Cybersecurity researchers have disclosed what they say is the “1st native Spectre v2 exploit” from the Linux kernel on Intel systems that could be exploited to examine delicate info from the memory.
The exploit, named Native Branch Record Injection (BHI), can be utilised to leak arbitrary kernel memory at 3.5 kB/sec by bypassing present Spectre v2/BHI mitigations, researchers from Devices and Network Security Team (VUSec) at Vrije Universiteit Amsterdam explained in a new analyze.
The shortcoming is currently being tracked as CVE-2024-2201.
BHI was 1st disclosed by VUSec in March 2022, describing it as a system that can get all over Spectre v2 protections in modern-day processors from Intel, AMD, and Arm.
Although the attack leveraged prolonged Berkeley Packet Filters (eBPFs), Intel’s suggestions to handle the difficulty, between other issues, was to disable Linux’s unprivileged eBPFs.

“Privileged managed runtimes that can be configured to permit an unprivileged consumer to make and execute code in a privileged area — such as Linux’s ‘unprivileged eBPF’ — noticeably boost the risk of transient execution assaults, even when defenses from intra-mode [Branch Target Injection] are existing,” Intel said at the time.
“The kernel can be configured to deny obtain to unprivileged eBPF by default, when nonetheless making it possible for administrators to empower it at runtime exactly where wanted.”
Native BHI neutralizes this countermeasure by demonstrating that BHI is feasible devoid of eBPF. It impacts all Intel systems that are inclined to BHI.
As a outcome, it would make it possible for an attacker with obtain to CPU sources to affect speculative execution paths through malicious computer software installed on a device with the goal of extracting delicate facts that are related with a distinct process.
“Present mitigation strategies of disabling privileged eBPF and enabling (Great)IBT are insufficient in halting BHI exploitation towards the kernel/hypervisor,” the CERT Coordination Center (CERT/CC) explained in an advisory.
“An unauthenticated attacker can exploit this vulnerability to leak privileged memory from the CPU by speculatively leaping to a chosen gadget.”
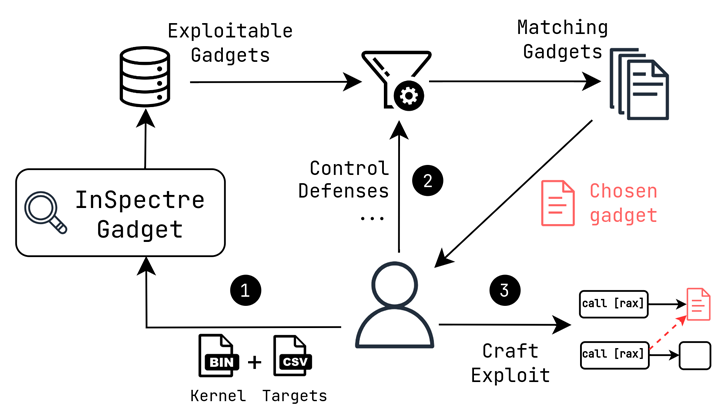
The flaw has been confirmed to influence Illumos, Intel, Purple Hat, SUSE Linux, Triton Data Centre, and Xen. AMD, in a bulletin, stated it really is “aware of any effects” on its goods.
The disclosure comes weeks following IBM and VUSec specific GhostRace (CVE-2024-2193), a variant of Spectre v1 that employs a mix of speculative execution and race problems to leak knowledge from up to date CPU architectures.

It also follows new analysis from ETH Zurich that disclosed a family members of assaults dubbed Ahoi Attacks that could be used to compromise components-based trusted execution environments (TEEs) and split private virtual machines (CVMs) like AMD Safe Encrypted Virtualization-Protected Nested Paging (SEV-SNP) and Intel Belief Area Extensions (TDX).
The assaults, codenamed Heckler and WeSee, make use of destructive interrupts to crack the integrity of CVMs, likely letting risk actors to remotely log in and obtain elevated entry, as nicely as perform arbitrary read, compose, and code injection to disable firewall policies and open a root shell.
“For Ahoi Assaults, an attacker can use the hypervisor to inject destructive interrupts to the victim’s vCPUs and trick it into executing the interrupt handlers,” the scientists said. “These interrupt handlers can have world wide outcomes (e.g., modifying the register state in the software) that an attacker can trigger to compromise the victim’s CVM.”
In response to the results, AMD reported the vulnerability is rooted in the Linux kernel implementation of SEV-SNP and that fixes addressing some of the issues have been upstreamed to the primary Linux kernel.
Observed this article exciting? Adhere to us on Twitter and LinkedIn to go through more unique information we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Webinar: Learn How to Stop Hackers from Exploiting Hidden Identity Weaknesses
Webinar: Learn How to Stop Hackers from Exploiting Hidden Identity Weaknesses