A new Google malvertising campaign is leveraging a cluster of domains mimicking a respectable IP scanner software to provide a previously not known backdoor dubbed MadMxShell.
“The risk actor registered a number of look-alike domains working with a typosquatting method and leveraged Google Ads to push these domains to the top of look for motor outcomes concentrating on precise research keyword phrases, thus luring victims to go to these web pages,” Zscaler ThreatLabz scientists Roy Tay and Sudeep Singh reported.
As numerous as 45 domains are reported to have been registered among November 2023 and March 2024, with the internet sites masquerading as port scanning and IT management software program these kinds of as Sophisticated IP Scanner, Offended IP Scanner, IP scanner PRTG, and ManageEngine.
Though this is not the very first time risk actors are banking on malvertising procedures to provide malware via lookalike web sites, the growth marks the very first time the shipping and delivery automobile is staying made use of to propagate a innovative Windows backdoor.

So, consumers who end up exploring for these types of applications are shown bogus websites that include things like JavaScript code made to download a destructive file (“Superior-ip-scanner.zip”) on clicking the download button.
Current within just the ZIP archive is a DLL file (“IVIEWERS.dll”) and an executable (“State-of-the-art-ip-scanner.exe”), the latter of which utilizes DLL side-loading to load the DLL and activate the an infection sequence.
The DLL file is accountable for injecting the shellcode into the “Superior-ip-scanner.exe” method by means of a approach identified as approach hollowing, next which the injected EXE file unpacks two more documents – OneDrive.exe and Secur32.dll.
OneDrive.exe, a legitimate signed Microsoft binary, is then abused to sideload Secur32.dll, and finally execute the shellcode backdoor, but not before setting up persistence on the host by signifies of a scheduled process and disabling Microsoft Defender Antivirus.
The backdoor – so named for its use of DNS MX queries for command-and-regulate (C2) – is designed to assemble procedure details, operate instructions via cmd.exe, and execute simple file manipulation functions this sort of as reading, crafting, and deleting documents.
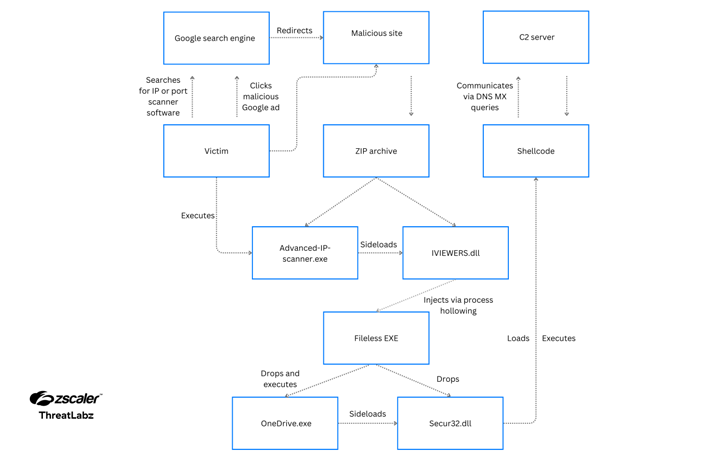
It sends requests to the C2 server (“litterbolo[.]com”) by encoding the info in the subdomain(s) of the Fully Experienced Area Identify (FQDN) in a DNS mail trade (MX) query packet and gets instructions encoded inside of the response packet.
“The backdoor employs methods these kinds of as various stages of DLL facet-loading and DNS tunneling for command-and-manage (C2) interaction as a means to evade endpoint and network security solutions, respectively,” Tay and Singh explained.
“In addition, the backdoor utilizes evasive strategies like anti-dumping to avoid memory investigation and hinder forensics security options.”

There is now no sign of wherever the malware operators originate from or what their intentions are, but Zscaler mentioned it discovered two accounts designed by them on felony underground message boards like blackhatworld[.]com and social-eng[.]ru using the email tackle wh8842480@gmail[.]com, which was also employed to sign-up a area spoofing Superior IP Scanner.
Particularly, the danger actor has been identified engaging in posts featuring ways to set up endless Google AdSense threshold accounts way back again in June 2023, indicating their curiosity in launching their personal lengthy-lasting malvertising marketing campaign.
“Google Advertisements threshold accounts and procedures for abusing them are frequently traded on BlackHat community forums,” the researchers reported. “A lot of times they provide a way for the risk actor to insert as several credits as possible to operate Google Ads campaigns.”
“This makes it possible for the threat actors to operate campaigns with out in fact paying out right up until the threshold restrict. A moderately high threshold limit lets the threat actor run the ad campaign for a significant amount of money of time.”
Located this posting attention-grabbing? Follow us on Twitter and LinkedIn to read through far more special material we article.
Some parts of this article are sourced from:
thehackernews.com


 Russian APT Deploys New ‘Kapeka’ Backdoor in Eastern European Attacks
Russian APT Deploys New ‘Kapeka’ Backdoor in Eastern European Attacks