As quite a few as 100 malicious artificial intelligence (AI)/device finding out (ML) styles have been found out in the Hugging Confront platform.
These consist of circumstances wherever loading a pickle file leads to code execution, computer software supply chain security business JFrog claimed.
“The model’s payload grants the attacker a shell on the compromised device, enabling them to achieve complete handle over victims’ devices by way of what is typically referred to as a ‘backdoor,'” senior security researcher David Cohen said.
“This silent infiltration could perhaps grant accessibility to critical interior methods and pave the way for big-scale details breaches or even corporate espionage, impacting not just unique end users but most likely overall corporations across the world, all while leaving victims totally unaware of their compromised condition.”

Particularly, the rogue design initiates a reverse shell link to 210.117.212[.]93, an IP address that belongs to the Korea Investigation Environment Open up Network (KREONET). Other repositories bearing the identical payload have been noticed connecting to other IP addresses.
In just one situation, the authors of the design urged people not to obtain it, boosting the possibility that the publication may perhaps be the get the job done of scientists or AI practitioners.
“Even so, a essential principle in security investigate is refraining from publishing authentic performing exploits or destructive code,” JFrog mentioned. “This principle was breached when the destructive code tried to link back to a legitimate IP handle.”
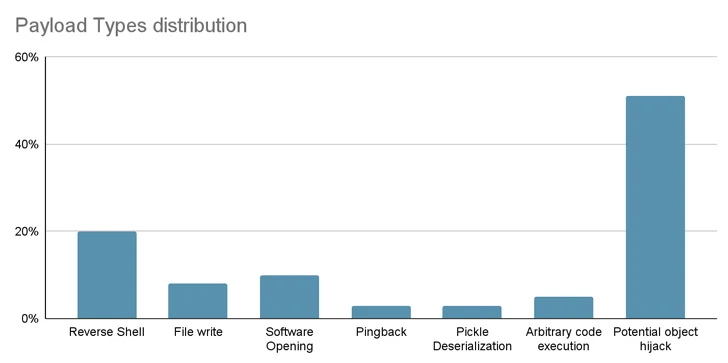
The findings when once again underscore the risk lurking within open up-supply repositories, which could be poisoned for nefarious activities.
From Source Chain Dangers to Zero-click on Worms
They also occur as scientists have devised efficient strategies to deliver prompts that can be utilised to elicit harmful responses from large-language designs (LLMs) using a procedure referred to as beam look for-centered adversarial attack (BEAST).
In a relevant progress, security scientists have produced what’s regarded as a generative AI worm called Morris II that’s able of stealing knowledge and spreading malware through several units.
Morris II, a twist on 1 of the oldest laptop or computer worms, leverages adversarial self-replicating prompts encoded into inputs such as visuals and text that, when processed by GenAI versions, can induce them to “replicate the input as output (replication) and engage in destructive actions (payload),” security scientists Stav Cohen, Ron Bitton, and Ben Nassi said.
Even extra troublingly, the versions can be weaponized to provide malicious inputs to new purposes by exploiting the connectivity within the generative AI ecosystem.

The attack strategy, dubbed ComPromptMized, shares similarities with regular methods like buffer overflows and SQL injections owing to the simple fact that it embeds the code within a question and information into areas recognized to hold executable code.
ComPromptMized impacts programs whose execution flow is reliant on the output of a generative AI provider as perfectly as individuals that use retrieval augmented technology (RAG), which combines textual content era types with an information retrieval part to enrich query responses.

The research is not the initially, nor will it be the very last, to check out the idea of prompt injection as a way to attack LLMs and trick them into accomplishing unintended actions.
Formerly, teachers have shown assaults that use visuals and audio recordings to inject invisible “adversarial perturbations” into multi-modal LLMs that trigger the design to output attacker-selected textual content or recommendations.
“The attacker may possibly entice the sufferer to a webpage with an intriguing picture or deliver an email with an audio clip,” Nassi, alongside with Eugene Bagdasaryan, Tsung-Yin Hsieh, and Vitaly Shmatikov, claimed in a paper printed late final 12 months.
“When the victim straight inputs the picture or the clip into an isolated LLM and asks issues about it, the product will be steered by attacker-injected prompts.”
Early past year, a team of researchers at Germany’s CISPA Helmholtz Heart for Data Security at Saarland College and Sequire Technology also uncovered how an attacker could exploit LLM versions by strategically injecting hidden prompts into knowledge (i.e., oblique prompt injection) that the design would likely retrieve when responding to consumer enter.
Found this short article fascinating? Comply with us on Twitter and LinkedIn to go through far more unique articles we submit.
Some parts of this article are sourced from:
thehackernews.com

 Phobos Ransomware Aggressively Targeting U.S. Critical Infrastructure
Phobos Ransomware Aggressively Targeting U.S. Critical Infrastructure