A beforehand undocumented “flexible” backdoor referred to as Kapeka has been “sporadically” observed in cyber assaults focusing on Jap Europe, together with Estonia and Ukraine, since at least mid-2022.
The results appear from Finnish cybersecurity business WithSecure, which attributed the malware to the Russia-connected advanced persistent danger (APT) team tracked as Sandworm (aka APT44 or Seashell Blizzard). Microsoft is tracking the exact same malware below the name KnuckleTouch.
“The malware […] is a adaptable backdoor with all the essential functionalities to serve as an early-stage toolkit for its operators, and also to supply extended-time period entry to the sufferer estate,” security researcher Mohammad Kazem Hassan Nejad stated.
Kapeka comes fitted with a dropper that’s made to launch and execute a backdoor part on the contaminated host, immediately after which it removes by itself. The dropper is also dependable for placing up persistence for the backdoor possibly as a scheduled task or autorun registry, based on whether the system has Method privileges.

Microsoft, in its personal advisory released in February 2024, explained Kapeka as associated in several campaigns distributing ransomware and that it can be used to carry out a wide variety of functions, these as stealing credentials and other details, conducting harmful assaults, and granting menace actors remote entry to the unit.
The backdoor is a Windows DLL written in C++ and options an embedded command-and-manage (C2) configuration that’s used to establish contact with an actor-controlled server and holds data about the frequency at which the server wants to be polled in buy to retrieve commands.
Aside from masquerading as a Microsoft Term incorporate-in to make it seem legitimate, the backdoor DLL gathers information and facts about the compromised host and implements multi-threading to fetch incoming recommendations, method them, and exfiltrate the final results of the execution to the C2 server.
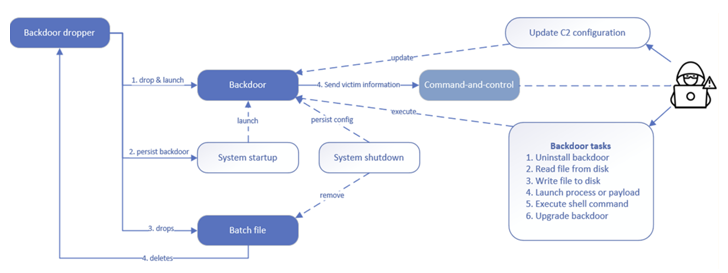
“The backdoor uses WinHttp 5.1 COM interface (winhttpcom.dll) to employ its network communication part,” Nejad stated. “The backdoor communicates with its C2 to poll for tasks and to deliver back fingerprinted info and undertaking benefits. The backdoor utilizes JSON to send out and acquire details from its C2.”
The implant is also capable of updating its C2 configuration on-the-fly by receiving a new version from the C2 server for the duration of polling. Some of the principal characteristics of the backdoor enable it to examine and generate information from and to disk, start payloads, execute shell commands, and even up grade and uninstall by itself.
The exact strategy by which the malware is propagated is currently unknown. Even so, Microsoft pointed out that the dropper is retrieved from compromised internet websites making use of the certutil utility, underscoring the use of a legitimate dwelling-off-the-land binary (LOLBin) to orchestrate the attack.

Kapeka’s connections to Sandworm occur conceptual and configuration overlaps with formerly disclosed families like GreyEnergy, a likely successor to the BlackEnergy toolkit, and Prestige.
“It is probably that Kapeka was utilised in intrusions that led to the deployment of Status ransomware in late 2022,” WithSecure reported. “It is possible that Kapeka is a successor to GreyEnergy, which itself was possible a substitute for BlackEnergy in Sandworm’s arsenal.”
“The backdoor’s victimology, infrequent sightings, and level of stealth and sophistication suggest APT-amount activity, extremely most likely of Russian origin.”
Located this posting intriguing? Follow us on Twitter and LinkedIn to read through much more exceptional content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 GenAI: A New Headache for SaaS Security Teams
GenAI: A New Headache for SaaS Security Teams