New research has identified around 800 offers in the npm registry which have discrepancies from their registry entries, out of which 18 have been observed to exploit a system referred to as manifest confusion.
The conclusions occur from cybersecurity agency JFrog, which reported the issue could be exploited by danger actors to trick builders into working destructive code.
“It really is an actual risk considering that builders could be tricked into downloading packages that search innocent, but whose hidden dependencies are essentially malicious,” security researcher Andrey Polkovnichenko told The Hacker Information.

Manifest confusion was very first documented in July 2023, when security researcher Darcy Clarke identified that mismatches in manifest and bundle metadata could be weaponized to stage computer software supply chain attacks.
The difficulty stems from the actuality that the npm registry does not validate no matter if the manifest file contained in the tarball (offer.json) matches the manifest information supplied to the npm server through the publishing course of action by using an HTTP Set ask for to the offer URI endpoint.
As a consequence, a threat actor could take benefit of this absence of cross verification to provide a distinctive manifest containing concealed dependencies which is processed during package installation to stealthily set up destructive dependencies on to the developer’s procedure.
“The obvious, or ‘fake,’ manifest can mislead developers and even audit tools that count on the knowledge obtainable in the npm registry database,” JFrog claimed. “In fact, the installer usually takes the file package.json from the tarball, which may well be distinctive from the visible one particular supplied in the HTTP Place request.”
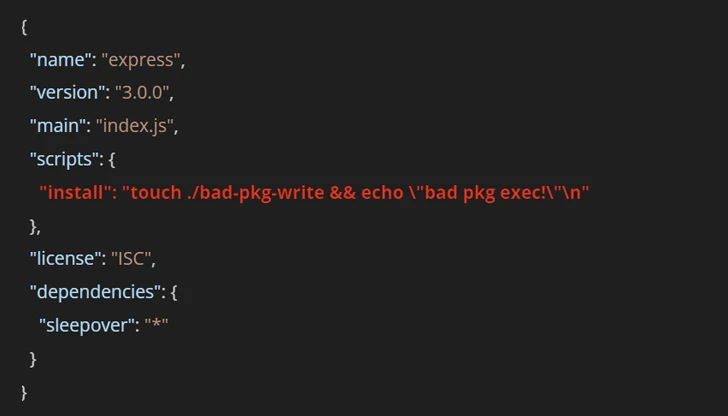
The corporation said it recognized far more than 800 offers the place there was a mismatch involving the manifest in the npm registry and the bundle.json file inside the tarball.
Though numerous of these mismatches are the outcome of protocol specification variations or variations in the scripts section of the package deal file, 18 of them are reported to have been created to exploit manifest confusion.
A notable bundle in dilemma is yatai-web-ui, which is designed to mail an HTTP request to a server with information about the IP address of the device in which the package deal was put in.

The results present that the attack vector looks to have never been put to use by danger actors. That said, it’s vital that builders take ways to assure the deals are absolutely free of suspicious behaviors.
“Considering that this issue was not settled by npm, trusting offers only by how they seem on npm’s internet site, might be dangerous,” Polkovnichenko explained.
“Companies should really introduce processes that verify that all packages that enter the organization or are applied by their dev teams are protected and can be trusted. Exclusively in the situation of manifest confusion, it truly is necessary that each individual deal is analyzed to see if there are any concealed dependencies.”
Found this short article intriguing? Observe us on Twitter and LinkedIn to read through additional unique content material we put up.
Some parts of this article are sourced from:
thehackernews.com


 AndroxGh0st Malware Targets Laravel Apps to Steal Cloud Credentials
AndroxGh0st Malware Targets Laravel Apps to Steal Cloud Credentials