Targets positioned in Azerbaijan have been singled out as component of a new campaign that’s developed to deploy Rust-dependent malware on compromised programs.
Cybersecurity business Deep Intuition is tracking the procedure beneath the name Operation Rusty Flag. It has not been affiliated with any known menace actor or team.
“The procedure has at minimum two distinct original accessibility vectors,” security scientists Simon Kenin, Ron Ben Yizhak, and Mark Vaitzman mentioned in an examination printed final week. “A single of the lures utilized in the operation is a modified doc that was made use of by the Storm-0978 team. This could be a deliberate ‘false flag.'”

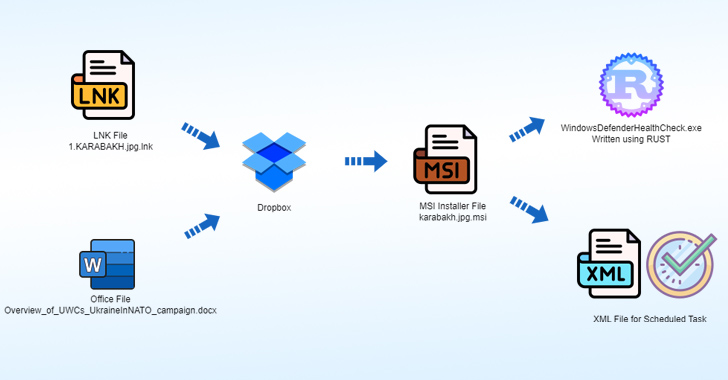
The attack chain leverages an LNK file named 1.KARABAKH.jpg.lnk as a launchpad to retrieve a 2nd-phase payload, an MSI installer, hosted on Dropbox.
The installer file, for its portion, drops an implant created in Rust, an XML file for a scheduled activity to execute the implant, and a decoy image file that capabilities watermarks of the symbol of the Azerbaijan Ministry of Defense.
An alternate infection vector is a Microsoft Place of work doc named “Overview_of_UWCs_UkraineInNATO_marketing campaign.docx,” which exploits CVE-2017-11882, a six-calendar year-previous memory corruption vulnerability in Microsoft Office’s Equation Editor, to invoke a Dropbox URL hosting a different MSI file serving a variant of the same Rust backdoor.
The use of Overview_of_UWCs_UkraineInNATO_marketing campaign.docx is noteworthy, as a lure with the identical filename was leveraged by Storm-0978 (aka RomCom, Tropical Scorpius, UNC2596, and Void Rabisu) in the latest cyber attacks focusing on Ukraine that exploit an Business remote code execution flaw (CVE-2023-36884).
Approaching WEBINARIdentity is the New Endpoint: Mastering SaaS Security in the Fashionable Age
Dive deep into the upcoming of SaaS security with Maor Bin, CEO of Adaptive Shield. Uncover why identification is the new endpoint. Secure your spot now.
Supercharge Your Skills
“This action seems to be like a deliberate phony flag endeavor to pin this attack on Storm-0978,” the scientists explained.
The Rust backdoor, one of which masquerades as “WinDefenderHealth.exe,” arrives fitted with capabilities to collect details from the compromised host and deliver it to an attacker-managed server.
The exact finish targets of the campaign continue to be unclear at this phase. At the exact time, the chance that it could be a crimson team exercising has not been discounted.
“Rust is starting to be extra popular between malware authors,” the researchers stated. “Security merchandise are not nonetheless detecting Rust malware precisely, and the reverse engineering course of action is far more elaborate.”
Observed this report attention-grabbing? Stick to us on Twitter and LinkedIn to browse a lot more exclusive content material we put up.
Some parts of this article are sourced from:
thehackernews.com

 Inside the Code of a New XWorm Variant
Inside the Code of a New XWorm Variant