A new fileless attack dubbed PyLoose has been noticed hanging cloud workloads with the objective of providing a cryptocurrency miner, new findings from Wiz reveal.
“The attack is composed of Python code that hundreds an XMRig Miner straight into memory working with memfd, a known Linux fileless procedure,” security scientists Avigayil Mechtinger, Oren Ofer, and Itamar Gilad reported. “This is the 1st publicly documented Python-primarily based fileless attack focusing on cloud workloads in the wild.”
The cloud security firm claimed it located just about 200 occasions where the attack strategy was utilized for cryptocurrency mining. No other particulars about the risk actor are at the moment regarded other than the simple fact that they possess complex abilities.
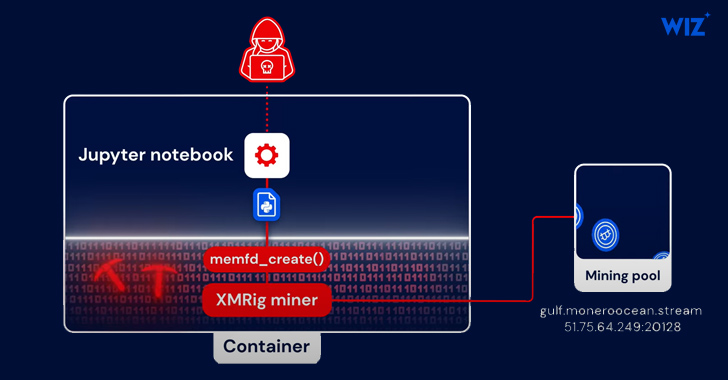
In the infection chain documented by Wiz, first accessibility is obtained as a result of the exploitation of a publicly obtainable Jupyter Notebook assistance that allowed for the execution of procedure instructions applying Python modules.
PyLoose, 1st detected on June 22, 2023, is a Python script with just 9 lines of code that embeds a compressed and encoded precompiled XMRig miner. The payload is retrieved from paste.c-net[.]org into the Python runtime’s memory by means of an HTTPS GET ask for with out owning to generate the file to disk.
The Python code is intended to decode and decompress the XMRig miner and then load it immediately into memory by means of the memfd memory file descriptor, which is utilised to entry memory-resident data files.
Impending WEBINAR🔐 PAM Security – Skilled Methods to Secure Your Delicate Accounts
This professional-led webinar will equip you with the knowledge and strategies you need to have to remodel your privileged access security strategy.
Reserve Your Place
“The attacker went to excellent lengths to be untraceable by using an open up data-sharing service to host the Python payload, adapting the fileless execution strategy to Python, and compiling an XMRig miner to embed its config to keep away from touching the disk or using a revealing command line,” the researchers explained.
The progress will come as Sysdig thorough a new attack campaign mounted by a menace actor known as SCARLETEEL that involves the abuse of AWS infrastructure to steal proprietary knowledge and conduct illicit crypto mining.
Identified this short article interesting? Follow us on Twitter and LinkedIn to read additional exclusive content we put up.
Some parts of this article are sourced from:
thehackernews.com

 Microsoft Releases Patches for 132 Vulnerabilities, Including 6 Under Active Attack
Microsoft Releases Patches for 132 Vulnerabilities, Including 6 Under Active Attack