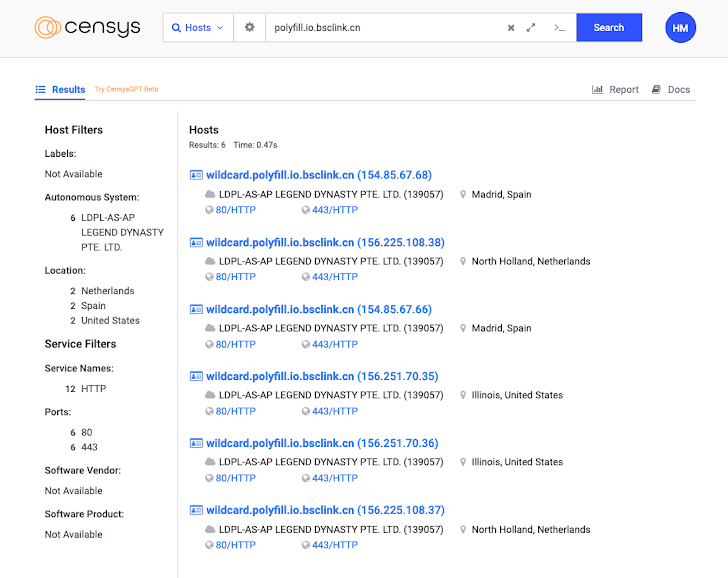
The provide chain attack targeting widely-utilised Polyfill[.]io JavaScript library is broader in scope than beforehand considered, with new conclusions from Censys exhibiting that above 380,000 hosts are embedding a polyfill script linking to the malicious domain as of July 2, 2024.
This consists of references to “https://cdn.polyfill[.]io” or “https://cdn.polyfill[.]com” in their HTTP responses, the attack area administration company stated.
“Around 237,700, are situated inside the Hetzner network (AS24940), mainly in Germany,” it noted. “This is not shocking – Hetzner is a preferred web hosting provider, and quite a few website developers leverage it.”
Further more evaluation of the influenced hosts has uncovered domains tied to prominent corporations like WarnerBros, Hulu, Mercedes-Benz, and Pearson that reference the malicious endpoint in problem.

Aspects of the attack emerged in late June 2024 when Sansec alerted that code hosted on the Polyfill domain had been modified to redirect consumers to grownup- and gambling-themed web sites. The code adjustments ended up designed these kinds of that the redirections only took put at sure occasions of the working day and only versus visitors who achieved sure criteria.
The nefarious actions is mentioned to have been released after the area and its associated GitHub repository ended up marketed to a Chinese corporation named Funnull in February 2024.
The development has due to the fact prompted area registrar Namecheap to suspend the domain, information shipping and delivery networks these types of as Cloudflare to immediately replace Polyfill hyperlinks with domains main to alternate risk-free mirror internet sites, and Google to block ads for web-sites embedding the area.
While the operators tried to relaunch the service less than a distinctive area named polyfill[.]com, it was also taken down by Namecheap as of June 28, 2024. Of the two other domains registered by them given that the begin of July – polyfill[.]internet site and polyfillcache[.]com –the latter remains up and operating.
On leading of that, a extra considerable network of perhaps related domains, which includes bootcdn[.]net, bootcss[.]com, staticfile[.]net, staticfile[.]org, unionadjs[.]com, xhsbpza[.]com, union.macoms[.]la, newcrbpc[.]com, has been uncovered as tied to the maintainers of Polyfill, indicating that the incident might be portion of a broader destructive marketing campaign.

“1 of these domains, bootcss[.]com, has been noticed participating in malicious things to do that are pretty equivalent to the polyfill[.]io attack, with evidence dating back again to June 2023,” Censys famous, introducing it found 1.6 million public-experiencing hosts that hyperlink to these suspicious domains.
“It would not be totally unreasonable to contemplate the probability that the same malicious actor responsible for the polyfill.io attack might exploit these other domains for identical functions in the future.”
The progress arrives as WordPress security company Patchstack warned of cascading hazards posed by the Polyfill offer chain attack on web pages working the articles administration method (CMS) by dozens of legitimate plugins that url to the rogue area.
Discovered this report appealing? Stick to us on Twitter and LinkedIn to read through a lot more unique information we write-up.
Some parts of this article are sourced from:
thehackernews.com


 New Golang-Based Zergeca Botnet Capable of Powerful DDoS Attacks
New Golang-Based Zergeca Botnet Capable of Powerful DDoS Attacks