The U.S. governing administration on Thursday posted a new cybersecurity advisory warning of North Korean threat actors’ attempts to deliver e-mail in a fashion that tends to make them appear like they are from genuine and trusted functions.
The joint bulletin was published by the National Security Agency (NSA), the Federal Bureau of Investigation (FBI), and the Office of Point out.
“The DPRK [Democratic People’s Republic of Korea] leverages these spear-phishing campaigns to gather intelligence on geopolitical gatherings, adversary overseas plan techniques, and any data impacting DPRK interests by getting illicit obtain to targets’ non-public paperwork, study, and communications,” NSA said.
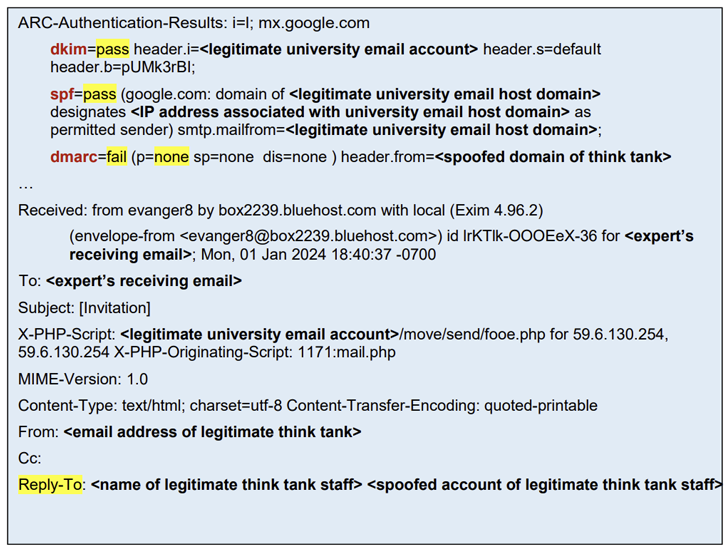
The system exclusively issues exploiting improperly configured DNS Domain-based Message Authentication, Reporting, and Conformance (DMARC) file guidelines to conceal social engineering makes an attempt. In carrying out so, the threat actors can ship spoofed e-mail as if they are from a genuine domain’s email server.

The abuse of weak DMARC procedures has been attributed to a North Korean activity cluster tracked by the cybersecurity local community less than the identify Kimsuky (aka APT43, Black Banshee, Emerald Sleet, Springtail, TA427, and Velvet Chollima), which is a sister collective to the Lazarus Group and is affiliated with the Reconnaissance Basic Bureau (RGB).
Proofpoint, in a report printed last month, claimed that Kimsuky began to integrate this process in December 2023 as portion of broader initiatives to goal international plan gurus for their views on topics similar to nuclear disarmament, U.S.-South Korea procedures, and sanctions.
Describing the adversary as a “savvy social engineering professional,” the organization security agency explained the hacking group is known to interact its targets for prolonged periods of time by way of a sequence of benign discussions to make belief with targets working with various aliases that impersonate DPRK subject matter make any difference professionals in thinks tanks, academia, journalism, and independent investigate.
“Targets are generally asked for to share their views on these subject areas by means of email or a formal analysis paper or report,” Proofpoint scientists Greg Lesnewich and Crista Giering stated.
“Malware or credential harvesting are never ever directly sent to the targets with no an trade of various messages, and […] rarely used by the danger actor. It is possible that TA427 can satisfy its intelligence prerequisites by specifically asking targets for their views or examination relatively than from an an infection.”
The enterprise also famous that numerous of the entities that TA427 has spoofed both did not allow or implement DMARC procedures, so allowing for these types of email messages to get close to security checks and be certain shipping and delivery even if those checks are unsuccessful.
Furthermore, Kimsuky has been observed making use of “absolutely free email addresses spoofing the identical persona in the reply-to subject to encourage the focus on that they are participating with reputable personnel.”

In a person email highlighted by the U.S. government, the danger actor posed as a reputable journalist seeking an job interview from an unnamed specialist to go over North Korea’s nuclear armament plans, but openly pointed out that their email account would be blocked quickly and urged the receiver to reply to them on their private email, which was a bogus account mimicking the journalist.
This suggests that the phishing message was at first sent from the journalist’s compromised account, so raising the likelihood that the victim would reply to the different phony account.
Businesses are encouraged to update their DMARC policies to instruct their email servers to take care of email messages that are unsuccessful the checks as suspicious or spam (i.e., quarantine or reject) and acquire combination opinions reviews by environment up an email address in the DMARC report.
Discovered this short article fascinating? Follow us on Twitter and LinkedIn to browse a lot more distinctive content we post.
Some parts of this article are sourced from:
thehackernews.com


 Google Announces Passkeys Adopted by Over 400 Million Accounts
Google Announces Passkeys Adopted by Over 400 Million Accounts