A new phishing marketing campaign is leveraging decoy Microsoft Term documents as bait to deliver a backdoor written in the Nim programming language.
“Malware created in unusual programming languages places the security group at a drawback as researchers and reverse engineers’ unfamiliarity can hamper their investigation,” Netskope researchers Ghanashyam Satpathy and Jan Michael Alcantara explained.
Nim-primarily based malware has been a rarity in the menace landscape, while that has been slowly but surely changing in modern many years as attackers proceed to possibly produce custom equipment from scratch making use of the language or port present variations of their nefarious plans to it.
This has been demonstrated in the case of loaders these as NimzaLoader, Nimbda, IceXLoader, as well as ransomware families tracked underneath the names Dark Power and Kanti.
The attack chain documented by Netskope begins with a phishing email that contains a Word document attachment that, when opened, urges the receiver to allow macros to activate the deployment of the Nim malware. The email sender disguises themselves as a Nepali federal government official.
When released, the implant is liable for enumerating working procedures to figure out the existence of acknowledged analysis instruments on the infected host and instantly terminate by itself need to it find 1.
Forthcoming WEBINAR Conquer AI-Driven Threats with Zero Trust – Webinar for Security Pros
Common security actions is not going to slice it in present-day entire world. It really is time for Zero Have confidence in Security. Protected your details like by no means prior to.
Be part of Now
In any other case, the backdoor establishes connections with a remote server that mimics a federal government domain from Nepal, such as the Nationwide Info Technology Middle (NITC) and awaits even more recommendations. The command-and-control (C2) servers are no lengthier obtainable –
- mail[.]mofa[.]govnp[.]org
- nitc[.]govnp[.]org
- mx1[.]nepal[.]govnp[.]org
- dns[.]govnp[.]org
“Nim is a statically typed compiled programming language,” the scientists mentioned. “Aside from its common syntax, its cross-compilation functions permit attackers to produce 1 malware variant and have it cross-compiled to focus on different platforms.”
The disclosure comes as Cyble discovered a social engineering campaign that leverages messages on social media platforms to deliver a new Python-dependent stealer malware called Editbot Stealer that’s designed to harvest and exfiltrate worthwhile info by using an actor-controlled Telegram channel.
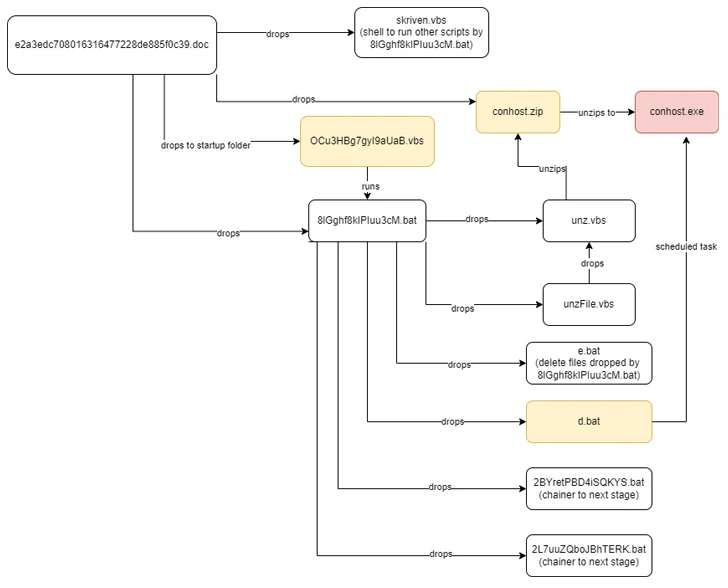
Even as threat actors are experimenting with new malware strains, phishing strategies have also been noticed distributing known malware these types of as DarkGate and NetSupport RAT by way of email and compromised internet websites with pretend update lures (aka RogueRaticate), significantly these from a cluster dubbed BattleRoyal.
Organization security organization Proofpoint stated it discovered at minimum 20 strategies that made use of DarkGate malware concerning September and November 2023, in advance of switching to NetSupport RAT before this month.
Just one attack sequence identified in early October 2023 notably stands out for chaining two website traffic supply programs (TDSs) – 404 TDS and Keitaro TDS – to filter and redirect victims meeting their standards to an actor-operated domain hosting a payload that exploited CVE-2023-36025 (CVSS rating: 8.8), a substantial-severity Windows SmartScreen security bypass that was addressed by Microsoft in November 2023.

This indicates BattleRoyal weaponized this vulnerability as a zero-day a thirty day period just before it was publicly uncovered by the tech huge.
DarkGate is intended to steal details and down load additional malware payloads, although NetSupport RAT, which started off off as a bona fide remote administration resource, has metamorphosed into a strong weapon wielded by malevolent actors to infiltrate systems and create unfettered distant control.
“Cybercriminal danger actors [are] adopting new, diverse, and significantly creative attack chains – which includes the use of many TDS equipment – to empower malware shipping and delivery,” Proofpoint stated.
“Additionally, the use of the two email and bogus update lures exhibits the actor applying several varieties of social engineering procedures in an attempt to get users to set up the final payload.”
DarkGate has also been place to use by other risk actors like TA571 and TA577, both of which are known to disseminate a wide range of malware, which include AsyncRAT, NetSupport, IcedID, PikaBot, and QakBot (aka Qbot).
“TA577 for illustration, one of the most distinguished Qbot distributors, returned to email danger details in September to supply DarkGate malware and has considering the fact that been noticed delivering PikaBot in strategies that usually have tens of 1000’s of messages,” Selena Larson, senior danger intelligence analyst at Proofpoint, informed The Hacker News.
Uncovered this article intriguing? Comply with us on Twitter and LinkedIn to go through extra exceptional information we post.
Some parts of this article are sourced from:
thehackernews.com

 UAC-0099 Using WinRAR Exploit to Target Ukrainian Firms with LONEPAGE Malware
UAC-0099 Using WinRAR Exploit to Target Ukrainian Firms with LONEPAGE Malware