File Integrity Checking (FIM) is an IT security regulate that screens and detects file improvements in laptop or computer programs. It aids businesses audit significant documents and method configurations by routinely scanning and verifying their integrity. Most information and facts security standards mandate the use of FIM for businesses to guarantee the integrity of their information.
IT security compliance consists of adhering to applicable regulations, policies, laws, methods, and requirements issued by governments and regulatory bodies this kind of as PCI DSS, ISO 27001, TSC, GDPR, and HIPAA. Failure to comply with these regulations can lead to serious repercussions such as cyber breaches, confidential knowledge decline, economic decline, and reputational problems. Therefore, corporations will have to prioritize adherence to IT regulations and criteria to mitigate hazards and safeguard their information techniques successfully.
The rapid speed of technological development and a lack of proficient cybersecurity specialists add to compliance difficulties. To successfully satisfy these restrictions, organizations require to strategically plan, allocate resources to cybersecurity efforts, and carefully classify and safeguard their data property.
Advantages of complying with cybersecurity criteria
Compliance with cybersecurity laws and specifications is vital for enterprises of all measurements. These rules require applying specific cybersecurity actions, insurance policies, and procedures. By adhering to these expectations, corporations ensure the transparency and integrity of their cybersecurity tactics. Some benefits contain:
- It ensures that companies have resilient backup and recovery procedures in place. This minimizes disruptions to company functions and maintains continuity for the duration of a cyber incident or disaster, as facts saved in backup websites can be restored.
- It delivers a structured framework for taking care of dangers throughout various enterprise factors. Companies can reduce the expenses connected with cybersecurity incidents and regulatory non-compliance by adhering to recognized techniques and controls.
- It safeguards an organization’s name. Facts breaches can considerably impression a company’s track record. Compliance can help secure against such breaches, thereby safeguarding the business’s reputation.
- It facilitates entry into regulated marketplaces. In health care, finance, and retail sectors, it assures regulators that the firm’s IT tactics and systems meet up with the needed benchmarks.
The Wazuh FIM ability
Wazuh is an open source security alternative that gives unified XDR and SIEM protection across quite a few platforms. It shields workloads throughout on-premises, virtualized, cloud-centered, and containerized environments to provide companies with an effective method to cybersecurity. Wazuh features file integrity monitoring (FIM) as one of its capabilities it also supplies other capabilities, these types of as security configuration assessment and risk detection and response.
The Wazuh FIM functionality guarantees the subsequent:
- Serious-time and scheduled file and directory checking.
- Detection of unauthorized file alterations.
- Specifics about what or who designed alterations to data.
FIM, put together with other Wazuh abilities these kinds of as malware detection, vulnerability detection, and Security Configuration Assessment (SCA), boosts danger detection, investigation, and remediation. These abilities can assist streamline your organization’s security compliance attempts.
Making certain regulatory compliance making use of the Wazuh FIM capacity
Customers can configure file integrity monitoring to meet up with the prerequisites of IT security compliance requirements related to their organization. The Wazuh FIM can be configured to check file addition, deletion, and modification to a file material.
Holding keep track of of file alterations in just the corporation can help system directors and security analysts have firm-huge visibility of these variations and deal with security incidents instantly. As soon as configured, FIM activities can be considered on the Wazuh dashboard.
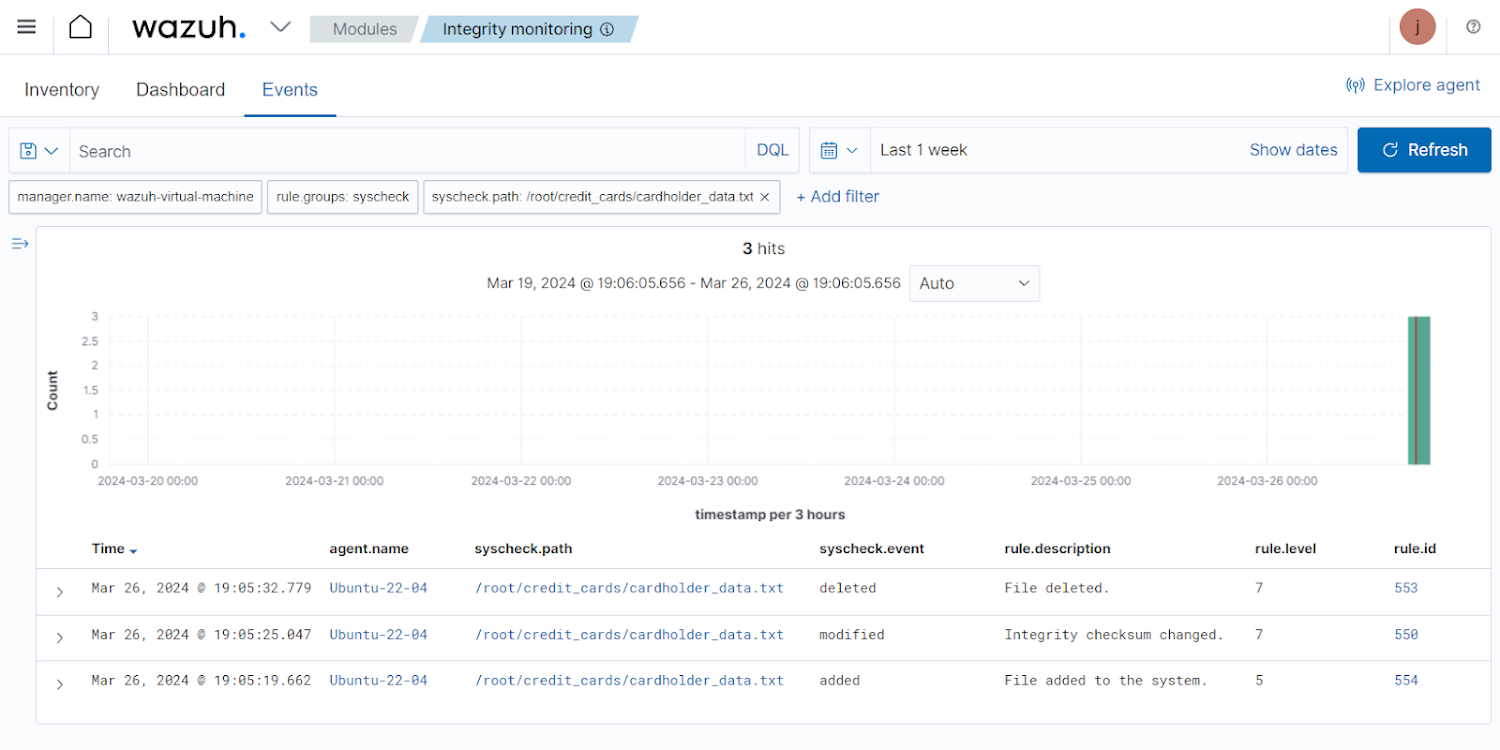 FIM occasions in the Wazuh dashboard
FIM occasions in the Wazuh dashboard
Monitoring file integrity and entry
The Wazuh FIM capability runs a baseline scan and merchants the cryptographic checksum and other attributes of monitored files. When a improve is built to a monitored file, the FIM compares its checksum and attributes to the baseline. If any discrepancy is recognized, an notify will be brought on. Wazuh file integrity monitoring functionality tracks particulars these as the system or person that modified a critical file and when the adjustments had been made. Employing the Wazuh FIM functionality, businesses can assure compliance with several sections of regulatory requirements these as:
- PCI DSS prerequisite 11.5.2
- CM-3 of NIST 800-53
- Report 5.1. (f) of GDPR
- Workforce Security §164.308(a)(2) of HIPAA.
For illustration, we can configure the Wazuh FIM to check the SSH configuration file /and so forth/ssh/sshd_config file on a Linux endpoint. Destructive actors usually focus on the SSH configuration file to weaken security by modifying port figures or disabling robust ciphers. The Wazuh FIM can detect unauthorized modifications by checking adjustments to this file. The adhering to configuration on a Wazuh agent sets the Wazuh FIM ability to monitor the /and so on/ssh/sshd_config file on a monitored endpoint:
The picture under displays alerts activated when alterations are produced to the SSH configuration file.
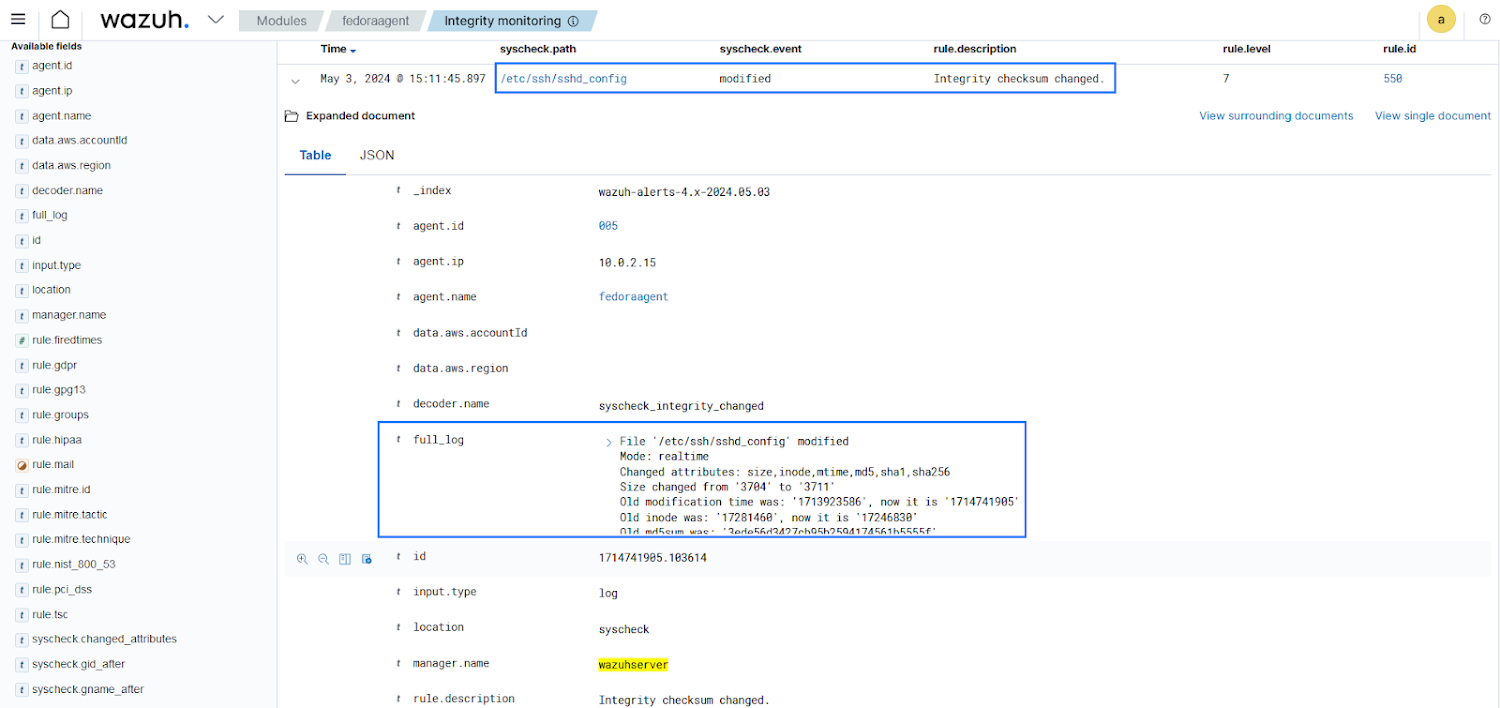 Inform for modification of SSH configuration
Inform for modification of SSH configuration
Equally, the /etc/ufw directory typically includes configuration information for UFW (Uncomplicated Firewall), a common firewall software in Linux. These files outline the guidelines figuring out which network targeted visitors is authorized or blocked on your method. An attacker could modify the UFW principles to open up ports generally closed by default, permitting unauthorized entry to a method or inside network services.
We can configure the Wazuh FIM to check the /and so on/ufw listing. This is configured by adding the configuration below in the agent configuration file on the monitored endpoint. We also permit the attribute whodata, which information the person that alterations a monitored file.
The impression under demonstrates alerts induced when alterations are made to the UFW rule documents.
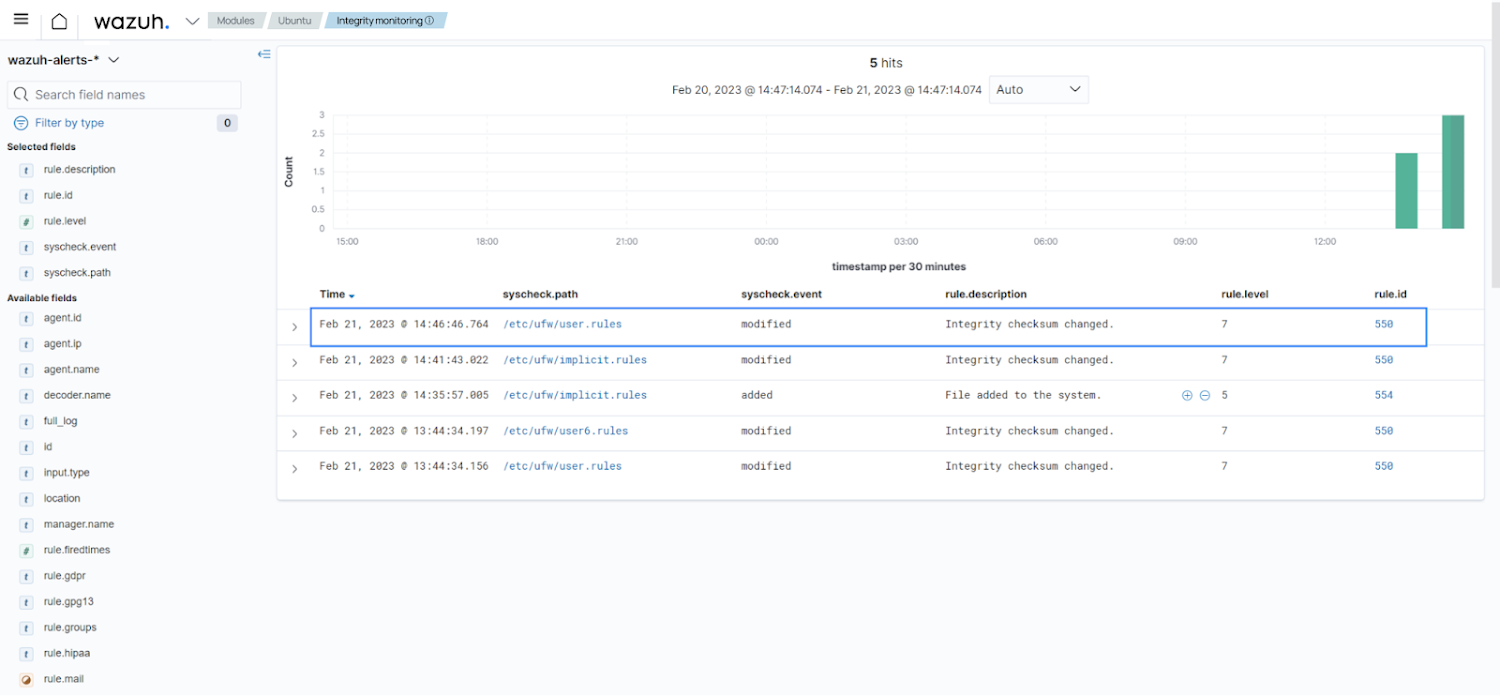 Inform for modification of UFW rule information
Inform for modification of UFW rule information
The Wazuh FIM functionality lets you see the consumer and process initiating the alter. The picture underneath shows this info.
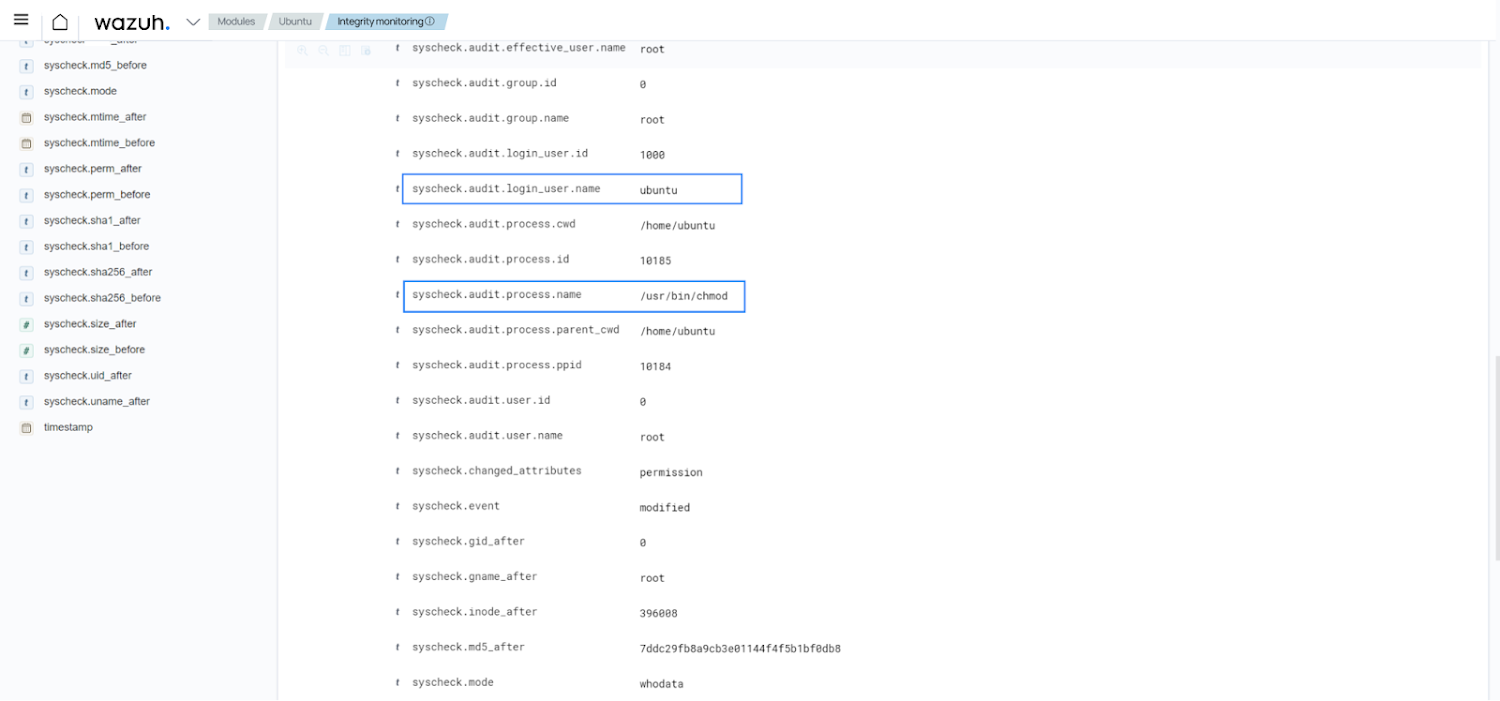 Notify for consumer and process that modified UFW principles file
Notify for consumer and process that modified UFW principles file
Positive aspects of using the Wazuh FIM for regulatory compliance
Wazuh gives file integrity monitoring functionality to enable accomplish IT security compliance needs and mitigate pitfalls. Added benefits of employing the Wazuh FIM capability involve:
- Integrity checks: It calculates the cryptographic hashes of monitored data files versus their baseline to accomplish integrity checks, detecting modifications precisely. This assures the integrity and security of sensitive information.
- Audit path: Businesses can use the ability to generate detailed reviews and audit trails of file adjustments all through audits. These experiences are quickly readily available when needed.
- Menace detection: The Wazuh FIM, when combined with other abilities like VirusTotal and YARA integration, is effective for detecting threats or malware dropped on monitored endpoints. By more using the Wazuh incident reaction functionality, these kinds of detected threats are successfully handled right before harm is brought on on the endpoint.
- Centralized administration: It delivers centralized management and reporting capabilities that enable organizations to monitor FIM alerts and things to do throughout various environments from a one dashboard.
- Genuine-time alerts: It can supply actual-time alerts for alterations designed to monitored files and directories. It also presents aspects on the consumer who produced the transform and the method name or procedure utilised. This will help security analysts instantly establish and reply to probable security incidents or compliance violations.
- Charge-effectiveness: It is free to download and use, producing it a price-helpful solution for businesses, specially smaller and medium enterprises with price range constraints.
Conclusion
Wazuh is an open up supply security platform that gives free of charge unified XDR and SIEM defense throughout several platforms. Wazuh also presents complementary abilities, these kinds of as vulnerability detection, security configuration evaluation, malware detection, and file integrity checking (FIM). Its FIM capacity helps corporations in complying with some cybersecurity laws. The other abilities also add to assembly cybersecurity regulatory compliance prerequisites, safeguarding an organization’s property, and enhancing security posture.
Check out our internet site to master more about Wazuh.
References
Uncovered this posting exciting? This posting is a contributed piece from a single of our valued associates. Abide by us on Twitter and LinkedIn to study extra unique information we article.
Some parts of this article are sourced from:
thehackernews.com


 Researchers Uncover Flaws in Python Package for AI Models and PDF.js Used by Firefox
Researchers Uncover Flaws in Python Package for AI Models and PDF.js Used by Firefox