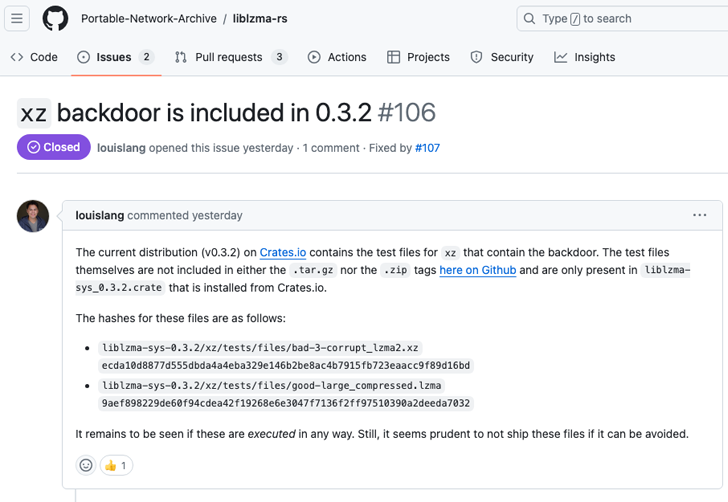
“Take a look at information” linked with the XZ Utils backdoor have produced their way to a Rust crate known as liblzma-sys, new findings from Phylum reveal.
liblzma-sys, which has been downloaded in excess of 21,000 periods to date, offers Rust developers with bindings to the liblzma implementation, an underlying library that is aspect of the XZ Utils details compression application. The impacted version in issue is .3.2.
“The recent distribution (v0.3.2) on Crates.io consists of the test information for XZ that contain the backdoor,” Phylum noted in a GitHub issue lifted on April 9, 2024.
“The take a look at information themselves are not incorporated in both the .tar.gz nor the .zip tags below on GitHub and are only present in liblzma-sys_.3.2.crate that is mounted from Crates.io.”
Following liable disclosure, the information in concern (“exams/files/poor-3-corrupt_lzma2.xz” and “assessments/information/great-massive_compressed.lzma”) have considering the fact that been removed from liblzma-sys version .3.3 released on April 10. The former edition of the crate has been pulled from the registry.

“The destructive tests information were committed upstream, but thanks to the malicious build guidance not remaining present in the upstream repository, they were by no means referred to as or executed,” Snyk reported in an advisory of its own.
The backdoor in XZ Utils was identified in late March when Microsoft engineer Andres Freund determined malicious commits to the command-line utility impacting variations 5.6. and 5.6.1 launched in February and March 2024, respectively. The popular package deal is built-in into lots of Linux distributions.
The code commits, built by a now-suspended GitHub person named JiaT75 (aka Jia Tan), essentially built it possible to circumvent authentication controls within SSH to execute code remotely, potentially allowing for the operators to get in excess of the technique.
“The over-all compromise spanned in excess of two many years,” SentinelOne researchers Sarthak Misraa and Antonio Pirozzi claimed in an evaluation published this 7 days. “Less than the alias Jia Tan, the actor started contributing to the xz venture on Oct 29, 2021.”
“Initially, the commits were innocuous and minimal. Nevertheless, the actor progressively became a more energetic contributor to the undertaking, steadily gaining name and rely on within just the neighborhood.”
In accordance to Russian cybersecurity corporation Kaspersky, the trojanized modifications just take the variety of a multi-stage operation.
“The supply code of the build infrastructure that produced the closing packages was somewhat modified (by introducing an additional file establish-to-host.m4) to extract the up coming stage script that was concealed in a check case file (undesirable-3-corrupt_lzma2.xz),” it explained.
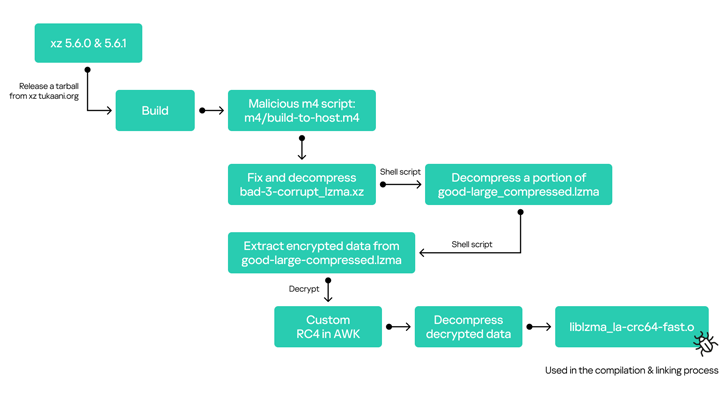
“These scripts in switch extracted a malicious binary component from another test case file (great-significant_compressed.lzma) that was linked with the reputable library throughout the compilation course of action to be delivered to Linux repositories.”
The payload, a shell script, is dependable for the extraction and the execution of the backdoor, which, in flip, hooks into unique features – RSA_community_decrypt, EVP_PKEY_established1_RSA, and RSA_get0_vital – that will let it to keep an eye on each and every SSH relationship to the contaminated device.
The major target of the backdoor slipped into liblzma is to manipulate Protected Shell Daemon (sshd) and check for commands sent by an attacker at the start off of an SSH session, effectively introducing a way to accomplish remote code execution.

Although the early discovery of the backdoor averted what could have been a popular compromise of the Linux ecosystem, the enhancement is as soon as once more a sign that open up-resource bundle maintainers are becoming targeted by social engineering strategies with the target of staging program provide chain assaults.
In this scenario, it materialized in the variety of a coordinated activity that presumably showcased quite a few sockpuppet accounts that orchestrated a force campaign aimed at forcing the project’s longtime maintainer to bring on board a co-maintainer to include far more characteristics and tackle issues.
“The flurry of open source code contributions and relevant tension strategies from earlier unfamiliar developer accounts indicates that a coordinated social engineering campaign making use of phony developer accounts was applied to sneak destructive code into a broadly used open up-resource undertaking,” ReversingLabs reported.
SentinelOne scientists discovered that the refined code variations made by JiaT75 between versions 5.6. and 5.6.1 advise that the modifications were engineered to boost the backdoor’s modularity and plant more malware.
As of April 9, 2024, the resource code repository affiliated with XZ Utils has been restored on GitHub, nearly two weeks after it was disabled for a violation of the firm’s phrases of assistance.
The attribution of the procedure and the meant targets are now not known, even though in mild of the setting up and sophistication behind it, the menace actor is suspected to be a state-sponsored entity.
“It is obvious that this backdoor is very elaborate and employs complex techniques to evade detection,” Kaspersky mentioned.
Observed this post fascinating? Adhere to us on Twitter and LinkedIn to read through far more exceptional written content we put up.
Some parts of this article are sourced from:
thehackernews.com


 Code Keepers: Mastering Non-Human Identity Management
Code Keepers: Mastering Non-Human Identity Management