Say good day to what could be the next massive spam participant: SquirrelWaffle, which is spreading with expanding frequency by means of spam campaigns and infecting devices with a new malware loader.
SquirrelWaffle, a new malware loader, is mal-spamming destructive Microsoft Place of work paperwork to deliver Qakbot malware and the penetration-screening resource Cobalt Strike – two of the most frequent threats routinely noticed concentrating on corporations all around the environment.
Cisco Talos scientists mentioned on Tuesday that they received wind of the malspam strategies starting in mid-September, when they noticed the boobytrapped Office environment files performing to infect programs with SquirrelWaffle in the initial stage of the infection chain.
The strategies are working with stolen email threads to arrive off as replies in those people threads, very similar to how the virulent Emotet malware – ordinarily unfold via malicious e-mail or text messages – works. “The campaigns by themselves feature several very similar qualities to the campaigns beforehand viewed affiliated with proven threats like Emotet,” Cisco Talos researchers stated.

“Due to the prevalence of these strategies, organizations should really be aware of SQUIRRELWAFFLE and the way it could be made use of by attackers to even more compromise corporate networks,” they advised.
The SquirrelWaffle emails generally have hyperlinks to malicious ZIP archives remaining hosted on attacker-managed web servers, researchers claimed. An case in point of one of the malspam email messages is revealed down below.
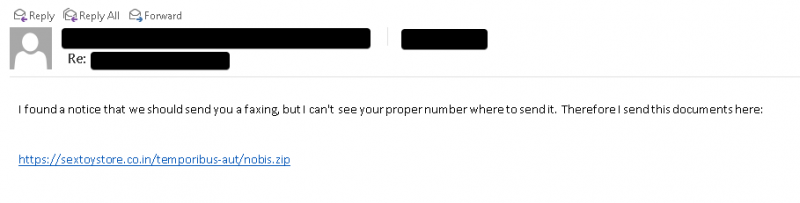
Sample of SquirrelWaffle malspam email. Resource: Cisco Talos.
Most of the messages – 76 % – are written in English. But the language used in the reply concept shifts to match what was utilized in the first email thread, “demonstrating that there is some localization using spot dynamically,” Cisco Talos said. Moreover English, the best 5 languages being applied also include French, German, Dutch and Polish.
Not Constantly the Ripest Nut in the Nest
These squirrels aren’t always buying up acorns that are fated to increase into majestic, income-earning oaks. Scientists explained that, “consistent with other threats also leveraging stolen email threads,” SquirrelWaffle took a number of potshots in deciding upon which email chains to hijack.
They supplied the adhering to instance, in which the attacker replied to an extortion email information – a selection which is possible “ineffective in convincing the recipient to entry the content material in the body of the email,” researchers understated.
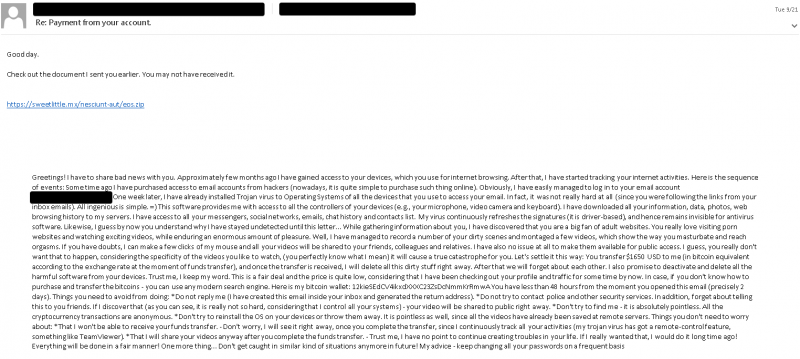
The SquirrelWaffle attacker’s mal-spam reply to an extortionist’s email. Source: Cisco Talos.
SquirrelWaffle Not Scampering as Furiously as Emotet – However
SquirrelWaffle is not as prolific as Emotet – at minimum, not however, however it is expanding steadily. Cisco Talos shared a graph, demonstrated down below, illustrating the quantity of the strategies involving Sept. 1 and Oct. 15.
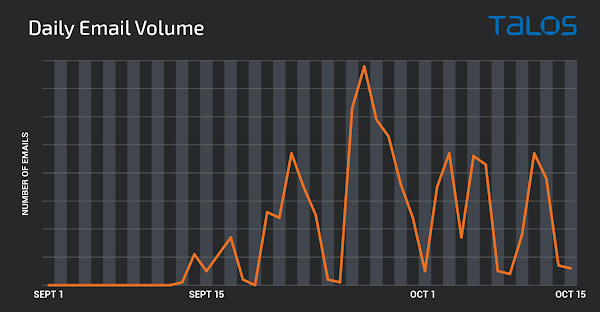
Quantity of SquirrelWaffle strategies tracked from Sept. 1 to Oct. 15, 2021. Supply: Cisco Talos.
“While the volume related with these campaigns is not but achieving the identical level observed previously with threats like Emotet, it appears to be pretty constant and may perhaps maximize around time as the adversaries infect a lot more users and boost the dimensions of their botnet,” Cisco Talos predicted.
Malspam O-Matic
In examining the campaign, scientists observed multiple features that pointed to the destructive Place of work paperwork as very likely obtaining been crafted working with an automatic builder. For example, in the recent campaigns, “the Microsoft Excel spreadsheets ended up crafted to make static analysis with tools like XLMDeobfuscator a lot less successful,” they stated.
The earliest information ended up submitted to general public malware repositories on Sept. 10. Three times afterwards, the campaign volume commenced to ramp up and “has been characterised by everyday spam operates noticed due to the fact then,” according to the writeup.
Much more indicators that it’s having cranked out with an automated builder: “The URL construction of the SQUIRRELWAFFLE distribution servers appears rather tied to the day-to-day campaigns, and rotates each individual few times,” in accordance to the assessment. Cisco Talos gave the example of the desk, demonstrated down below, which depicts variance in the URL landing webpages observed more than a interval of quite a few times.
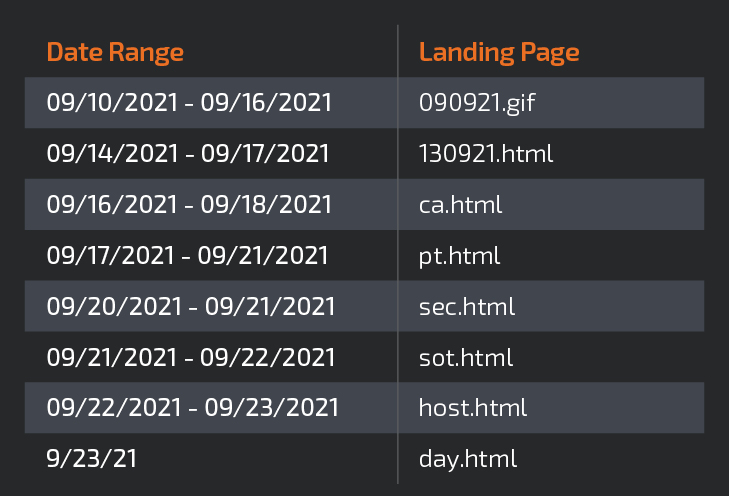
SquirrelWaffle timeline. Supply: Cisco Talos.
“This rotation is also reflected in the maldoc macros themselves, with the macro purpose names and hashes rotating at the exact same time,” the researchers included.
How the Squirrel Twitches
Victims who tumble for the emails and simply click on their links wind up downloading a destructive ZIP archive that includes tainted Microsoft Business office information, which have been evenly break up among Term paperwork and Excel spreadsheets. The caveat: This is an actively evolving threat, and researchers have seen the danger actor change from an initial reliance on using Phrase paperwork to an practically distinctive use of Excel spreadsheets.
In the previously email campaigns working with malicious Word paperwork, researchers noticed the risk actor gussy up the document so it appeared like it was linked with the DocuSign doc-sharing and signing platform: a well-liked decision for dealing with formal transactions.

Destructive Term file intended to glimpse like it is connected with DocuSign. Resource: Cisco Talos.
At any charge, the Business information, be they .DOC or .XLS, spring the upcoming-stage element, which is the SquirrelWaffle payload.
In all of the SquirrelWaffle campaigns observed so considerably, the rigged links used to host the ZIP archives incorporate Latin terms and abide by a URL structure identical to this one:
abogados-en-medellin[.]com/odit-mistake/assumenda[.]zip
But in a lot of conditions, the campaign incorporates separate ZIP archives currently being hosted in diverse directories on the identical domain. Inside of of the ZIP archives, the malicious Place of work information often comply with a naming convention identical to these examples:
- chart-1187900052.xls
- diagram-127.doc
- diagram_1017101088.xls
- Specification-1001661454.xls
They’re Kicking Servers When They’re Currently Down
The malware distribution strategies are seemingly leaping on earlier compromised web servers: generally these managing variations of WordPress, with the most common compromised edition being WordPress 5.8.1.
Scientists also discovered a single situation of “a SQL dump similar to an AZORult panel present on the same host currently being utilized as a C2 server by SQUIRRELWAFFLE,” they said.
They could not figure out if the responsible actor was the same threat or no matter whether the server had been gang-attacked by numerous actors: “As is usually the circumstance with vulnerable servers uncovered to the internet, it is unclear irrespective of whether this panel was remaining administered by the similar menace actor or if the server had basically been compromised by numerous unrelated entities,” Cisco Talos mentioned.
The More Malware Changes…
Cisco Talos said that while the SquirrelWaffle danger is somewhat new, the workings – like the distribution strategies, infrastructure and command-and-manage (C2) implementations – have a good deal in popular with those people witnessed from other, more proven danger actors.
“Organizations need to keep on to utilize detailed protection-in-depth security controls to make sure that they can prevent, detect, or respond to SQUIRRELWAFFLE strategies that could be encountered in their environments,” they recommended.
Look at out our free approaching are living and on-need on-line city halls – distinctive, dynamic conversations with cybersecurity authorities and the Threatpost group.
Some parts of this article are sourced from:
threatpost.com


 Volvo’s 2022 C40 Recharge adds fastback style to the XC40
Volvo’s 2022 C40 Recharge adds fastback style to the XC40