Previously this week, ServiceNow declared on its aid site that misconfigurations within the platform could result in “unintended obtain” to sensitive facts. For businesses that use ServiceNow, this security publicity is a critical issue that could have resulted in important data leakage of sensitive corporate data. ServiceNow has since taken actions to deal with this issue.
This article fully analyzes the issue, points out why this critical application misconfiguration could have had critical penalties for companies, and remediation measures companies would just take, if not for the ServiceNow resolve. (Even though, advised to double check that the correct has closed the organization’s publicity.)
In a Nutshell
ServiceNow is a cloud-dependent platform utilised for automating IT assistance management, IT operations management, and IT organization administration for client support, as properly as HR, security operations, and a large variety of supplemental domains. This SaaS software is thought of to be one particular of the top rated company-critical programs thanks to its infrastructural nature, extensibility as a progress platform, and entry to confidential and proprietary information during the organization.
Very simple Listing is an interface widget that pulls info that is saved in tables and takes advantage of them in dashboards. The default configuration for Easy List allows the knowledge in the tables to be accessed remotely by unauthenticated customers. These tables include sensitive details, including material from IT tickets, interior classified know-how bases, personnel information, and extra.
These misconfigurations have essentially been in location considering the fact that the introduction of Accessibility Control Lists in 2015. To date, there ended up no noted incidents as a final result. Nonetheless, considering the modern publication of the info leakage investigation, leaving it unresolved could have uncovered corporations extra than at any time.
This exposure was the result of just a person default configuration — and there are hundreds of configurations covering access manage, knowledge leakage, malware safety, and additional that have to be secured and maintained. For corporations applying an SSPM (SaaS Security Posture Management solution), like Adaptive Shield, companies can a lot more effortlessly discover risky misconfigurations and see if they are compliant or non-compliant (see graphic 1 under).
Find out a lot more about how SSPM secures the critical applications in your SaaS stack
Inside of the ServiceNow Misconfigurations
It is vital to reiterate that this issue was not triggered by a vulnerability in ServiceNow’s code but by a configuration that exists within the platform.
This issue stems from security controls in a ServiceNow Access Manage List (ACL) widget called Very simple List, which puts records into easily readable tables. These tables manage facts from many resources and have configurations with a default placing of General public Accessibility.
Mainly because these tables are the core of ServiceNow, the issue was not contained within a solitary placing that can be mounted. It wanted to be remediated in numerous locations in just the software in mix with the use of the UI widget, and through all tenants. Further complicating the issue, was that switching a one location could crack current workflows related to the Basic Record tables, causing serious disruption of current processes.
Remediation Methods
Published by ServiceNow in their understanding base posting – General Information and facts | Possible Public List Widget Misconfiguration, the exposure assessment and remediation actions include:
- Critique Access Command Lists (ACLs) that both are solely empty or, alternately, include the job “Community”
- Assessment general public widgets and established the “Public” flag to phony where it is not aligned with their use situations
- Consider applying stricter access regulate steps using crafted-in controls made available by ServiceNow, this sort of as IP Address Accessibility Regulate or Adaptive Authentication
- Look at installing ServiceNow Specific Roles Plugin. ServiceNow states that the plugin stops exterior consumers from accessing inside information and scenarios using this plugin are not impacted by this issue (the plugin guarantees that every single ACL declares at minimum one particular job need)
These proposed remediation methods can continue to be utilized for organizations that are uncovered (even immediately after the deal with) as it’s truly worth double examining to be certain top rated security during the group.
Discover much more about automating your ServiceNow Security
Automate Info Leakage Avoidance for ServiceNow
Organizations that use a SaaS Security Posture Administration (SSPM) answer, like Adaptive Defend, are capable to attain visibility into ServiceNow’ and any other SaaS app’s configurations and remediate any configuration issue.
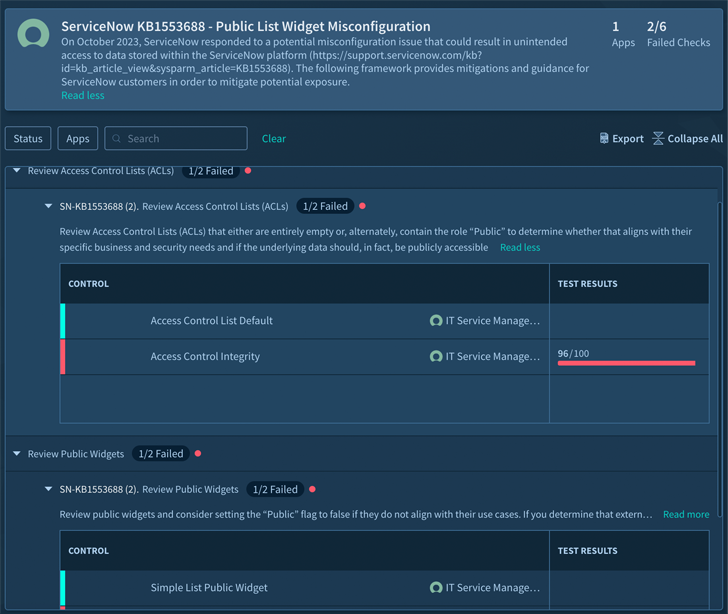 Image 1: Adaptive Shield dashboard with the compliance framework: ServiceNow KB1553688 – Public Record Widget Misconfiguration
Image 1: Adaptive Shield dashboard with the compliance framework: ServiceNow KB1553688 – Public Record Widget Misconfiguration
SSPMs alert security groups when there are substantial-risk configurations, enabling them to alter their configurations and prevent any style of info leakage. This way, companies obtain a much better comprehending of their firm’s attack surface, amount of risk, and security posture with an SSPM.
Click on right here to ask for a demo and get an evaluation of any app publicity
Identified this write-up intriguing? Adhere to us on Twitter and LinkedIn to go through a lot more distinctive written content we put up.
Some parts of this article are sourced from:
thehackernews.com


 EleKtra-Leak Cryptojacking Attacks Exploit AWS IAM Credentials Exposed on GitHub
EleKtra-Leak Cryptojacking Attacks Exploit AWS IAM Credentials Exposed on GitHub