Cybersecurity scientists have unearthed a novel rootkit signed by Microsoft which is engineered to connect with an actor-managed attack infrastructure.
Development Micro has attributed the exercise cluster to the very same actor that was formerly recognized as guiding the FiveSys rootkit, which came to light-weight in Oct 2021.
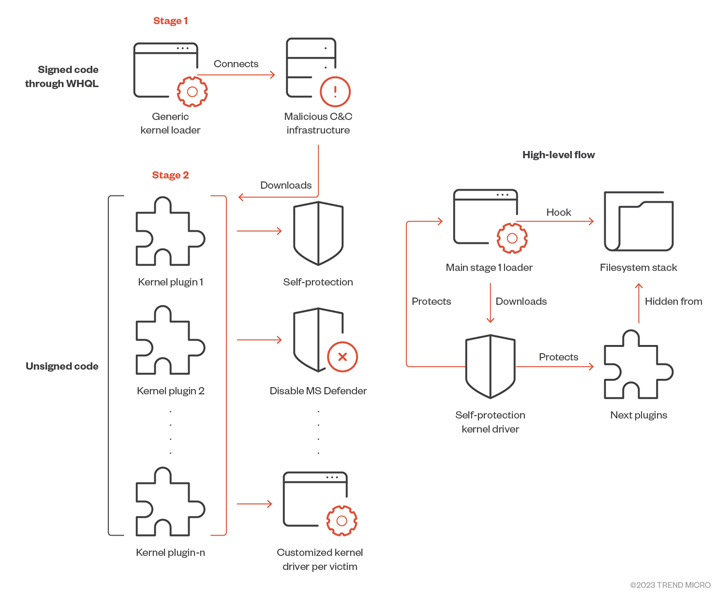
“This malicious actor originates from China and their main victims are the gaming sector in China,” Craze Micro’s Mahmoud Zohdy, Sherif Magdy, and Mohamed Fahmy explained. Their malware appears to be to have handed through the Windows Hardware Quality Labs (WHQL) approach for getting a valid signature.
A number of variants of the rootkit spanning 8 distinctive clusters have been found, with 75 this kind of motorists signed utilizing Microsoft’s WHQL application in 2022 and 2023.
Development Micro’s evaluation of some of the samples has uncovered the existence of debug messages in the resource code, indicating that the operation is continue to in the improvement and tests stage.
In subsequent measures, the initially-stage driver disables the Person Account Manage (UAC) and Secure Desktop manner by modifying the registry and initializes Winsock Kernel (WSK) objects for initiating network interaction with the remote server.
It further more periodically polls the server to retrieve much more payloads and load them straight into memory immediately after decoding and decrypting the acquired data, properly performing as a stealthy kernel driver loader that can bypass detections.
“The major binary functions as a universal loader that enables the attackers to right load a 2nd-stage unsigned kernel module,” the scientists spelled out. “Every second-stage plug-in is personalized to the target machine it can be deployed on, with some containing even a tailor made compiled driver for every single device. Every single plug-in has a unique established of steps to be carried out from the kernel place.”
The plug-ins, for their section, arrive with unique capabilities to achieve persistence, disarm Microsoft Defender Antivirus, and deploy a proxy on the device and redirect web searching traffic to a distant proxy server.
Considerably like FiveSys, the new rootkit detections have been confined solely to China. One particular of the suspected entry points for these infections is reported to be a trojanized Chinese match, mirroring Cisco Talos’ discovery of a destructive driver referred to as RedDriver.
The conclusions dovetail with other stories from Cisco Talos and Sophos about the use of Microsoft-signed malicious kernel-mode drivers for write-up-exploitation things to do, with Chinese-speaking menace actors applying open-supply software well known in just the video clip sport cheat development local community to bypass limits enforced by the tech giant.
Approaching WEBINARShield Versus Insider Threats: Learn SaaS Security Posture Administration
Nervous about insider threats? We have bought you coated! Sign up for this webinar to take a look at realistic procedures and the secrets of proactive security with SaaS Security Posture Management.
Be part of These days
As lots of as 133 destructive motorists signed with legitimate electronic certificates have been uncovered, 81 of which are capable of terminating antivirus alternatives on victims’ systems. The remaining drivers are rootkits created to covertly monitor delicate information despatched more than the internet.
The reality that these motorists are signed by the Windows Hardware Compatibility Application (WHCP) suggests that attackers can put in them on breached methods without boosting any alerts and carry on to carry out malicious action pretty much unimpeded.
“Simply because drivers typically converse with the ‘core’ of the operating program and load before security software program, when they are abused, they can be especially effective at disabling security protections – especially when signed by a dependable authority,” Christopher Budd, director of threat analysis at Sophos X-Ops, explained.
Microsoft, in response to the disclosures, said it has carried out blocking protections and suspended the partners’ vendor accounts concerned in the incident to safeguard customers from potential threats.
If nearly anything, the enhancement paints a photograph of an evolving attack vector that’s currently being actively employed by adversaries to obtain privileged entry to Windows equipment and sidetep detection by security program.
“Malicious actors will keep on to use rootkits to hide destructive code from security resources, impair defenses, and fly under the radar for prolonged durations of time,” the scientists said. “These rootkits will see weighty use from sophisticated teams that have both of those the competencies to reverse-engineer very low-stage system parts and the necessary means to acquire this sort of equipment.”
Observed this write-up intriguing? Follow us on Twitter and LinkedIn to read additional exclusive content we put up.
Some parts of this article are sourced from:
thehackernews.com


 Python-Based PyLoose Fileless Attack Targets Cloud Workloads for Cryptocurrency Mining
Python-Based PyLoose Fileless Attack Targets Cloud Workloads for Cryptocurrency Mining