Nowadays, companies facial area a assortment of security troubles like cyber assaults, compliance necessities, and endpoint security administration. The menace landscape constantly evolves, and it can be too much to handle for enterprises to continue to keep up with the most current security trends. Security groups use procedures and security options to control these worries. These alternatives consist of firewalls, antiviruses, details reduction avoidance solutions, and XDRs (Extended Detection and Response).
Wazuh is a cost-free and open resource security system that unifies XDR and SIEM (System Data and Party Administration) abilities. It contains a common security agent for party knowledge collection from different resources and the central elements for party analysis, correlation, and alerting. The central components consist of the Wazuh server, dashboard, and indexer. Wazuh delivers a suite of modules capable of delivering prolonged danger detection and reaction for on-premises and cloud workloads.
In this report, we emphasize the capabilities of Wazuh that are effective to your organization’s security desires.
Threat intelligence
Wazuh contains the MITRE ATT&CK module with risk detection guidelines out-of-the-box. The MITRE ATT&CK module offers facts that let risk hunters to recognize adversary methods, strategies, and strategies (TTPs). These include things like facts this kind of as the risk groups, computer software, and mitigation actions. You can use this details to slim down threats or compromised endpoints in your atmosphere. Wazuh menace detection rules are mapped versus their corresponding MITRE ATT&CK IDs.
 Fig 1: Wazuh MITRE ATT&CK dashboard
Fig 1: Wazuh MITRE ATT&CK dashboard
Wazuh integrates seamlessly with third-get together risk intelligence alternatives like VirusTotal, MISP, URLHaus, and YARA. These integrations empower the examining of file hashes, IP addresses, and URLs in opposition to acknowledged destructive indicators of compromise (IOCs). Wazuh integration with these answers improves your business’ overall security posture by giving additional insights on likely threats, malicious things to do, and IOCs.
A Vulnerability is a security weak spot or flaw that can be exploited by threats to perform destructive activities in a laptop or computer process. Wazuh provides the Vulnerability Detector module to assist businesses detect and prioritize vulnerabilities in their environments. This module employs facts from multiple feeds such as Canonical, Microsoft, the Countrywide Vulnerability Databases (NVD), and much more to offer true-time information and facts about vulnerabilities.
Threat detection and response
Wazuh uses its modules, decoders, ruleset, and integration with third-get together alternatives to detect and shield your electronic assets from threats. These threats incorporate malware, web, network assaults, and a lot more.
The Wazuh File Integrity Checking module monitors directories and studies file addition, deletion, and modifications. It is utilized to audit delicate files but can be put together with other integrations to detect malware. The rootcheck module is applied to detect rootkit behaviors like concealed documents, ports, and strange processes. The Wazuh lively response module provides automatic reaction steps these as quarantining contaminated techniques, blocking network website traffic, or terminating the ransomware procedures. The mixture of these modules enables for a rapid response to mitigate the effects of cyberattacks.
The picture underneath illustrates the combination of the FIM module, VirusTotal integration, and the active reaction module in detecting and responding to malware downloaded on a monitored endpoint.
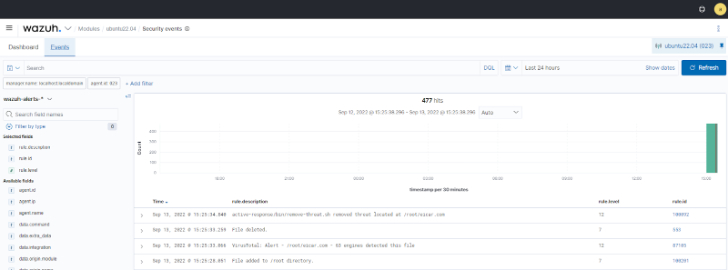 Fig 2: Destructive file detected and deleted from a monitored endpoint
Fig 2: Destructive file detected and deleted from a monitored endpoint
Audit and regulatory compliance
Security auditing and compliance are two crucial principles for any enterprise that aims to shield itself from cyber attacks. Security auditing is the systematic approach of analyzing an organization’s information systems, practices, and procedures to recognize vulnerabilities, evaluate dangers, and make sure that security controls purpose as meant. Regulatory compliance refers to the procedure of certifying that an business adheres to a set of set up criteria, restrictions, or laws connected to information security.
Wazuh will help corporations go security audits and meet up with regulatory compliance prerequisites. Compliance requirements present a established of recommendations and best treatments to promise the safety of an organization’s devices, network, and information. Adhering to these criteria allows lower the probability of a security breach. Wazuh has a variety of modules that help satisfy compliance benchmarks like PCI DSS, GDPR, NIST, and many others. The publish Applying the Wazuh SIEM and XDR system to meet up with PCI DSS compliance reveals how Wazuh performs an critical position in preserving PCI compliance for your business. The image below reveals a Wazuh NIST dashboard.
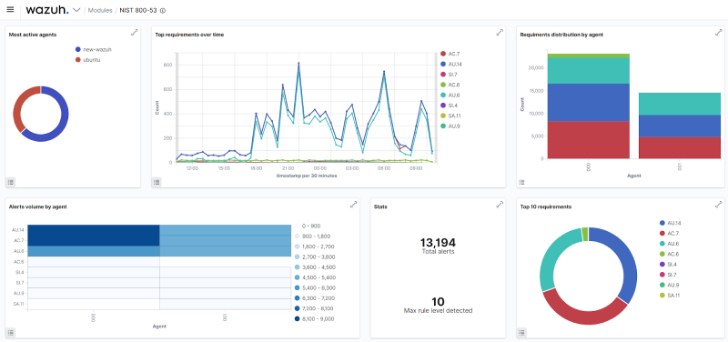 Fig 3: The Wazuh NIST dashboard
Fig 3: The Wazuh NIST dashboard
Cloud security
Cloud platforms provide solutions that manage computing, storage, and networking operations via the Internet. Companies are greatly adopting these cloud platforms simply because of their easy entry to resources, flexibility, and superior scalability. As extra organizations leverage the use of the cloud, protecting the security of their digital belongings continues to be critical.
Wazuh is a unified XDR and SIEM platform that supplies visibility and security checking for cloud environments. It displays and shields cloud products and services running on Amazon Web Services, Microsoft Azure, and Google Cloud System. It achieves this by collecting and analyzing security function knowledge from several cloud components. These information makes it possible for Wazuh to accomplish vulnerability detection, cloud compliance checks, security checking, and automated responses to detected threats.
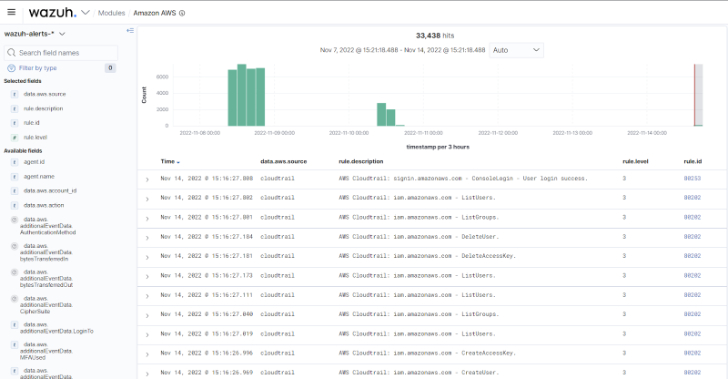 Fig 4: Wazuh monitoring the AWS CloudTrail service
Fig 4: Wazuh monitoring the AWS CloudTrail service
Endpoint hardening
The Wazuh SCA module performs configuration assessments on techniques and applications, making certain the host is secure and the vulnerability surface is decreased. Wazuh uses coverage files to scan endpoints for misconfigurations and vulnerabilities. These coverage documents are included out-of-the-box and based mostly on the Middle for Internet Security (CIS) benchmark. The SCA scan results offer perception into the vulnerabilities present on a monitored endpoint. These vulnerabilities variety from configuration flaws to installed vulnerable variations of the applications and companies. Failed security checks are shown alongside their remediation, supplying process administrators a quick resolution pathway.
 Fig 5: Failed SCA check and remediation for a WordPress installation
Fig 5: Failed SCA check and remediation for a WordPress installation
Open source
Wazuh has a quick-developing local community in which customers, developers, and contributors can request questions about the platform and share collaborative strategies. The Wazuh neighborhood offers users with absolutely free assist, means, and documentation.
Wazuh, as an open up supply security platform, gives quick flexibility and customization. Buyers can modify the resource code to accommodate their certain needs or increase new attributes and capabilities. The Wazuh source code is publicly obtainable on the Wazuh GitHub repository for consumers that may possibly want to complete verification checks or contributions.
Summary
Wazuh is a no cost and open resource system with sturdy XDR and SIEM capabilities. With abilities these types of as log information investigation, file integrity checking, intrusion detection, and automated reaction, Wazuh gives organizations the capacity to speedily and properly respond to security incidents.
Located this write-up exciting? Adhere to us on Twitter and LinkedIn to study more exclusive content we submit.
Some parts of this article are sourced from:
thehackernews.com


 CISA Warns of 5 Actively Exploited Security Flaws: Urgent Action Required
CISA Warns of 5 Actively Exploited Security Flaws: Urgent Action Required