Indian govt entities and the protection sector have been qualified by a phishing marketing campaign that’s engineered to drop Rust-centered malware for intelligence gathering.
The action, very first detected in October 2023, has been codenamed Procedure RusticWeb by organization security firm SEQRITE.
“New Rust-based mostly payloads and encrypted PowerShell commands have been used to exfiltrate confidential paperwork to a web-centered services motor, in its place of a devoted command-and-handle (C2) server,” security researcher Sathwik Ram Prakki said.
Tactical overlaps have been uncovered amongst the cluster and people greatly tracked underneath the monikers Clear Tribe and SideCopy, the two of which are assessed to be joined to Pakistan.
SideCopy is also a suspected subordinate factor inside of Clear Tribe. Very last month, SEQRITE thorough a number of strategies undertaken by the threat actor focusing on Indian governing administration bodies to provide various trojans such as AllaKore RAT, Ares RAT, and DRat.
Upcoming WEBINAR Conquer AI-Powered Threats with Zero Believe in – Webinar for Security Gurus
Standard security steps is not going to minimize it in modern environment. It really is time for Zero Rely on Security. Safe your data like never right before.
Be part of Now
Other modern attack chains documented by ThreatMon have employed decoy Microsoft PowerPoint files as properly as specially crafted RAR archives prone to CVE-2023-38831 for malware shipping, enabling unbridled remote accessibility and command.
“The SideCopy APT Group’s infection chain will involve various ways, each very carefully orchestrated to guarantee productive compromise,” ThreatMon observed previously this year.
The most up-to-date established of assaults commences with a phishing email, leveraging social engineering procedures to trick victims into interacting with destructive PDF data files that fall Rust-dependent payloads for enumerating the file program in the history while exhibiting the decoy file to the victim.
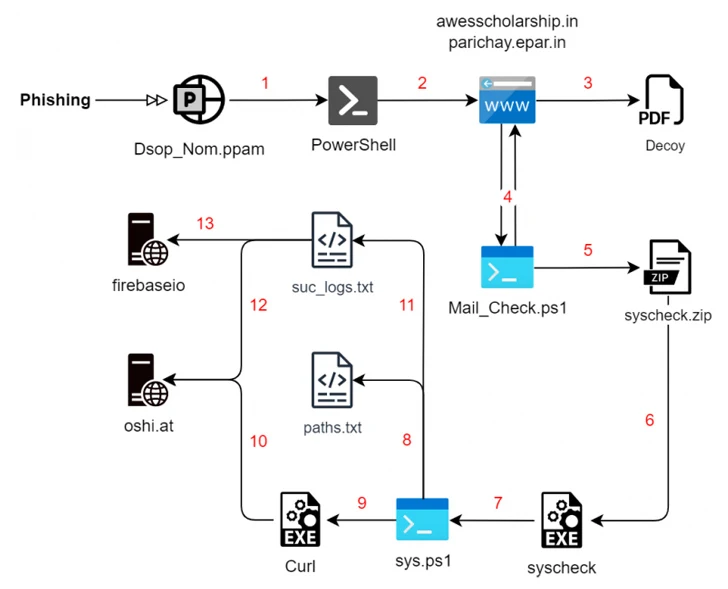
Moreover amassing information of fascination, the malware is equipped to acquire procedure information and transmit them to the C2 server but lacks the features of other innovative stealer malware offered in the cybercrime underground.
A second an infection chain determined by SEQRITE in December employs a very similar multi-phase system but substitutes the Rust malware with a PowerShell script that can take treatment of the enumeration and exfiltration measures.
But in an appealing twist, the ultimate-phase payload is launched by way of a Rust executable that goes by the identify “Cisco AnyConnect Web Helper.” The gathered data is in the long run uploaded to oshi[.]at domain, an anonymous general public file-sharing engine referred to as OshiUpload.
“Procedure RusticWeb could be linked to an APT threat as it shares similarities with a variety of Pakistan-linked groups,” Ram Prakki stated.

The disclosure will come just about two months just after Cyble uncovered a malicious Android application used by the DoNot Group targeting men and women in the Kashmir area of India.
The country-condition actor, also identified by the names APT-C-35, Origami Elephant, and SECTOR02, is believed to be of Indian origin and has a history of employing Android malware to infiltrate equipment belonging to people in Kashmir and Pakistan.
The variant examined by Cyble is a trojanized version of an open-supply GitHub venture named “QuranApp: Examine and Take a look at” that will come equipped with a vast variety of adware options to report audio and VoIP phone calls, capture screenshots, collect details from numerous apps, down load further APK files, and observe the victim’s area.
“The DoNot group’s relentless initiatives to refine their equipment and tactics underscore the ongoing risk they pose, notably in their targeting of people in the sensitive Kashmir area of India,” Cyble mentioned.
Uncovered this report attention-grabbing? Abide by us on Twitter and LinkedIn to browse far more exclusive written content we publish.
Some parts of this article are sourced from:
thehackernews.com

 Decoy Microsoft Word Documents Used to Deliver Nim-Based Malware
Decoy Microsoft Word Documents Used to Deliver Nim-Based Malware