The Russia-linked danger actor identified as Turla contaminated a number of systems belonging to an unnamed European non-governmental group (NGO) in get to deploy a backdoor called TinyTurla-NG.
“The attackers compromised the initial system, recognized persistence and extra exclusions to antivirus products and solutions functioning on these endpoints as portion of their preliminary submit-compromise steps,” Cisco Talos claimed in a new report printed currently.
“Turla then opened added channels of communication by using Chisel for details exfiltration and to pivot to supplemental accessible techniques in the network.”
There is evidence indicating that the infected units ended up breached as early as Oct 2023, with Chisel deployed in December 2023 and details exfiltrating getting area by using the instrument a thirty day period later, about January 12, 2024.

TinyTurla-NG was to start with documented by the cybersecurity company last thirty day period immediately after it was identified to be utilized in connection with a cyber attack concentrating on a Polish NGO performing on improving upon Polish democracy and supporting Ukraine during the Russian invasion.
Cisco Talos told The Hacker News at the time that the marketing campaign seems to be remarkably targeted and centered on a small number of corporations, most of which are situated in Poland.
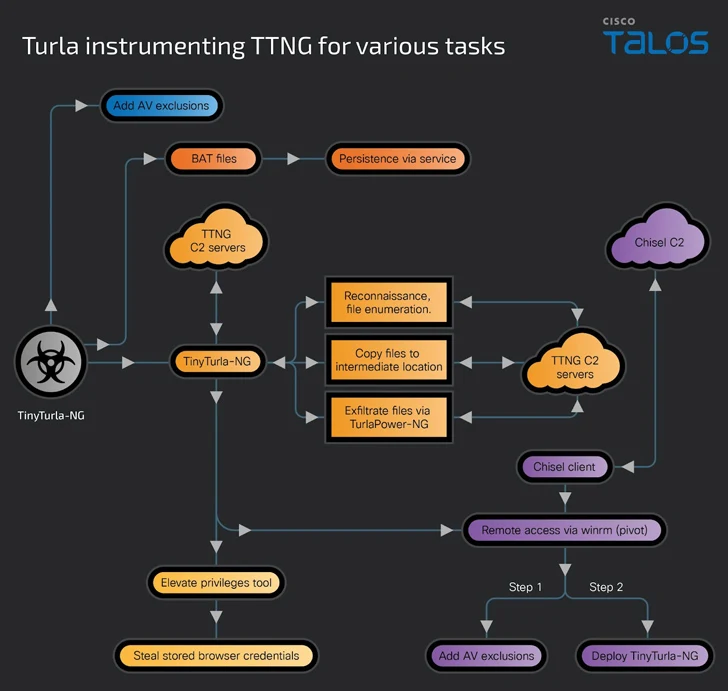
The attack chain will involve Turla exploiting their preliminary obtain to configure Microsoft Defender antivirus exclusions to evade detection and fall TinyTurla-NG, which is then persisted by building a destructive “sdm” company that masquerades as a “System Machine Supervisor” service.
TinyTurla-NG functions as a backdoor to perform follow-on reconnaissance, exfiltrate documents of desire to a command-and-control (C2) server, and deploy a custom-crafted variation of the Chisel tunneling software package. The specific intrusion pathway is still currently being investigated.
“After the attackers have acquired access to a new box, they will repeat their routines to make Microsoft Defender exclusions, drop the malware factors, and generate persistence,” Talos researchers explained.
Discovered this write-up intriguing? Stick to us on Twitter and LinkedIn to go through additional exceptional material we put up.
Some parts of this article are sourced from:
thehackernews.com


 Over 800 npm Packages Found with Discrepancies, 18 Exploitable to ‘Manifest Confusion’
Over 800 npm Packages Found with Discrepancies, 18 Exploitable to ‘Manifest Confusion’