Menace actors have been observed leveraging the QEMU open up-supply components emulator as tunneling software all through a cyber attack concentrating on an unnamed “significant enterprise” to join to their infrastructure.
Though a number of legit tunneling tools like Chisel, FRP, ligolo, ngrok, and Plink have been employed by adversaries to their edge, the development marks the 1st QEMU that has been utilised for this purpose.
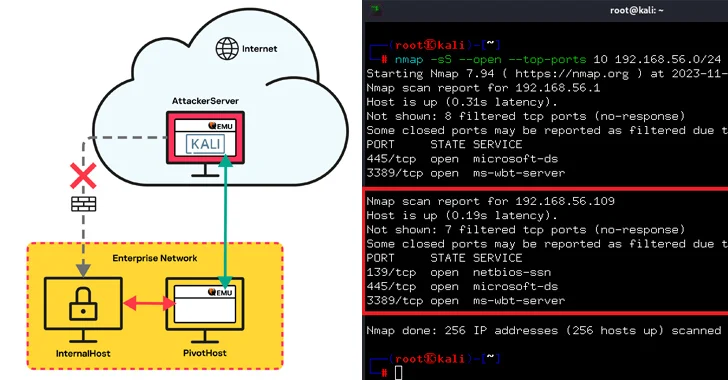
“We observed that QEMU supported connections concerning virtual machines: the -netdev solution produces network products (backend) that can then link to the virtual devices,” Kaspersky researchers Grigory Sablin, Alexander Rodchenko, and Kirill Magaskin claimed.
“Just about every of the various network equipment is outlined by its kind and supports extra solutions.”

In other text, the concept is to develop a digital network interface and a socket-variety network interface, thus letting the digital device to communicate with any distant server.
The Russian cybersecurity firm reported it was equipped to use QEMU to set up a network tunnel from an internal host in just the organization network that did not have internet access to a pivot host with internet obtain, which connects to the attacker’s server on the cloud functioning the emulator.
The conclusions demonstrate that menace actors are continually diversifying their attack approaches to blend their malicious website traffic with genuine action and meet their operational objectives.
“Destructive actors employing legit resources to perform a variety of attack actions is practically nothing new to incident reaction experts,” the scientists stated.
“This additional supports the thought of multi-degree defense, which addresses the two reputable endpoint protection, and specialized alternatives for detecting and guarding towards complex and specific attacks which include human-operated ones.”
Observed this report fascinating? Comply with us on Twitter and LinkedIn to read through much more unique material we publish.
Some parts of this article are sourced from:
thehackernews.com

 CISA Warns of Actively Exploited JetBrains TeamCity Vulnerability
CISA Warns of Actively Exploited JetBrains TeamCity Vulnerability