The malware acknowledged as GootLoader proceeds to be in lively use by danger actors wanting to deliver more payloads to compromised hosts.
“Updates to the GootLoader payload have resulted in various variations of GootLoader, with GootLoader 3 at this time in energetic use,” cybersecurity agency Cybereason said in an assessment posted last week.
“Though some of the particulars of GootLoader payloads have transformed over time, an infection techniques and total performance continue to be related to the malware’s resurgence in 2020.”

GootLoader, a malware loader portion of the Gootkit banking trojan, is connected to a menace actor named Hive0127 (aka UNC2565). It abuses JavaScript to download post-exploitation resources and is distributed via search engine optimization (Search engine optimisation) poisoning methods.
It usually serves as a conduit for offering many payloads this kind of as Cobalt Strike, Gootkit, IcedID, Kronos, REvil, and SystemBC.

In latest months, the threat actors powering GootLoader have also unleashed their have command-and-manage (C2) and lateral movement tool dubbed GootBot, indicating that the “team is increasing their market to obtain a wider audience for their monetary gains.”
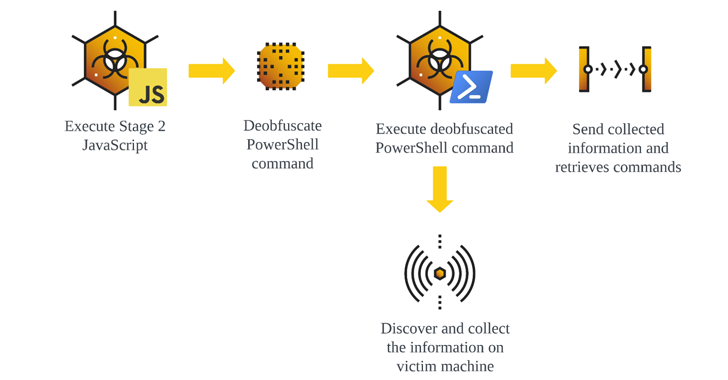
Attack chains involve compromising sites to host the GootLoader JavaScript payload by passing it off as authorized documents and agreements, which, when introduced, sets up persistence working with a scheduled endeavor and executes additional JavaScript to kick-start off a PowerShell script for accumulating system facts and awaiting further more recommendations.

“Web sites that host these archive data files leverage Lookup Engine Optimization (Seo) poisoning techniques to lure in victims that are hunting for business-connected files this kind of as agreement templates or lawful files,” security scientists Ralph Villanueva, Kotaro Ogino, and Gal Romano stated.
The assaults are also notable for making use of supply code encoding, command movement obfuscation, and payload size inflation in get to resist evaluation and detection. An additional technique involves embedding the malware in genuine JavaScript library files like jQuery, Lodash, Maplace.js, and tui-chart.
“GootLoader has received many updates for the duration of its lifetime cycle, such as improvements to evasion and execution functionalities,” the researchers concluded.
Observed this post intriguing? Comply with us on Twitter and LinkedIn to go through extra unique articles we post.
Some parts of this article are sourced from:
thehackernews.com

 Polyfill[.]io Attack Impacts Over 380,000 Hosts, Including Major Companies
Polyfill[.]io Attack Impacts Over 380,000 Hosts, Including Major Companies