A new ongoing marketing campaign dubbed EleKtra-Leak has set its eyes on uncovered Amazon Web Support (AWS) identification and accessibility management (IAM) credentials in just public GitHub repositories to facilitate cryptojacking pursuits.
“As a end result of this, the threat actor involved with the campaign was in a position to generate several AWS Elastic Compute (EC2) scenarios that they utilised for wide-ranging and very long-long lasting cryptojacking operations,” Palo Alto Networks Device 42 researchers William Gamazo and Nathaniel Quist mentioned in a technical report shared with The Hacker News.
The operation, active considering that at minimum December 2020, is built to mine Monero from as numerous as 474 exceptional Amazon EC2 scenarios among August 30 and October 6, 2023.
A standout aspect of the assaults is the automatic targeting of AWS IAM qualifications in four minutes of their initial exposure on GitHub, indicating that risk actors are programmatically cloning and scanning the repositories to seize the uncovered keys.
The adversary has also been observed blocklisting AWS accounts that publicize IAM credentials in what is most likely found as an effort and hard work to avert more investigation.

There is proof to counsel that the attacker may well also have been connected to an additional cryptojacking campaign disclosed by Intezer in January 2021 aimed at badly secured Docker products and services utilizing the similar bespoke mining software package.
Aspect of the campaign’s results lies in the exploitation of blindspots in GitHub’s solution scanning feature and AWS’ AWSCompromisedKeyQuarantine policy to flag and avoid the misuse of compromised or exposed IAM credentials to operate or get started EC2 situations.
Although the quarantine policy is used in two minutes of the AWS credentials becoming publicly available on GitHub, it’s staying suspected that the keys are being exposed by way of an as-however-undetermined technique.
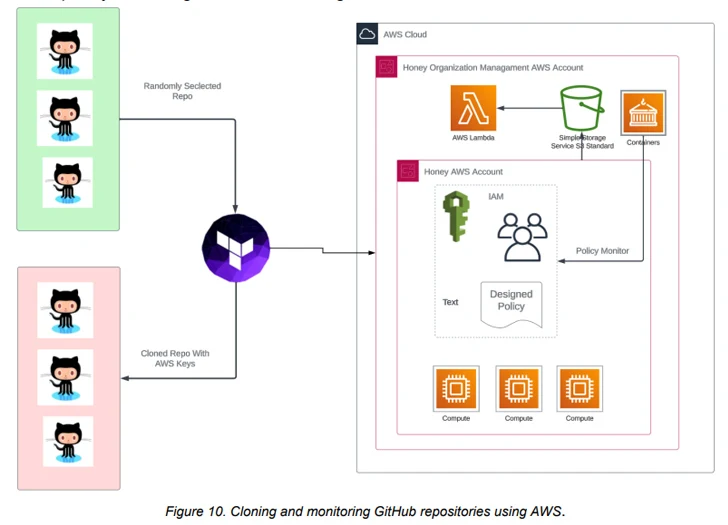
Device 42 stated that the “threat actor may possibly be capable to locate exposed AWS keys that are not instantly detected by AWS and subsequently manage these keys outside of the AWSCompromisedKeyQuarantine policy.”
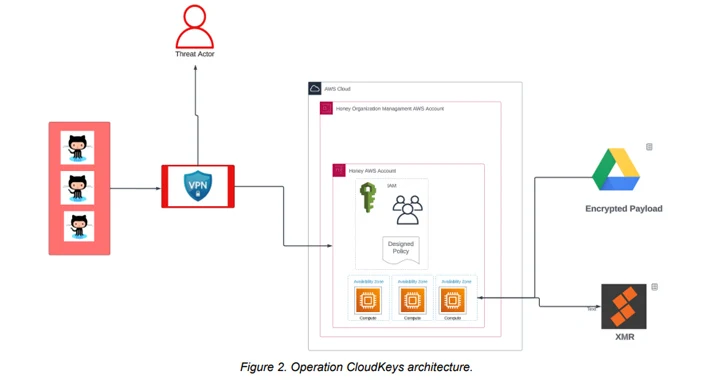
In the attack chains uncovered by the cybersecurity company, the stolen AWS qualifications are used to carry out an account reconnaissance operation, adopted by generating AWS security teams and launching numerous EC2 situations throughout different areas from driving a digital private network (VPN).
The cryptomining functions are performed on c5a.24xlarge AWS cases owing to their bigger processing energy, making it possible for its operators to mine much more cryptocurrency in a shorter period of time of time.

The mining software program made use of to carry out cryptojacking is fetched from a Google Generate URL, highlighting a sample of malicious actors leveraging the trust affiliated with extensively utilized programs to fly underneath the radar.
“The sort of Amazon Equipment Pictures (AMI) the menace actor used was also unique,” the researchers stated. “The recognized photographs had been personal and they were being not listed in the AWS Market.”
To mitigate these assaults, corporations that accidentally expose AWS IAM qualifications are proposed to instantly revoke any API connections utilizing the keys, remove them from the GitHub repository, and audit GitHub repository cloning events for any suspicious functions.
“The menace actor can detect and start a entire-scale mining procedure within just 5 minutes from the time of an AWS IAM credential becoming exposed in a public GitHub repository,” the scientists claimed. “Irrespective of prosperous AWS quarantine procedures, the campaign maintains continuous fluctuation in the number and frequency of compromised sufferer accounts.”
Found this write-up interesting? Stick to us on Twitter and LinkedIn to go through a lot more exclusive information we submit.
Some parts of this article are sourced from:
thehackernews.com

 Urgent: New Security Flaws Discovered in NGINX Ingress Controller for Kubernetes
Urgent: New Security Flaws Discovered in NGINX Ingress Controller for Kubernetes