File Integrity Checking (FIM) is an IT security handle that displays and detects file alterations in laptop or computer devices. It assists companies audit critical documents and method configurations by routinely scanning and verifying their integrity. Most data security benchmarks mandate the use of FIM for firms to ensure the integrity of their information.
IT security compliance entails adhering to relevant regulations, guidelines, regulations, treatments, and standards issued by governments and regulatory bodies such as PCI DSS, ISO 27001, TSC, GDPR, and HIPAA. Failure to comply with these polices can lead to intense outcomes these as cyber breaches, private info decline, economical loss, and reputational harm. Consequently, organizations must prioritize adherence to IT regulations and standards to mitigate pitfalls and safeguard their information units effectively.
The swift pace of technological advancement and a scarcity of proficient cybersecurity gurus lead to compliance challenges. To effectively fulfill these laws, organizations need to strategically plan, allocate methods to cybersecurity initiatives, and carefully classify and secure their information belongings.
Benefits of complying with cybersecurity standards
Compliance with cybersecurity rules and benchmarks is critical for corporations of all measurements. These rules have to have applying precise cybersecurity actions, policies, and processes. By adhering to these expectations, companies assure the transparency and integrity of their cybersecurity methods. Some positive aspects include:
- It assures that businesses have resilient backup and restoration strategies in put. This minimizes disruptions to business enterprise functions and maintains continuity all through a cyber incident or catastrophe, as data saved in backup web sites can be restored.
- It presents a structured framework for controlling hazards throughout various business elements. Businesses can reduce the costs involved with cybersecurity incidents and regulatory non-compliance by subsequent founded methods and controls.
- It safeguards an organization’s track record. Information breaches can substantially impact a company’s track record. Compliance assists safeguard towards this kind of breaches, thereby safeguarding the business’s name.
- It facilitates entry into controlled markets. In healthcare, finance, and retail sectors, it assures regulators that the firm’s IT methods and units meet the essential expectations.
The Wazuh FIM functionality
Wazuh is an open resource security solution that gives unified XDR and SIEM security across several platforms. It protects workloads across on-premises, virtualized, cloud-centered, and containerized environments to deliver corporations with an productive method to cybersecurity. Wazuh presents file integrity checking (FIM) as one particular of its abilities it also provides other capabilities, such as security configuration assessment and menace detection and response.
The Wazuh FIM ability assures the adhering to:
- Serious-time and scheduled file and listing checking.
- Detection of unauthorized file improvements.
- Specifics about what or who built adjustments to details.
FIM, merged with other Wazuh capabilities these kinds of as malware detection, vulnerability detection, and Security Configuration Evaluation (SCA), enhances menace detection, investigation, and remediation. These abilities can support streamline your organization’s security compliance initiatives.
Making certain regulatory compliance making use of the Wazuh FIM ability
End users can configure file integrity checking to meet up with the requirements of IT security compliance criteria appropriate to their business. The Wazuh FIM can be configured to check file addition, deletion, and modification to a file content.
Retaining observe of file changes in just the organization will help process directors and security analysts have group-extensive visibility of these changes and deal with security incidents promptly. After configured, FIM gatherings can be viewed on the Wazuh dashboard.
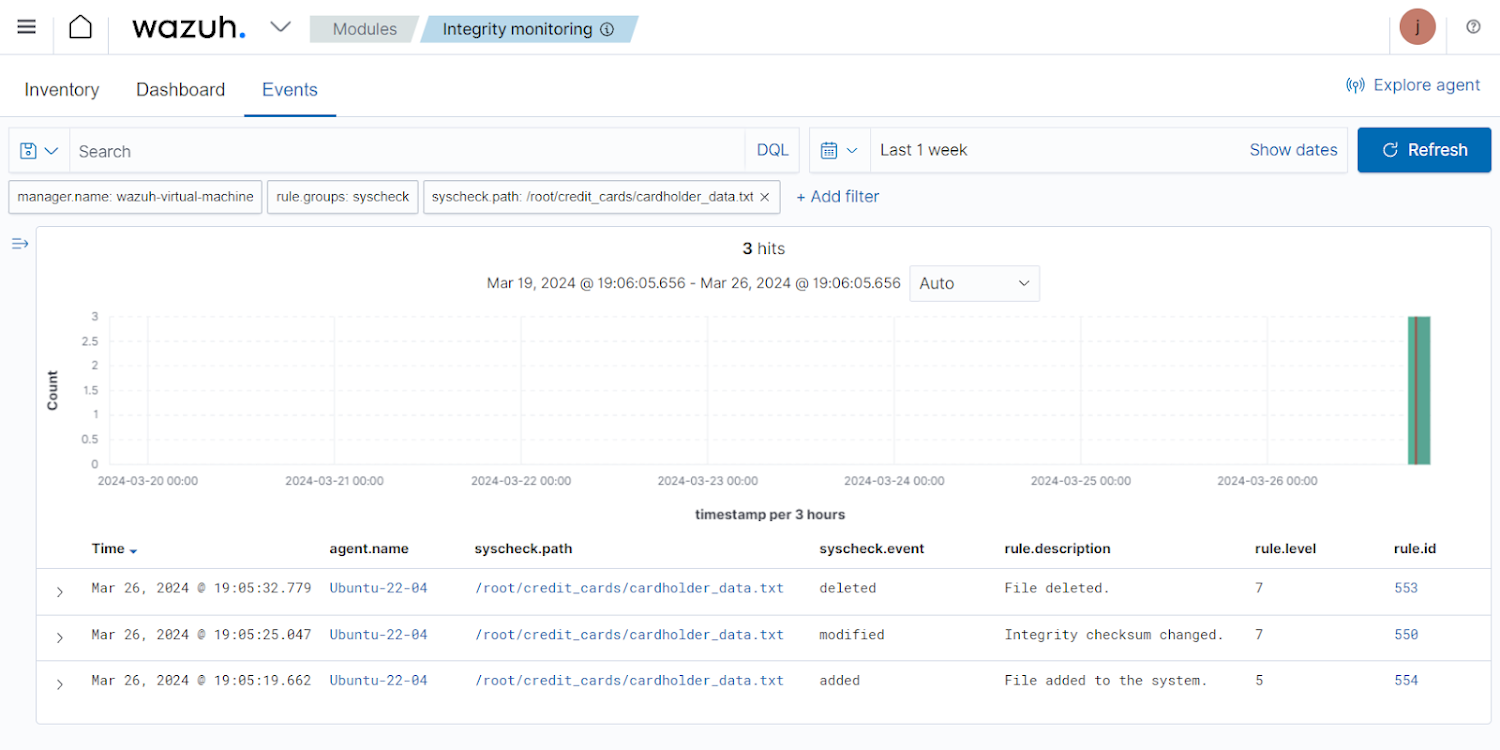 FIM situations in the Wazuh dashboard
FIM situations in the Wazuh dashboard
Checking file integrity and entry
The Wazuh FIM ability runs a baseline scan and outlets the cryptographic checksum and other characteristics of monitored files. When a transform is manufactured to a monitored file, the FIM compares its checksum and characteristics to the baseline. If any discrepancy is recognized, an inform will be triggered. Wazuh file integrity checking capability tracks specifics these types of as the process or user that modified a critical file and when the modifications were built. Employing the Wazuh FIM functionality, businesses can make certain compliance with many sections of regulatory standards this sort of as:
- PCI DSS necessity 11.5.2
- CM-3 of NIST 800-53
- Post 5.1. (f) of GDPR
- Workforce Security §164.308(a)(2) of HIPAA.
For illustration, we can configure the Wazuh FIM to keep an eye on the SSH configuration file /and so forth/ssh/sshd_config file on a Linux endpoint. Malicious actors usually target the SSH configuration file to weaken security by altering port numbers or disabling potent ciphers. The Wazuh FIM can detect unauthorized modifications by checking alterations to this file. The adhering to configuration on a Wazuh agent sets the Wazuh FIM ability to observe the /etc/ssh/sshd_config file on a monitored endpoint:
The impression down below exhibits alerts triggered when alterations are manufactured to the SSH configuration file.
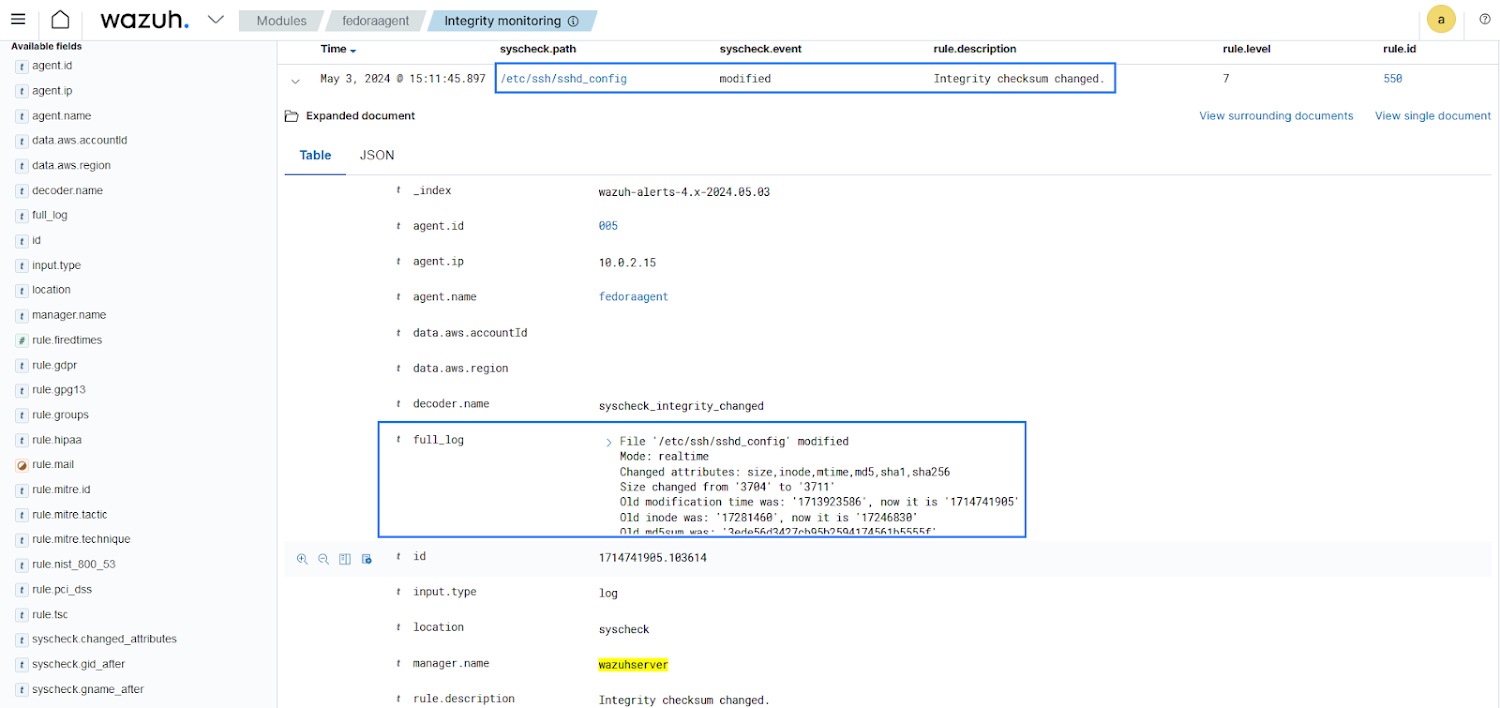 Inform for modification of SSH configuration
Inform for modification of SSH configuration
Equally, the /and so forth/ufw directory normally has configuration files for UFW (Uncomplicated Firewall), a well-known firewall application in Linux. These files outline the regulations analyzing which network website traffic is permitted or blocked on your method. An attacker could modify the UFW principles to open up ports ordinarily closed by default, permitting unauthorized entry to a system or inside network providers.
We can configure the Wazuh FIM to check the /and so on/ufw directory. This is configured by including the configuration down below in the agent configuration file on the monitored endpoint. We also help the attribute whodata, which records the user that improvements a monitored file.
The impression beneath shows alerts induced when alterations are produced to the UFW rule data files.
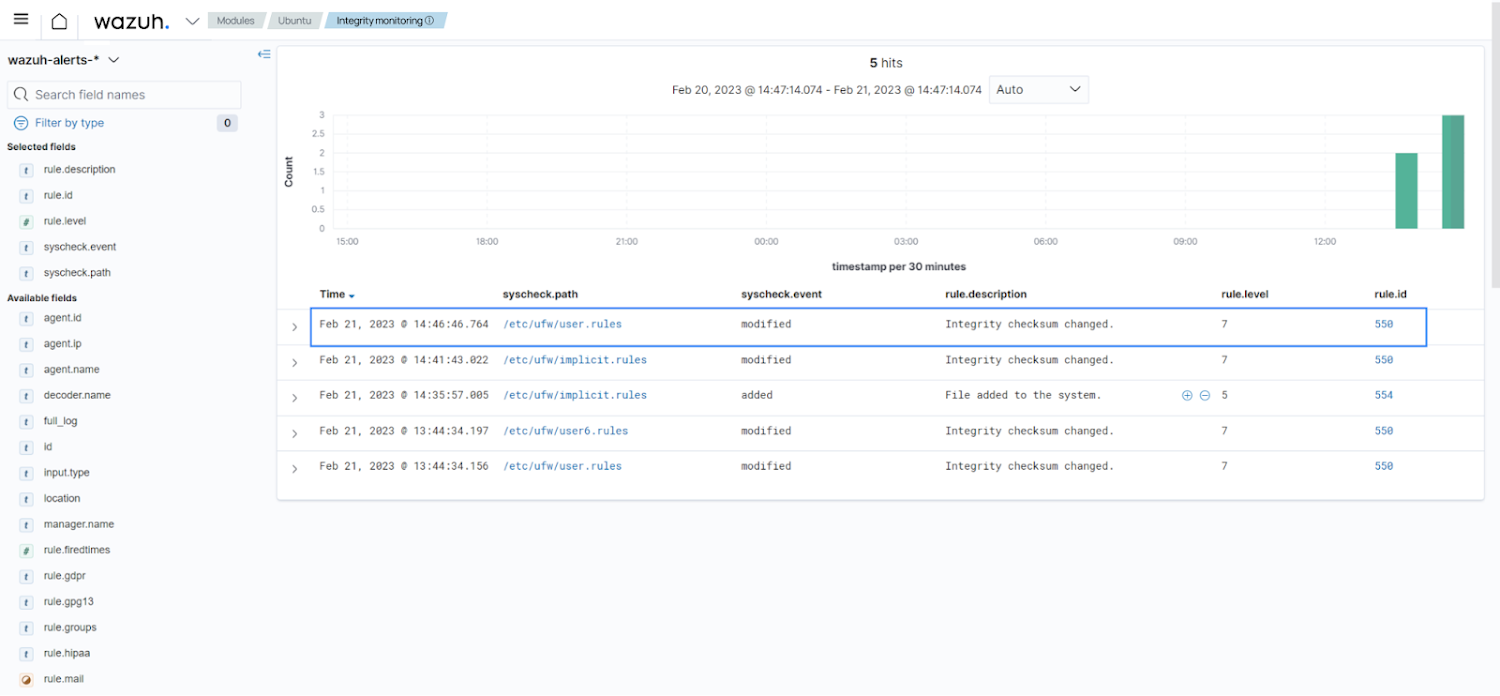 Notify for modification of UFW rule data files
Notify for modification of UFW rule data files
The Wazuh FIM functionality lets you see the consumer and system initiating the improve. The picture beneath demonstrates this information.
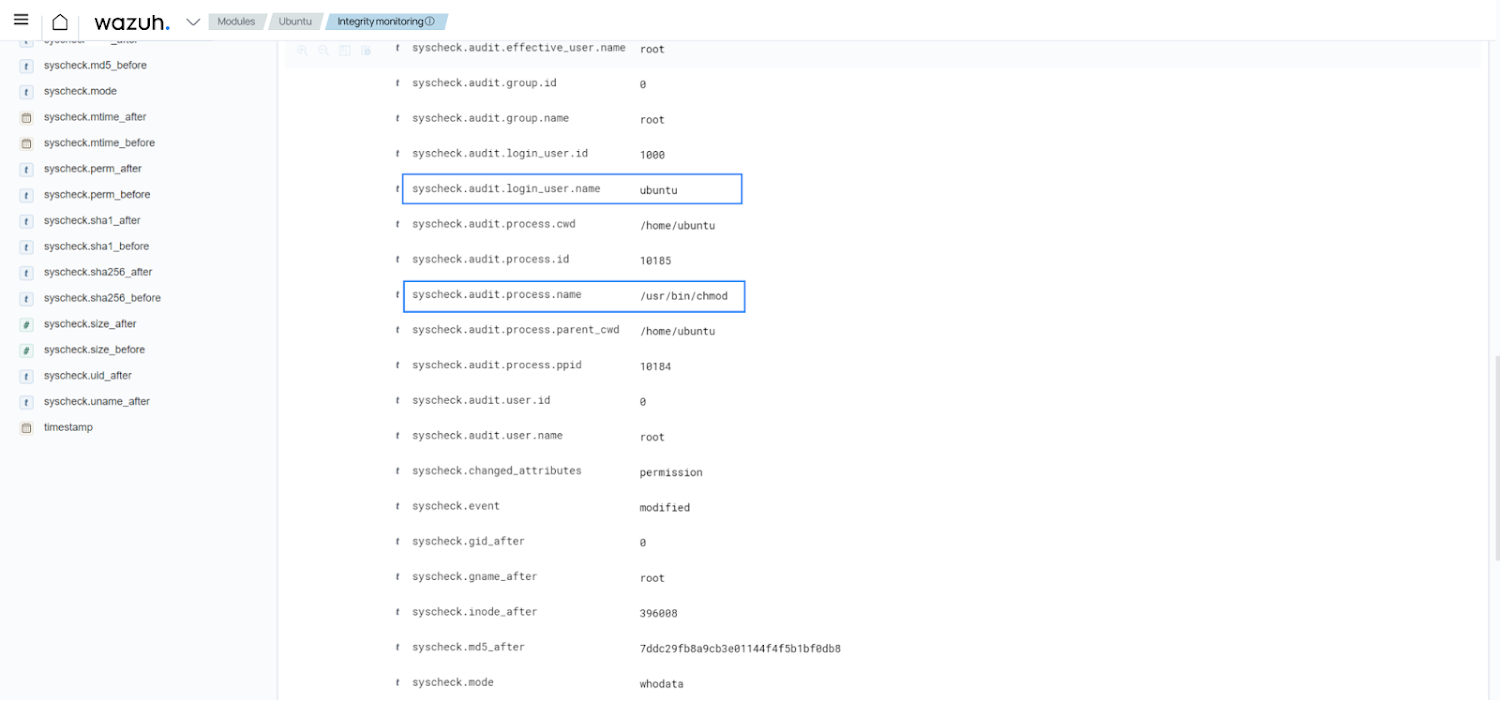 Notify for user and process that modified UFW rules file
Notify for user and process that modified UFW rules file
Positive aspects of making use of the Wazuh FIM for regulatory compliance
Wazuh supplies file integrity monitoring capacity to assistance realize IT security compliance specifications and mitigate hazards. Gains of making use of the Wazuh FIM capability incorporate:
- Integrity checks: It calculates the cryptographic hashes of monitored data files against their baseline to complete integrity checks, detecting modifications accurately. This makes certain the integrity and security of sensitive data.
- Audit trail: Businesses can use the capacity to create detailed experiences and audit trails of file alterations in the course of audits. These experiences are quickly available when desired.
- Menace detection: The Wazuh FIM, when merged with other capabilities like VirusTotal and YARA integration, is powerful for detecting threats or malware dropped on monitored endpoints. By further more applying the Wazuh incident response functionality, these detected threats are competently managed just before damage is brought about on the endpoint.
- Centralized management: It provides centralized administration and reporting capabilities that make it possible for companies to monitor FIM alerts and routines throughout distinct environments from a single dashboard.
- Serious-time alerts: It can deliver real-time alerts for modifications created to monitored files and directories. It also delivers particulars on the consumer who manufactured the improve and the program name or procedure used. This will help security analysts promptly recognize and react to opportunity security incidents or compliance violations.
- Charge-effectiveness: It is totally free to down load and use, generating it a charge-efficient option for businesses, in particular small and medium enterprises with finances constraints.
Conclusion
Wazuh is an open up resource security system that delivers no cost unified XDR and SIEM defense throughout numerous platforms. Wazuh also delivers complementary capabilities, these types of as vulnerability detection, security configuration evaluation, malware detection, and file integrity checking (FIM). Its FIM capability assists companies in complying with some cybersecurity laws. The other capabilities also contribute to conference cybersecurity regulatory compliance specifications, safeguarding an organization’s assets, and maximizing security posture.
Check out our website to find out much more about Wazuh.
References
Located this posting appealing? This report is a contributed piece from a single of our valued partners. Stick to us on Twitter and LinkedIn to read far more exclusive material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Achieve security compliance with Wazuh File Integrity Monitoring
Achieve security compliance with Wazuh File Integrity Monitoring