a container from it to have out any conceivable objective,” the researchers reported. “Hosting the destructive container in Docker Hub, Docker’s container image library, streamlines this system even further more.”
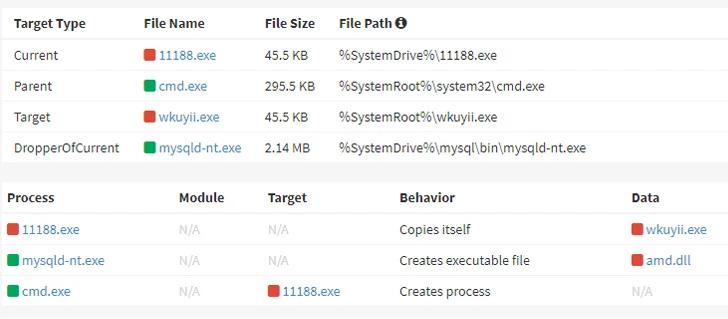
It can be not just Docker, as susceptible MySQL servers have emerged as the target of an additional DDoS botnet malware recognized as Ddostf, according to the AhnLab Security Emergency Response Center (ASEC).
“Although most of the commands supported by Ddostf are equivalent to those people from normal DDoS bots, a distinctive attribute of Ddostf is its means to connect to a newly obtained deal with from the C&C server and execute commands there for a specified period,” ASEC explained.
“Only DDoS commands can be carried out on the new C&C server. This indicates that the Ddostf threat actor can infect a lot of techniques and then market DDoS attacks as a service.”
Compounding issues even more is the emergence of various new DDoS botnets, these types of as hailBot, kiraiBot, and catDDoS that are dependent on Mirai, whose source code leaked in 2016.

“These recently developed Trojan horses possibly introduce new encryption algorithms to hide critical info or much better disguise on their own by modifying the go-stay method and coming up with a lot more covert communication strategies,” cybersecurity enterprise NSFOCUS exposed previous thirty day period.
Yet another DDoS malware that has resurfaced this yr is XorDdos, which infects Linux products and “transforms them into zombies” for abide by-on DDoS assaults from targets of interest.
Palo Alto Networks Unit 42 reported the marketing campaign began in late July 2023, just before peaking all over August 12, 2023.
“Before malware effectively infiltrated a unit, the attackers initiated a scanning system, utilizing HTTP requests to identify opportunity vulnerabilities in their targets,” the firm pointed out. “To evade detection, the menace turns its course of action into a background services that runs independently of the recent person session.”
Uncovered this report intriguing? Observe us on Twitter and LinkedIn to read more special articles we article.
Some parts of this article are sourced from:
thehackernews.com


 CI/CD Risks: Protecting Your Software Development Pipelines
CI/CD Risks: Protecting Your Software Development Pipelines