Pick out Ukrainian government networks have remained contaminated with a malware named OfflRouter considering the fact that 2015.
Cisco Talos claimed its findings are dependent on an examination of more than 100 private paperwork that have been infected with the VBA macro virus and uploaded to the VirusTotal malware scanning system.
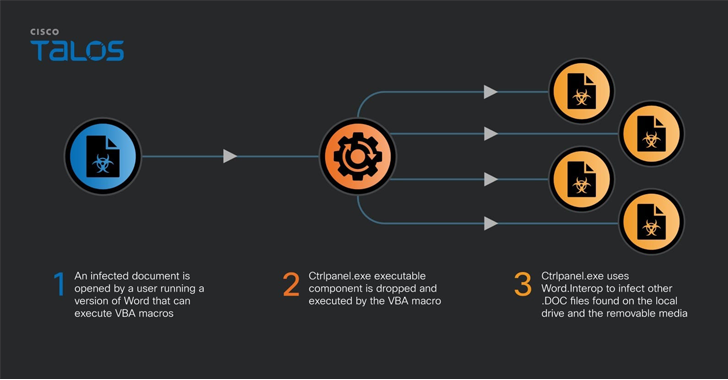
“The files contained VBA code to fall and operate an executable with the name ‘ctrlpanel.exe,'” security researcher Vanja Svajcer said. “The virus is however energetic in Ukraine and is causing probably private paperwork to be uploaded to publicly available doc repositories.”
A striking element of OfflRouter is its inability to unfold via email, necessitating that it be propagated by way of other indicates, these kinds of as sharing files and removable media, together with USB memory sticks containing the contaminated files.
These design and style possibilities, intentional or if not, are said to have confined the unfold of OfflRouter in Ukraine’s borders and to a number of organizations, so escaping detection for practically 10 a long time.

It can be presently not known who is dependable for the malware and there are no indications that it was made by someone from Ukraine.
Whoever it is, they have been described as ingenious yet inexperienced owing to the strange propagation system and the existence of many mistakes in the supply code.
OfflRouter has been formerly highlighted by MalwareHunterTeam as early as May perhaps 2018 and once again by the Computer Security Incident Reaction Workforce Slovakia (CSIRT.SK) in August 2021, detailing contaminated paperwork uploaded to the Nationwide Police of Ukraine’s internet site.
The modus operandi has remained just about unchanged, with the VBA macro-embedded Microsoft Term documents dropping a .NET executable named “ctrlpanel.exe,” which then infects all documents with the .DOC (not .DOCX) extension identified on the system and other removable media with the exact same macro.
“The an infection iterates through a checklist of the document candidates to infect and takes advantage of an innovative method to check out the document infection marker to stay clear of various an infection procedures – the operate checks the doc generation metadata, provides the creation times, and checks the price of the sum,” Svajcer reported.
“If the sum is zero, the document is thought of by now infected.”
That reported, the attack gets effective only when VBA macros are enabled. Microsoft, as of July 2022, has been blocking macros by default in Business files downloaded from the internet, prompting menace actors to seek out other initial obtain pathways.
A different key functionality of the malware is to make Windows Registry modifications so as to be certain that the executable operates each and every time upon booting the technique.
“The virus targets only files with the filename extension .DOC, the default extension for the OLE2 documents, and it will not try to infect other filename extensions,” Svajcer elaborated. “The default Phrase document filename extension for the much more modern Term variations is .DOCX, so couple documents will be contaminated as a outcome.”

That’s not all. Ctrlpanel.exe is also geared up to look for for likely plugins (with the extension .ORP) existing on detachable drives and execute them on the device, which implies the malware is anticipating the plugins to be shipped through USB drives or CD-ROMs.
A single the opposite, if the plugins are previously existing on a host, OfflRouter will take care of encoding them, copying the documents to the root folder of the hooked up detachable media with the filename extension .ORP, and manipulating them to make them concealed so that they are not visible by means of the File Explorer when plugging them into yet another product.
That reported, one particular key unknown is no matter whether the preliminary vector is a doc or the executable module ctrlpanel.exe.
“The edge of the two-module virus is that it can be unfold as a standalone executable or as an infected doc,” Svajcer stated.
“It could even be advantageous to in the beginning unfold as an executable as the module can run standalone and established the registry keys to let execution of the VBA code and switching of the default saved file formats to .DOC in advance of infecting documents. That way, the an infection might be a little bit stealthier.”
Found this write-up interesting? Stick to us on Twitter and LinkedIn to go through more exclusive material we article.
Some parts of this article are sourced from:
thehackernews.com


 FIN7 Cybercrime Group Targeting U.S. Auto Industry with Carbanak Backdoor
FIN7 Cybercrime Group Targeting U.S. Auto Industry with Carbanak Backdoor