In this report, we will supply a short overview of Silverfort’s system, the 1st (and presently only) unified id security platform on the market place. Silverfort’s patented technology aims to secure corporations from id-centered attacks by integrating with present identity and accessibility administration methods, such as Ad (Active Listing) and cloud-based services, and extending safe access controls like Risk-Based mostly Authentication and MFA (Multi-Issue Authentication) to all their assets. This incorporates on-prem and cloud methods, legacy devices, command-line equipment and service accounts.
A recent report by Silverfort and Osterman Research discovered that 83% of businesses around the world have expert info breaches owing to compromised qualifications. Lots of corporations confess that they are underprotected from identification-dependent assaults, this kind of as lateral motion and ransomware. Resources like command-line accessibility tools and legacy units, which are greatly made use of, are significantly hard to safeguard.
Finding Commenced: Applying the Dashboard
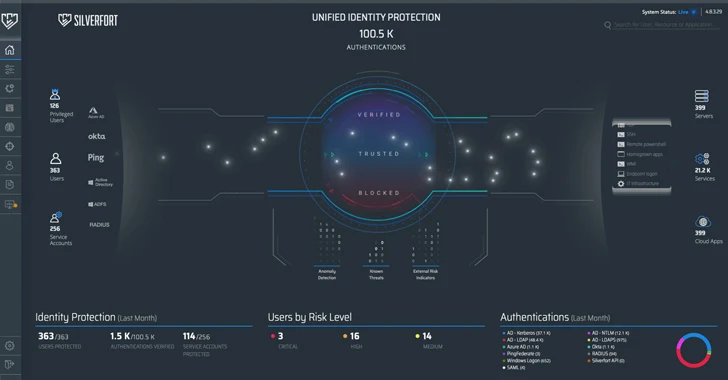
Beneath is a screenshot of Silverfort’s dashboard (figure 1). Over-all, it has a quite intuitive person interface. On the remaining is a list of consumer forms: privileged buyers, typical users, and provider accounts, and how they obtain resources: by on-prem and cloud-centered directories (Advert, Azure Advertisement, Okta), federation servers (Ping, ADFS), and VPN connections (RADIUS). The right facet of the monitor displays a list of the distinct useful resource sorts customers attempt to obtain. The accessibility makes an attempt are represented by glowing dots.
This exhibit showcases the platform’s exceptional differentiator – it really is the only option now that is capable of integrating with the total id infrastructure in the hybrid surroundings. With this integration in area, the unique on-prem and cloud directories forward every single authentication and accessibility try to Silverfort for evaluation and verdict no matter whether to let access or deny. In that method, true time defense for any consumer and useful resource is obtained, as we’ll before long see in extra detail.
The dashboard also exhibits aggregations of precious identification-associated information: amount of authentication tries by protocols and directories, proportion of confirmed authentications, number of consumers and support accounts properly protected, and a breakdown of consumers by risk stage (medium, substantial, critical).
The platform contains many modules with every single a single addressing a distinctive identification defense issue. We’ll now take a look at two of them: Sophisticated MFA and Company Account Protection.
Shielding Means with Superior MFA
MFA has verified to be a single of the most successful ways to guard from id-dependent assaults. Having said that, having MFA security on all network property is quite challenging.
MFA ordinarily relies on brokers and proxies, which signifies some computers will hardly ever be coated by it. Possibly simply because your network is also massive to have proxies on each individual one computer, or mainly because not all computers are capable of installing agents.
Want to see Silverfort in motion? Timetable a no cost demo with our crew of authorities currently!
Also, command-line accessibility equipment, these types of as PsExec, PowerShell, and WMI, despite becoming greatly made use of by network admins, do not natively guidance MFA. These and other on-prem authentications are managed by Advertisement, but Advertisement authentication protocols (Kerberos, NTLM) were being simply just not designed for MFA, and attackers know that. Advert only checks no matter whether usernames and passwords match, so attackers applying reputable qualifications (which might or may well not be compromised) can access the network and launch lateral motion and ransomware attacks devoid of Ad realizing. Silverfort’s important advantage is that it can actually enforce MFA on all of these, something other alternatives cannot.
On the plan screen (determine 2) you can check out current policies or make new ones.
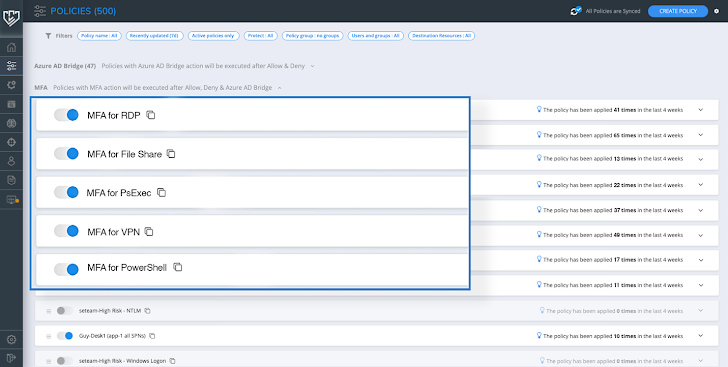 Determine 2: Plan display
Determine 2: Plan display
Creating a new coverage appears quite intuitive, as viewed in determine 3. We need to have to establish the authentication type, the appropriate protocols, what people, sources, and destinations the policy addresses, and the action expected. What occurs in this article is in fact fairly easy, but shockingly intelligent. Advert sends all authentication and entry requests to Silverfort. For each request, Silverfort analyzes its risk and associated procedures to decide no matter if MFA is needed or not. Relying on the verdict, the user is granted accessibility, blocked, or requested to offer MFA. In other words, the policy fundamentally bypasses the inherent limitations of more mature protocols and enforces MFA on them.
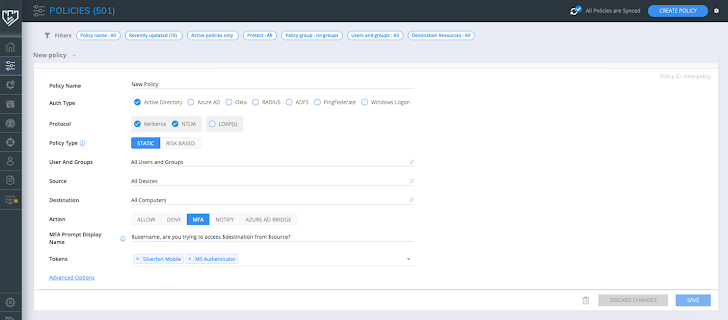 Figure 3: Developing a policy
Figure 3: Developing a policy
Exploring and Securing Service Accounts
Service accounts are a critical security obstacle because of to their high access privileges and lower to zero visibility. Also, services accounts usually are not people, so MFA is not an option, and so is password rotation with PAM, which might crash critical procedures if their logins fail. In simple fact, all businesses have various services accounts, from time to time as lots of as 50% of their in general people, and lots of of them go unmonitored. That’s why attackers appreciate compromised support accounts- they can use them for lateral motion less than the radar and achieve accessibility to a big quantity of machines with out becoming found.
Determine 4 shows the Company Accounts display. As Silverfort receives all authentication and accessibility requests, it is in a position to identify assistance accounts by examining repetitive equipment behaviors.
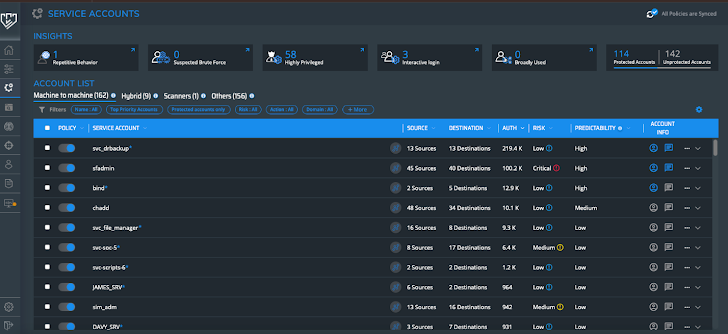 Determine 4: Provider Accounts monitor
Determine 4: Provider Accounts monitor
It seems like we have 162 accounts under machine-to-device. We can filter them centered on a range of parameters. Predictability, for illustration, actions recurring obtain to the identical supply or desired destination. Deviations from this sample can indicate destructive activity.
In determine 5, we can see supplemental data about our services accounts, these kinds of as resources, locations, risk indicators, privilege concentrations, and usage.
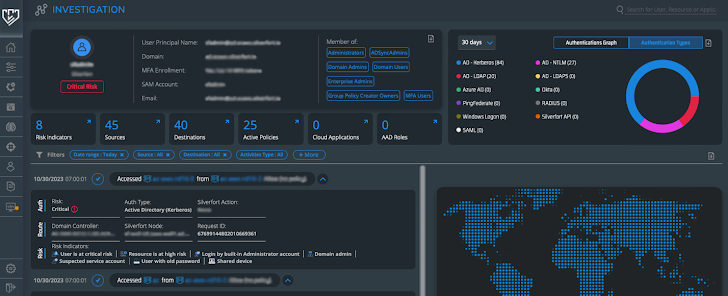 Determine 5: Support account Investigation screen
Determine 5: Support account Investigation screen
For just about every provider account, policies are mechanically created centered on its behavior. All we have to do is select involving ‘alert’, ‘block’ and ‘alert to SIEM’, and empower the plan (determine 6).
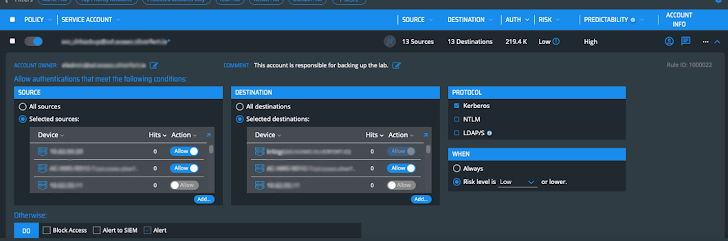 Determine 6: Provider account insurance policies
Determine 6: Provider account insurance policies
Ultimate Feelings
Silverfort’s system actually achieves its intention of unified identification defense. Its ability to enforce MFA on practically any source (this kind of as command-line equipment, legacy apps, file shares, and several other folks) and create insurance policies in seconds is unparalleled. Getting total visibility into all service accounts and finally being in a position to safeguard them is exceptionally important. To conclude, Silverfort’s system gives ground breaking identification security abilities that are getting to be more and more required each individual working day.
Observed this posting intriguing? Observe us on Twitter and LinkedIn to browse much more distinctive content material we article.
Some parts of this article are sourced from:
thehackernews.com

 Why Defenders Should Embrace a Hacker Mindset
Why Defenders Should Embrace a Hacker Mindset